Headline
CVE-2021-44480: «Doctor Web discovered vulnerabilities in children’s smart watches
Wokka Lokka Q50 devices through 2021-11-30 allow remote attackers (who know the SIM phone number and password) to listen to a device’s surroundings via a callback in an SMS command, as demonstrated by the 123456 and 523681 default passwords.
November 30, 2021
Parents always strive to take care of their children. Technology innovations help them reach this goal, through various wearables like smartwatches and GPS trackers. More and more models of these devices are getting close to smartphones in functionality. For example, many of them can track the child’s location and travel route. These devices can also make and answer phone and video calls, receive SMS and voicemail, take pictures, and listen to the surroundings. It is even possible to enable the remote control of the device. Doctor Web has analyzed the potential threats that such gadgets can pose to parents and their children.
During their daily operation, these devices collect and transmit data to the manufacturer’s servers and make it available to parents through their personal accounts. The information obtained with smartwatches is very sensitive. If malicious actors get their hands over such information, it can put children in great danger.
To understand the vulnerability and dangers of children’s smartwatches, Doctor Web’s specialists analyzed several popular models: Elari Kidphone 4G, Wokka Lokka Q50, Elari FixiTime Lite, and Smart Baby Watch Q19. We chose models based on public popularity ratings for the Russian market, and purposefully selected models from different price ranges. We purchased all smartwatches anonymously from a large Russian online store.
We carried out both static and dynamic analyses during the inspection: we searched for potential implants in the software and possible undocumented features, as well as checked network activity, transmitted data, and how it was secured.
****Elari Kidphone 4G Smartwatch****
Several versions of the Elari Kidphone 4G watches exist. They are based on different hardware platforms but they all run an Android OS and their firmware differs slightly.
The analysis has demonstrated that the remote server the watch transmits data to is located outside of Russia which may pose a potential threat. The main threat of this model, however, comes from installed software. Its firmware has a built-in app for over-the-air updating, and this app has a trojan functionality.
Firstly, the application sends the child’s geolocation data to its own remote server. Secondly, we found a malicious code inside it, which is detected by Dr.Web as Android.DownLoader.3894. Every time the watch turns on or network connection changes, this code launches two malicious modules, Android.DownLoader.812.origin and Android.DownLoader.1049.origin. They connect to the C&C server to transmit various information and to receive commands. By default, the modules connect to the server every 8 hours. Because of this, a high time delay exists between the first connection and the first time the watch turned on.
The Android.DownLoader.812.origin module sends the user’s mobile phone number and SIM card information, geolocation data, and information about the device itself to the C&C server. In response, it can receive commands to change the frequency of requests to the server, update the module, download, install, run and uninstall apps, and load web pages.
The Android.DownLoader.1049.origin module sends SIM card and mobile phone number information, geolocation data, a large number of data about the device and installed apps, as well as the info about the number of SMS, phone calls, and contacts in the phone book to the C&C server.
Thus, Android.DownLoader.3894 hidden in this watch can be used for cyber espionage, displaying ads, and installing unwanted or even malicious apps.
****Wokka Lokka Q50 Smartwatch****
The analysis of network activity on this model did not reveal any suspicious actions. The child’s geolocation data that is collected during watch operation is sent to a remote server located in Russia. At the same time, we did not observe any sensitive information transmitted to third-party servers.
The geolocation data is transmitted to the server without encryption which can pose a potential threat to Wokka Lokka Q50 users. Theoretically, the attackers could hijack unprotected data though a man-in-the-middle attack. However, because the data is transmitted through the mobile operator network, chances of such an attack to occur are not high.
Officially, this watch is controlled through the mobile app installed on the parents’ devices. But Wokka Lokka Q50 can also be controlled through special SMS commands. The watch manual does not list information on alternative control mechanisms, however. Still, it is the way the SMS control mechanism itself is implemented that poses certain risks.
The main vulnerability of Wokka Lokka Q50 is its passwords. In all watches of this model line, the standard 123456 password (523681 password in some versions of the watch) is used to send SMS commands. However, the watch has no functionality to force-change the default password when the device is turned on for the first time. The manual does not have a recommendation to change it; it also cannot be changed through the controlling app.
The only place that mentions the possibility of changing the default password is an online FAQ on the brand’s official site. But users rarely visit these official sites to search for additional info on the devices they bought. Therefore, a significant number of buyers of these watches will not know that the gadget can be controlled through SMS, and they will use the devices with the default password, not realizing that it can and should be changed. This poses a serious threat.
If a malicious third-party knows the watch’s password and SIM phone number, they can easily gain control over the device. For example, they can request GPS location that will be sent in the reply SMS, remotely listen to the surroundings through a callback to a phone number specified in the command, and even change the C&C server address to their own and gain access to all the information the watch collects.
Even if the default password is changed, it will not solve the problem completely. It is true that a password change will make many commands unavailable for the attacker. But they can still execute the command to verify the watch’s status and parameters without any limits, from any phone number. If the attacker uses this command, the watch will send them the current administrator’s phone number, among other data about the device. Knowing this number, the attacker can act on behalf of the administrator (i.e., the parents) and set a new password for the watch and gain complete control over it.
****Elari FixiTime Lite Smartwatch****
During the analysis of the Elari FixiTime Lite smart watch network activity, we did not trace any suspicious activity. However, these watches send data to a C&C server located outside of Russia. Moreover, the information on GPS coordinates is transmitted to the server through the MQTT protocol without encryption, similar to the Wokka Lokka Q50 watch. Also, voicemails and photos are sent through unprotected HTTP protocol. In the case of a successful man-in-the-middle attack, the malicious actors can intercept this data.
The password used to connect to the MQTT protocol to transmit the data is hardcoded in the firmware of the watch, which is another potential danger of this model. If the attacker knows the watch’s IMEI and this password, they can connect to the server and disguise themselves as the attacked device and transmit fake data.
****Smart Baby Watch Q19 Smartwatch****
The analysis of this watch did not reveal suspicious activity or any commands that could possibly lead to the confidential information leak. The watch encrypts the data it sends to the C&C server, and it will be difficult for potential attackers to gain access to this information. However, the C&C server is located outside Russia which poses a potential threat. In addition, this watch also uses the default 123456 password to send control commands. At the same time, the list of available commands is significantly reduced in this model.
****Conclusions****
The performed analysis showed that the security level of children’s smartwatches is quite unsatisfactory. Our research covered several models, but the problem with these devices is that different models can have similar software. For example, a variety of smartwatch models and GPS trackers use firmware similar to the one installed on the Wokka Lokka Q50. They also have standard passwords to control them through SMS. Therefore, their users are facing the same risks as the owners of Wokka Lokka Q50 watches. With that, new models constantly appear on the market, and there is no guarantee that they will have no any vulnerabilities either.
In addition, the discovery of the trojan preinstalled on the Elari Kidphone 4G smart watch clearly demonstrates the danger hidden in Android OS-based devices of this type. Third-party firms often create their firmware, and manufacturers rarely check firmware’s security and integrity. Therefore, it is possible that during the manufacturing stage, malicious actors will plug Android smart watches with trojans or adware.
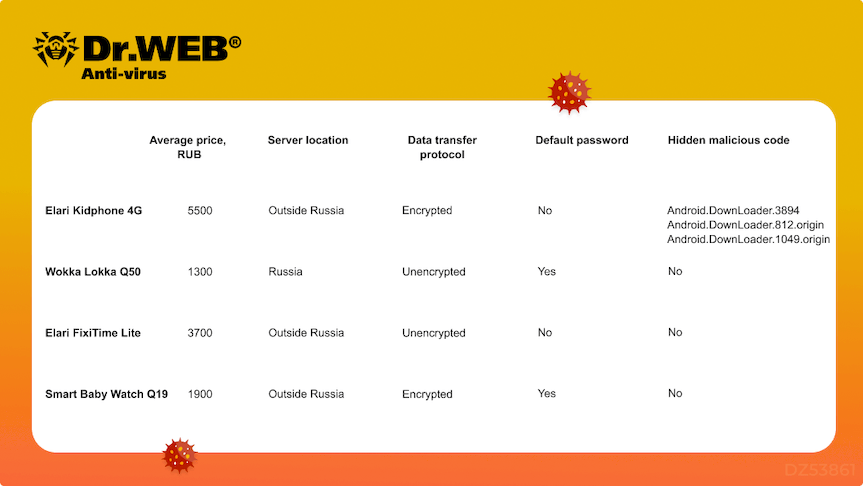
The summary table below shows the main vulnerabilities of the examined smart watches:
Doctor Web has notified the manufacturers of uncovered vulnerabilities.
Smart watches are a convenient and relatively inexpensive way to protect and monitor a child. But they still pose certain risks. They can silently send confidential information to third-party services, execute malicious functionalities, and put children in danger if cybercriminals hack and control these devices.
Parents should be careful when using such devices to monitor their children and must carefully examine possible security risks before making their purchase. Otherwise, the model they choose can do their child more harm than good.
- More details on Android.DownLoader.3894
- More details on Android.DownLoader.812.origin
- More details on Android.DownLoader.1049.origin