Headline
CVE-2022-24110: Secure Managed File Transfer
Kiteworks MFT 7.5 may allow an unauthorized user to reset other users’ passwords. This is fixed in version 7.6 and later.
 Revolutionize MFT
Revolutionize MFT
With a Security-First
ArchitectureInfrastructure managers and enterprise architects responsible for secure managed file transfer (MFT) face new pressures from throughout their organizations. For years, legacy MFT products have transformed custom-scripted transfer projects into scalable, reliable operations. But now, CISOs reeling from surging cyber-attacks mandate deeper defenses, and your Compliance Officer requires even more audits. Meanwhile, the business demands faster turnaround, and qualified staff is harder to find… and keep. Prevail over these challenges with managed file transfer designed from the ground up for simplicity, security, and governance. Easily deploy its virtual appliance cluster—or our hosted service—and configure your policies. Immediately benefit from the security of its hardened vault and built-in defense in depth. Configure trading partner workflows, start operations, and breathe a sigh of relief as your auditors and SOC now see every transaction detail in built-in audit reports, security analytics, and your SIEM.
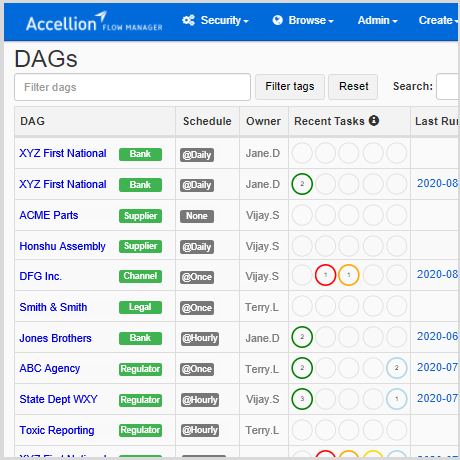
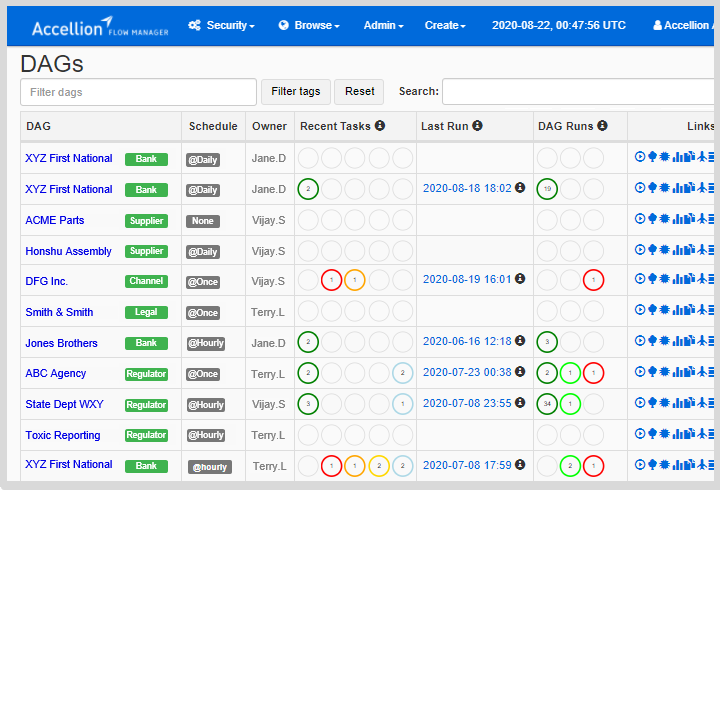
Streamline and Secure Large-Scale File Transfer Operations****Secure MFT Server | Managed File Transfer
- Manage, monitor, and recover transfers with the Secure MFT Server’s graphical operations dashboard.
- Onboard new trading partners and author workflows simply and quickly.
- Trigger transfers with scheduling, polling, or events, or start them manually.
- Maximize end-to-end security with unique vault-to-vault transfers.
- Access data in folders, file shares, repositories, and cloud stores.
Learn more about the Secure MFT Server…
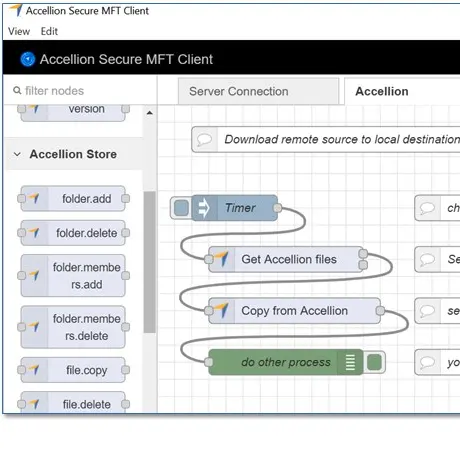
Automate Secure and Flexible Business Processes****Secure MFT Client | Managed File Transfer
- Make departmental file-based processes simple, foolproof, and compliant using the Secure MFT Client.
- Distribute throughout the organization, but manage centrally.
- Author visual workflows without coding.
- Leverage a library of two thousand connectors and workflow functions.
- Utilize content firewall functions.
Learn more about the Secure MFT Client…

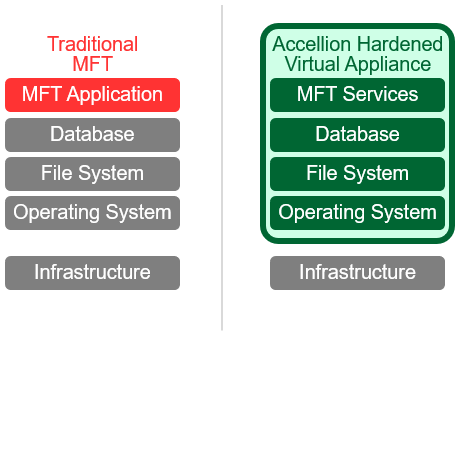
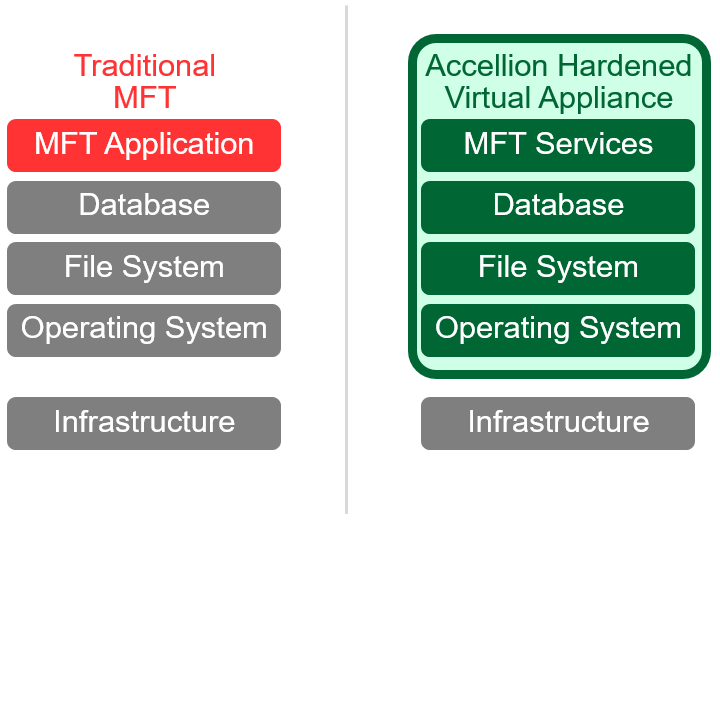
Protect Your Content from Insiders and Advanced Threats****Hardened Virtual Appliance | Managed File Transfer
- The content firewall doesn’t just encrypt protocols and storage, it minimizes your attack surface by enclosing all system components in a hardened virtual appliance.
- It firewalls each server, defaults to most secure settings, shuts off unnecessary ports, removes unnecessary code, and isolates traffic between tiers.
- Kiteworks secure development lifecycle, regular penetration testing, and worldwide bounty program eliminate bugs before they become vulnerabilities.
- Like a smartphone, one button updates all the system components so you never miss a patch.
- Intrusion detection systems detect and alert on suspicious system modifications.
Learn more about content firewall security…
Set Granular Policy Controls to Prevent Compliance Violations****Governance | Secure Managed File Transfer
- More easily meet standards like NIST 800-53, PCI-DSS, and ISO 27001.
- Prevent insider mistakes and attacks with separation of duties and workflow-level access controls, and govern end users with role-based permissions and data access policies.
- Firewall zone-savvy deployments and policies let you control where data and metadata is stored to prevent DMZ exposure.
- Connect and leverage your DLP to block and log sensitive transfers, your ATP to quarantine malware, and your CDR for content disarm and reconstruction.
Learn more about granular policy controls and regulatory compliance


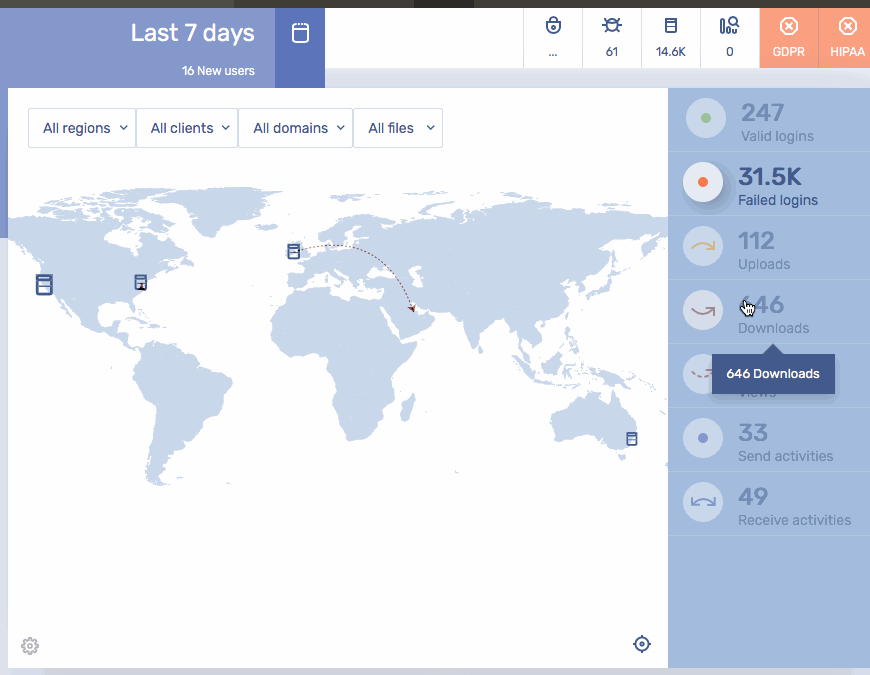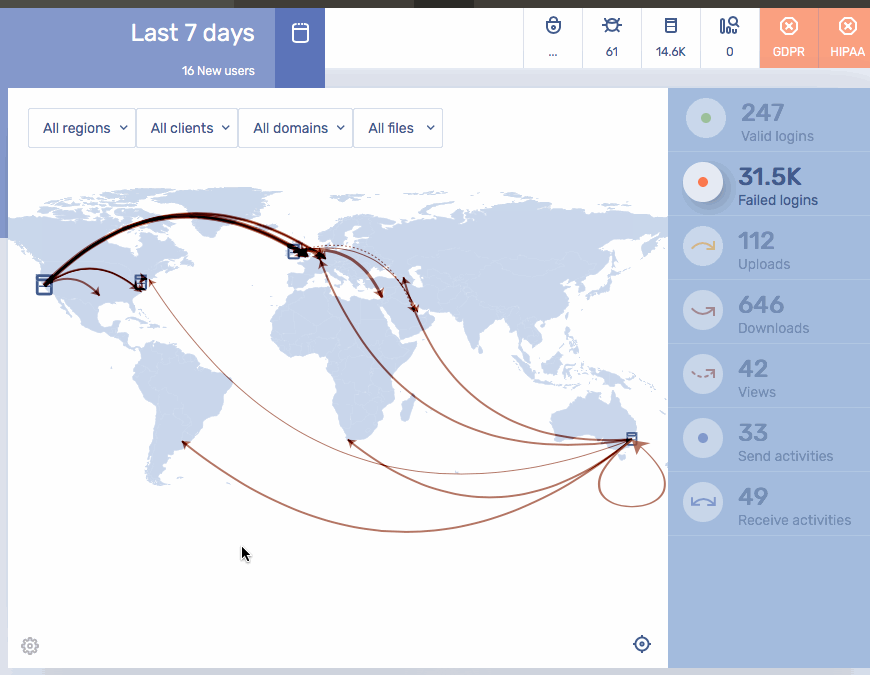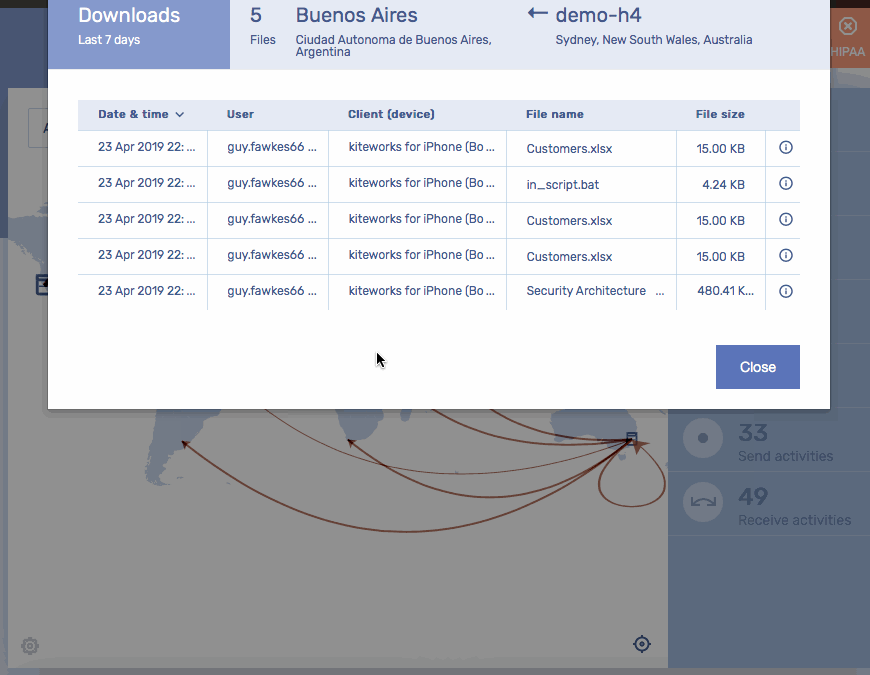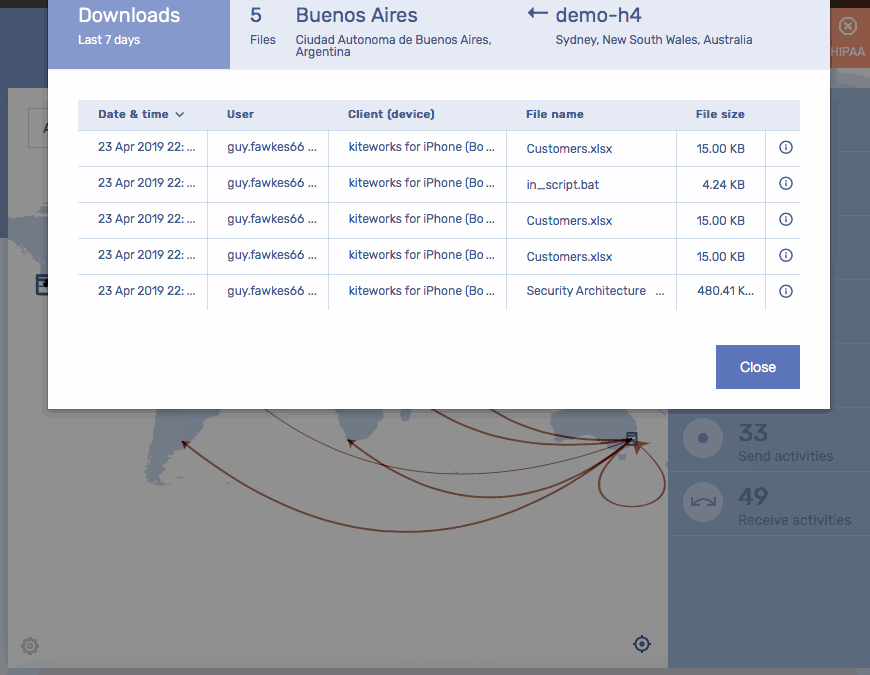

Gain End-to-End Visibility of Content Entering or Leaving the Enterprise****Security Analytics| Secure Managed File Transfer
- Visualize all sensitive information entering and leaving the firm in a standardized log of all transactions covering secure MFT, secure email, secure file sharing, and other content firewall communication channels.
- Understand who’s sending what to whom, when, where and how.
- Detect suspicious activity and take action on anomalies.
- Pass audits and comply with industry regulations.
- Create custom dashboards and reports in your SIEM, or utilize the Kiteworks Splunk App.
Learn more about CISO Dashboard visualization…
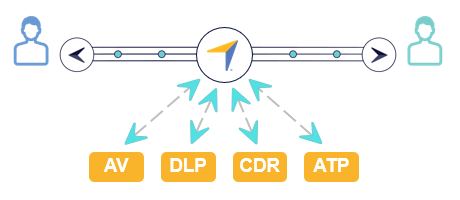
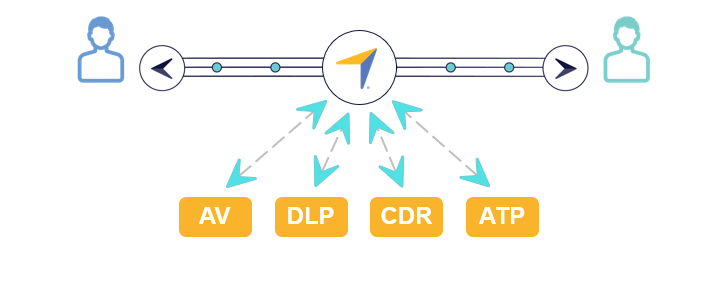
Prevent Leaks and Breaches with AV, DLP, CDR, and ATP****Automated File Scanning | Managed File Transfer
- Detect and quarantine malware in incoming content by scanning through the content firewall’s embedded anti-virus.
- Detect and quarantine unknown threats in incoming content with your Advanced Threat Prevention (ATP) product such as Check Point SandBlast or FireEye Malware Analysis (AX) and Detection on Demand.
- Prevent leaks by scanning outgoing content through your Data Leak Prevention (DLP) product based on your rules for logging and blocking transfers.
- Eliminate malware in incoming content using Content Disarm and Reconstruction (CDR) products like OPSWAT MetaDefender.
Learn more about security integrations…
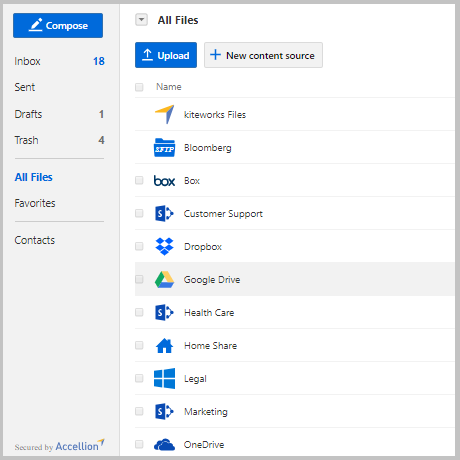

Leverage All Content Firewall Communication Channels****Third Party Communications | Managed File Transfer
- Give business users simple Web or local folders as transfer endpoints.
- Securely access enterprise content in file shares, SharePoint and other on-premise Enterprise Content Management (ECM) systems, and cloud shares such as Microsoft OneDrive and Box.
- Orchestrate secure email communications.
Learn more about unified communication channels
Take control of your sensitive information
FEATURED RESOURCES
Sign up for the latest blog posts and news