Headline
CVE-2022-1316: ZeroTierOne for windows local privilege escalation because of incorrect directory privilege in zerotierone
ZeroTierOne for windows local privilege escalation because of incorrect directory privilege in GitHub repository zerotier/zerotierone prior to 1.8.8. Local Privilege Escalation
Description
When administrators install zerotierone for windows, it will install ZeroTierOneService, the ImagePath of it is C:\ProgramData\ZeroTier\One\zerotier-one_x64.exe,however, the permission of C:\ProgramData\ZeroTier\One\ is incorrect, an attacker with low privilege can get system privilege by this vuln.
Proof of Concept
When administrators install zerotierone for windows, it will install ZeroTierOneService, the ImagePath of it is C:\ProgramData\ZeroTier\One\zerotier-one_x64.exe.
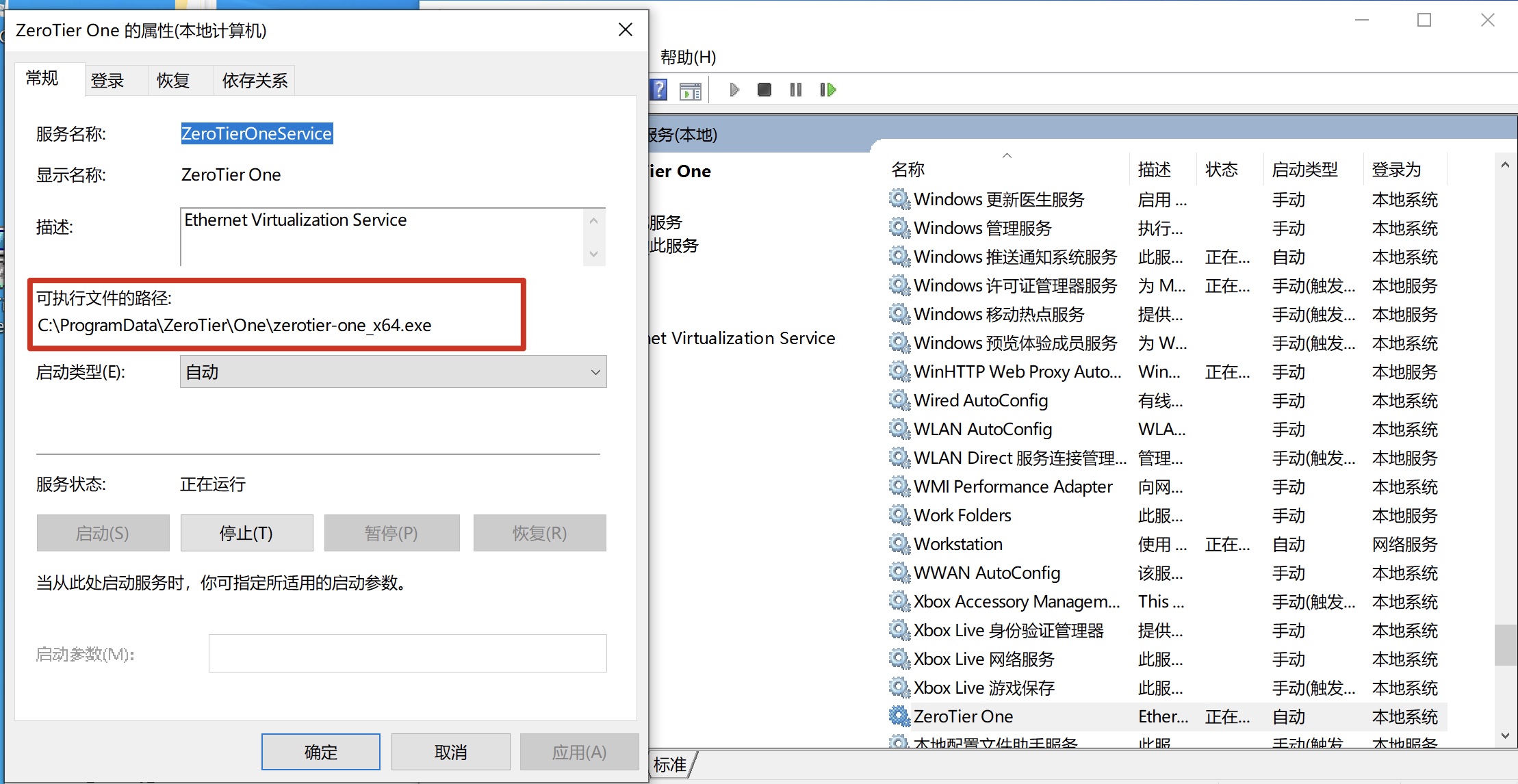
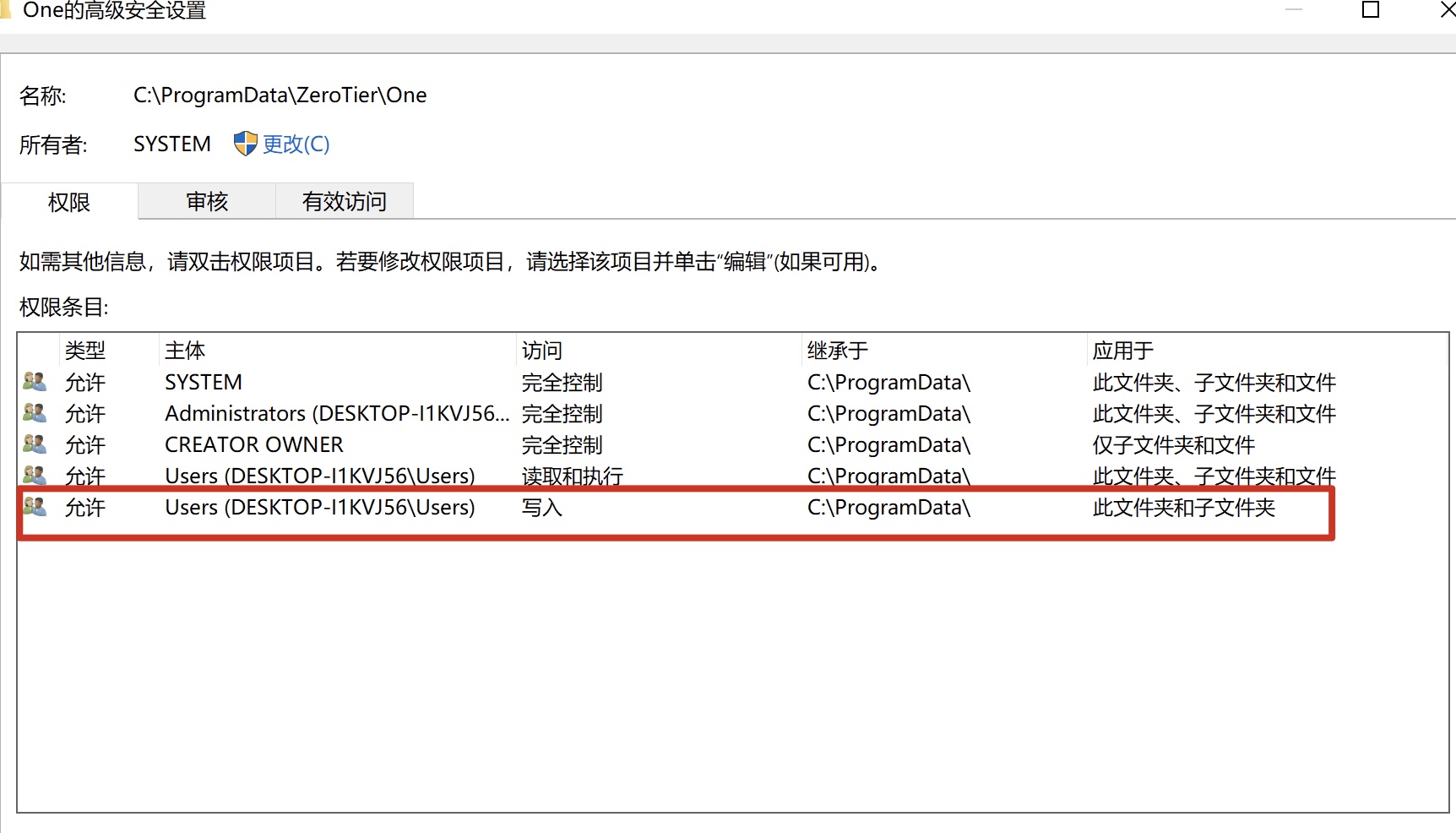
However,the permission of C:\ProgramData\ZeroTier\One\ is incorrect, all Users have write permission of C:\ProgramData\ZeroTier\One and its subdirectories.
When ZeroTierOneService starts, it will try to load some dlls under C:\ProgramData\ZeroTier\One.
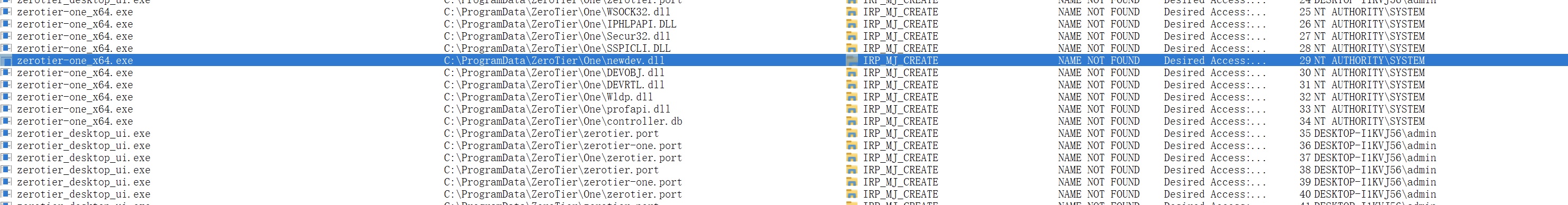
So an attacker with low privilege can exploit it and gain a system privilege by dll hijacking because of ZeroTierOneService running as SYSTEM.
Impact
Local Privilege Escalation