Headline
CVE-2022-28128: File encryption software for both Windows and macOS
Untrusted search path vulnerability in AttacheCase ver.3.6.1.0 and earlier allows an attacker to gain privileges and execute arbitrary code via a Trojan horse DLL in an unspecified directory.
![]()
AttachéCase ( Current Version )****Windows10, 11 / macOS


“AttachéCase4” is a powerful file/folder encryption software that uses the world’s standard encryption algorithm, while focusing on simplicity and ease of use for daily use.
Important Notice(2022/03/30)
A vulnerability in loading DLL was discovered in “AttacheCase4” for Windows. Placing a maliciously modified “dwmapi.dll” in the directory containing the executable file (AttacheCase.exe) may allow arbitrary code to be executed.
This vulnerability have been confirmed in ver. 4.0.2.7 or earlier. If you are using these versions of "AttacheCase4", please update to the latest version as soon as possible.
More information on this vulnerability can be found at the following page.
https://hibara.org/software/attachecase/vulnerability/JVN#10140834
AttacheCase may insecurely load Dynamic Link Libraries
https://jvn.jp/jp/JVN10140834/By countermeasuring of this vulnerability, the previous vulnerability in the older version of the " AttacheCase#3 " is also fixed.
If you are using this version, please update to the latest version as soon as possible.
スポンサー・リンク
Introduction
Encryption is just three steps
Encryption is just three steps. You can easily encrypt files by simply dragging and dropping them, or if you drag and drop the entire folder, it will create one encrypted file (pack the entire folder).
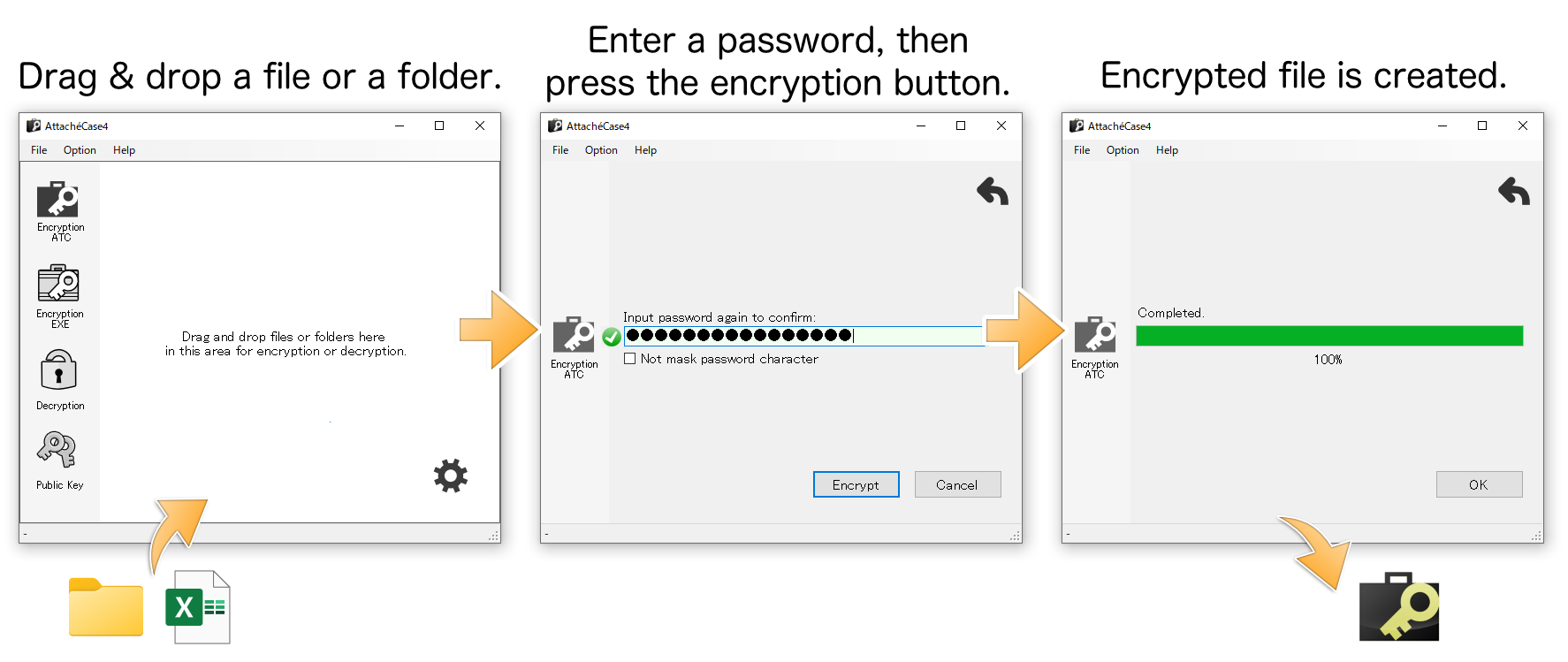
In addition, the data will be compressed during the encryption process, making it compact in size.
Decrypting is also as easy as dragging and dropping, or double-clicking and entering the password to restore the original files and folders.
Output in self-executable format
The encrypted file can also be output as an executable (*.exe) file, so it can be passed to someone who does not have an AttachéCase and can be decrypted.
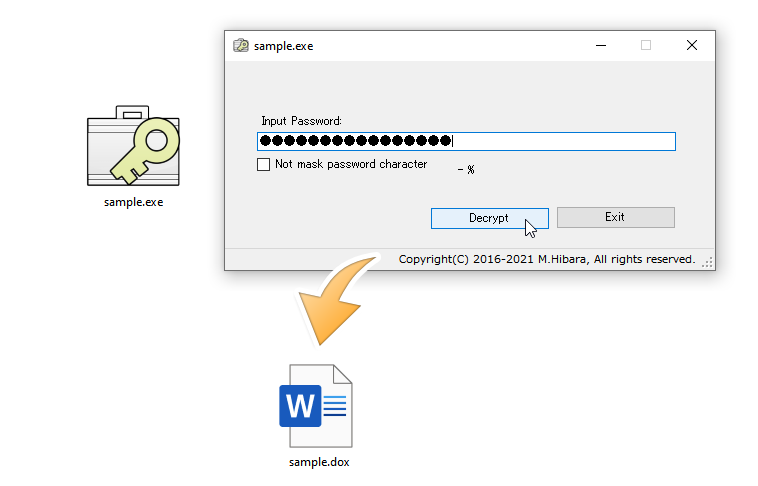
The Mac version cannot output in self-executable format, but it can decrypt executable files (*.exe) generated by the Windows version.
Supports both Windows and macOS
Enables data exchange on Windows and macOS.
At present, the macOS version is inferior to the Windows version in terms of functionality, but as described in the roadmap below, I plan to start supporting both versions in earnest from around .NET6.
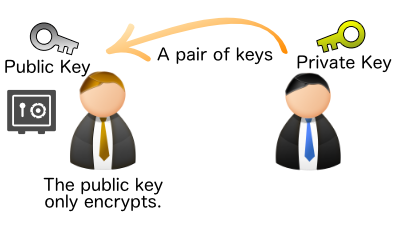
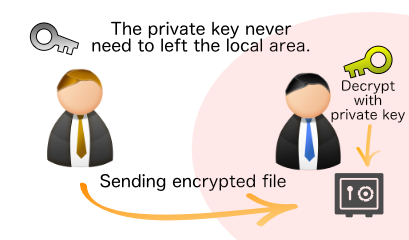
Public key cryptography
From ver.4, public key cryptography (RSA) is also supported. By exchanging public and private keys, it is no longer necessary to exchange ZIP passwords, making it possible to exchange data more securely.
Cryptographic algorithms are global standards
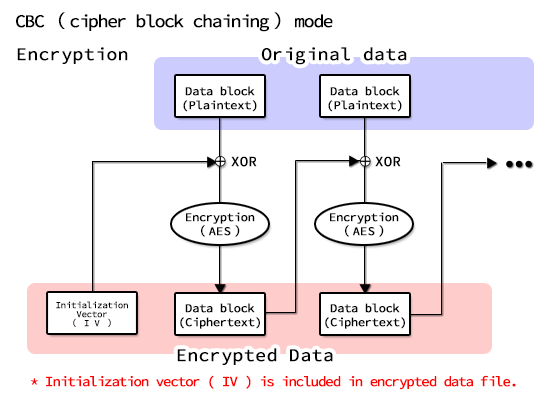
The encryption algorithm is based on the Advanced Encryption Standard (AES), the next-generation encryption standard chosen by the U.S. Government’s National Institute of Standards and Technology (NIST) in October 2000. Also, the encryption mode used is CBC mode.
Key derivation according to RFC2898
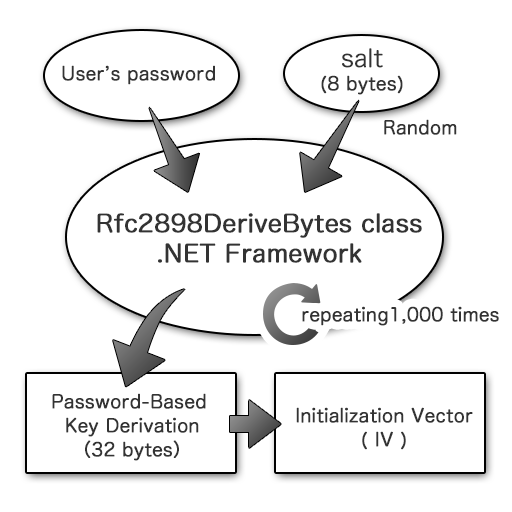
Based on “PKCS #5: Password-Based Cryptography Specification Version 2.0” by RFC2898, the derived key and initialization vector after 1,000 iterations of password-based key derivation mixed with random numbers as salt are output one after another, and each is used as the key and initialization vector for encryption.
New data format (Current version)
Starting from ver.4, a new data format has been introduced, which enables more efficient encryption and decryption based on the know-how accumulated in the development up to ver.3. Note that ver.4 can decrypt data of ver.3 and 2, but ver.3 and 2 cannot decrypt data of ver.4. For details on data formats, please refer to " here ".
The old version is below.
Development Roadmap
A macOS version is also available, but it has limited functionality compared to the Windows version. .NET library used in application will be upgraded in the future, making it a cross-platform application completely that supports both Windows and macOS. Specifically, I will do this over the period from Nov 2021 onward.
Due to the delay in development by Microsoft, it is likely that full cross-platform with Windows and macOS will not be available until the second quarter of 2022 or later . Depending on the development status, it may be possible to release it as a beta version before the end of this year, but the schedule is uncertain.
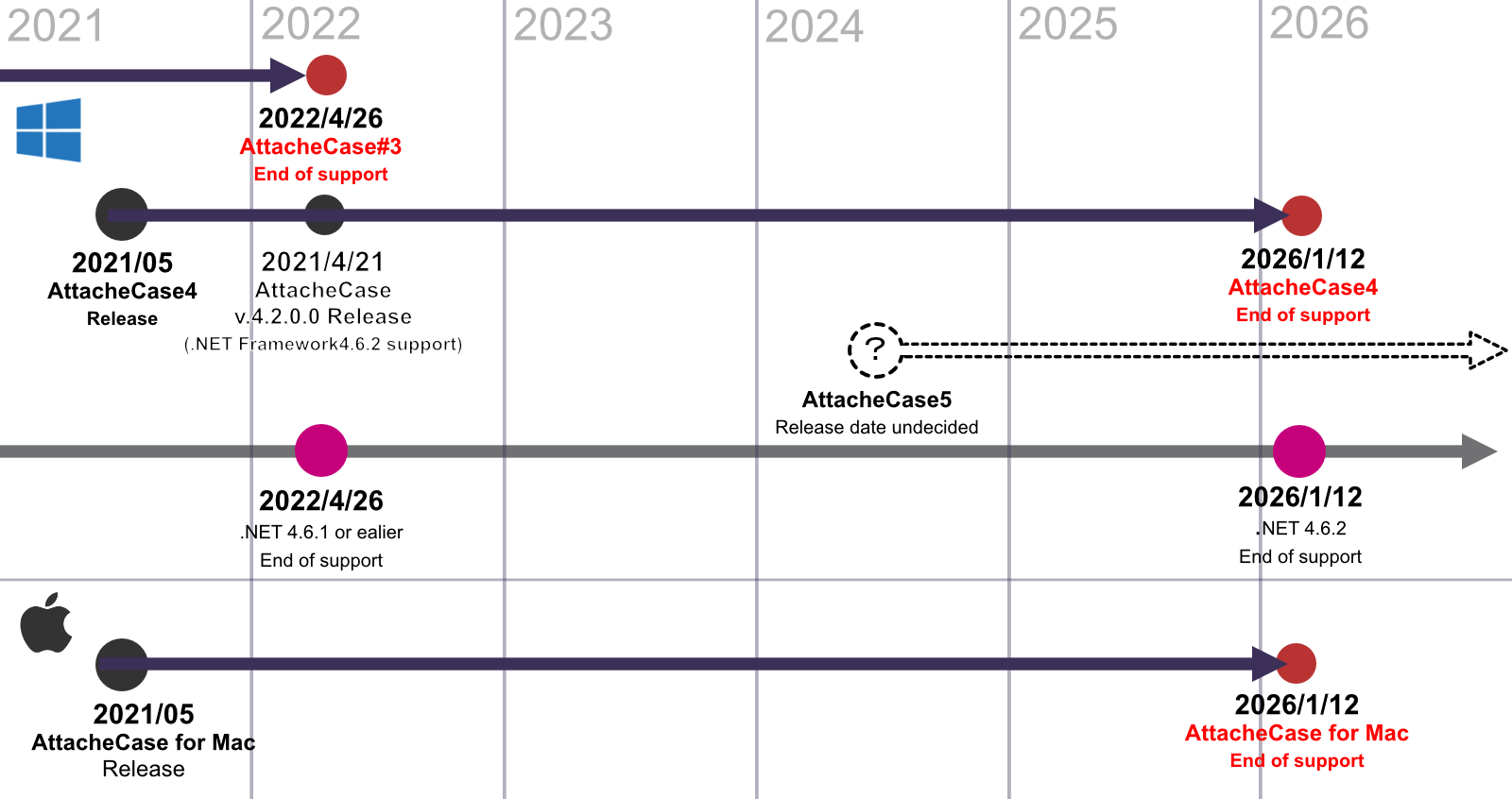
After that, we will support .NET7, .NET8 according to the latest libraries released by Microsoft.
Starting from ver.4, commercial use will be charged.
Windows
I also set the “trial period” as one month, but there is no limit to how long you can continue using the app.
The price is 550 yen (tax included) per 1 user.
Note that
- For home and personal use
- Students and educational institutions
can use it free of charge as a free license version.
You have free personal use, but if you would like to support us in the form of “support” or "donation", you are welcome to pay so. In that case, you will be issued a registration code, just like a commercial user.
As a result, support for the previous ver. 3 and 2 will be discontinued (Complete termination by April 2022). However, the previous versions will continue to be available free of charge for both personal and commercial use.
macOS
As for the macOS version, anyone (regardless of personal or commercial use) can use it free of charge.
However, that is only for downloads from this website, and any future downloads handled by the App Store will be paid for (whether for personal or commercial use).
The reason why downloads from this website, including the macOS version, are free of charge, while downloads from the App Store are paid for, is explained in the next section.
Why commercial use is now paid for?
There are many reasons for this, including the cost of managing and maintaining websites, the cost of continuing software development, especially the cost of “code signing certificates” that are added to executable files to prove that they are safe on Windows and can be installed without warning messages, and, for macOS, the Apple Developer registration fee etc. has become very difficult to cover with the decrease in advertising revenue.
I get a lot of emails about bugs and complaints, but other than that, I don’t know what kind of people are using it, and to be honest, I’m loss of motivation.
The source code is released under the GPLv3 license (the macOS version is not open to the public), so there are no restrictions on using it as a stray build. You will only be charged for downloading the software from this official website or the App Store (* Currently under review). In other words, please think of it as the cost of the distributed product, including development and maintenance costs, code signing certificate fees, etc.
スポンサー・リンク
Download
Ver.4
* Windows10, 11 / NET Framework 4.6 later
* macOS 10.14 (macOS Mojave) later
Hash value
MD5:
SHA-1:
SHA-256:
MD5:
SHA-1:
SHA-256:
MD5:
SHA-1:
SHA-256:
Update history for Windows version
Update history for macOS version
Old Ver.3
Important Notice(2022/03/30)
A previously reported vulnerability allows “AttacheCase#3” to be DLL hijacked (DLL preloaded) by placing certain DLL files in the location where the output self-extracting archive file and the main body “AttacheCase.exe” are located.
Please update to the latest version “AttacheCase#3” as soon as possible.
JVN#61502349
Self-Extracting Encrypted Files created by AttacheCase may insecurely load Dynamic Link Libraries
https://jvn.jp/en/jp/JVN61502349/
* Windows XP/Vista/7/8/10 / NET Framework 4.0 later
- Although support for this software has been discontinued by Microsoft, it also will work on Windows XP.
- .NET Framework 4 or higher is required for operation.
Hash value
Update history
Old Ver.2
* Windows 95, 98, XP
Hash value
Open source license
GPLv3 license
Copyright © 2020 M.Hibara
This program is free software: you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version.
This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details.
You should have received a copy of the GNU General Public License along with this program. If not, see http://www.gnu.org/licenses/.
Source code
hibara - GitHub
It has been built and tested with Microsoft Visual Studio 2019. It includes everything you need to build, including resource files. You are welcome to report bugs and requests to Issue, pull requests, forks, etc.
The MacOS version is not open source due to Apple’s terms and conditions. However, the classes required for encryption and decryption (specifically, Encrypt4.cs and Decrypt4.cs) are the same.

Data specification
Starting from ver.4, the cryptographic algorithm has been changed to AES 256bit CBC mode for ease of porting. I keep that .NET is moving in the direction of cutting off Rijindael 256 support for in the future in mind.
In addition, I used to use SHA-1 for checksums, which is a heavy load. MD5 is now sufficient for this purpose.
The file information stored in the data is now stored serially as binary data instead of character strings. For details, please see the following PDF file.
Download data specification
To learn more about the data structure, including previous versions (ver.3 and 2), please download the PDF data above and check it out.
オンラインヘルプ
Support
For inquiries (support), please contact us by e-mail. Please contact us at the following address
Mitsuhiro Hibara
If you would like to report a problem, please specify your OS version (Windows, macOS, and its version), the version of the AttachéCase you are using, and describe a situation that I can reproduce. If I can’t reproduce the problem, I can’t fix it.
If possible, please attach reproducible files and passwords (dummy data and dummy passwords are fine) so that I can make revisions smoothly.
Improvements, bug reports, and pull requests from GitHub are most welcome!
If possible, please use the GitHub repository instead of your email address, and send improvements and bug reports to Issues , or Pull Requests if you can fix the code directly.

