Headline
CVE-2021-27653: Collaboration Center
Misconfiguration of the Pega Chat Access Group portal in Pega platform 7.4.0 - 8.5.x could lead to unintended data exposure.
Pega continually works to implement security controls designed to protect client environments. As part of that effort, Pega has issued a CVE regarding the possibility of misconfiguring Pega Chat and Pega Intelligent Virtual Assistant (IVA) in a way that could lead to unintended data and system exposure.
CVE Details:
Software/Product: Pega Infinity
Version: 7.4.0-8.5.x
CVE ID: CVE-2021-27653
Title: Misconfiguration of the Pega Chat Access Group portal in Pega platform 7.4.0 - 8.5.x could lead to unintended data exposure.
If one of your current Pega installations leverages Pega Chat or the chat functionality as part of Pega Intelligent Virtual Assistant (IVA), please check for the following condition:
Pega Chat ships with a blank or empty portal definition in the CSSelfServiceUser access group. If your organization has changed or customized the access group portal, ensure the activated portal is also blank or empty, meaning it contains no harness or section definitions whatsoever.
We do not anticipate many clients have misconfigured their system in this way, however, we are issuing the CVE on short notice due to the possible risk of accidentally exposing your portal to unauthorized users in the event it was not set with a blank or empty portal definition.
As always, we recommend our customers review our Security Checklist regularly.
The following are additional details on how to check if you have the proper configuration.
- The access group referenced above is the access group that is associated with the template operator specified in the Webchat Channel rule.
- The possible misconfiguration reference to Pega Intelligent Virtual Assistant (IVA) relates to the Web Chatbot channel only.
Please see below for an example of the Pega Chat configuration as shipped out of the box.
Fig.1: An example of the out of the box Template operator record as shown from the Web Chatbot channel on the connection tab:
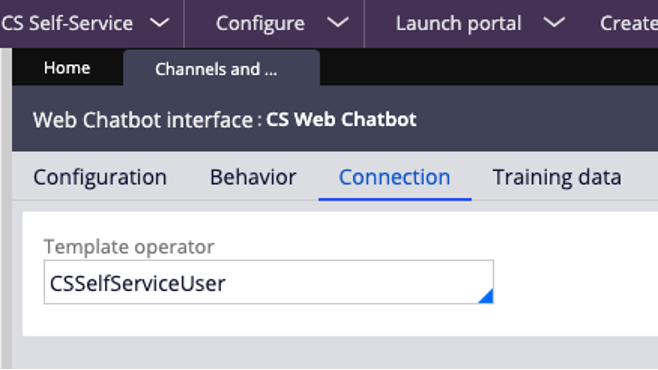
Fig. 2: The actual operator record:
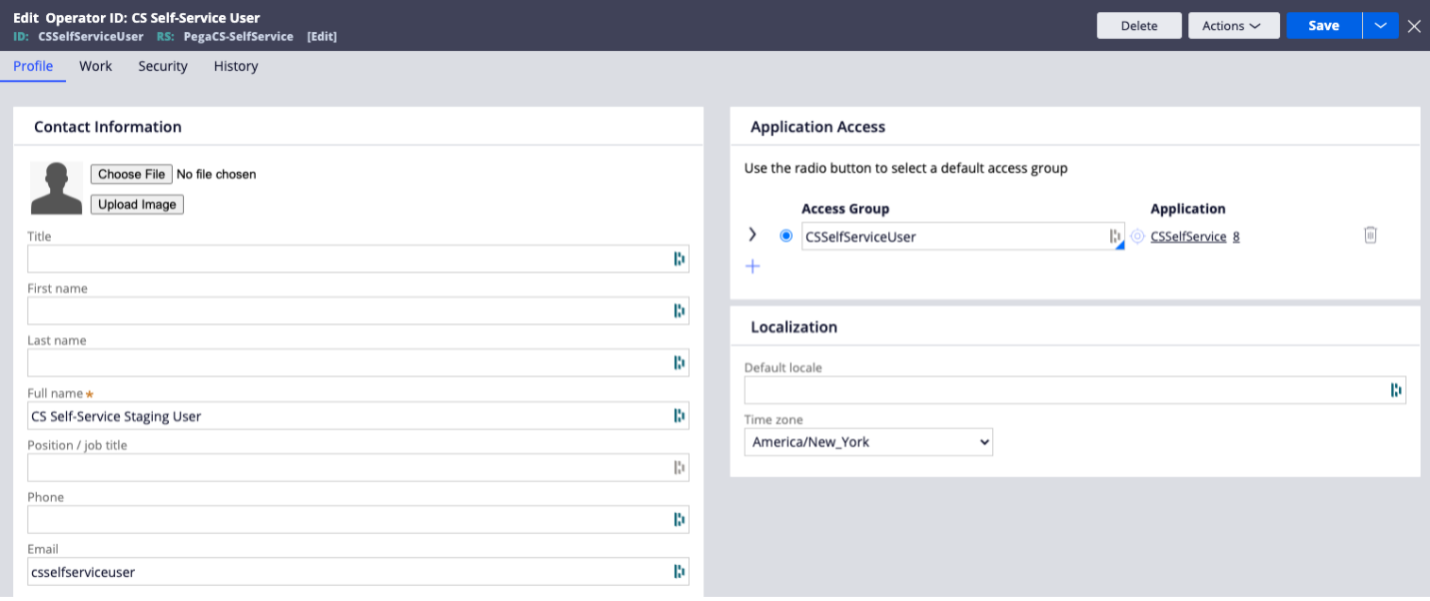
Fig. 3: The Access Group for the operator:
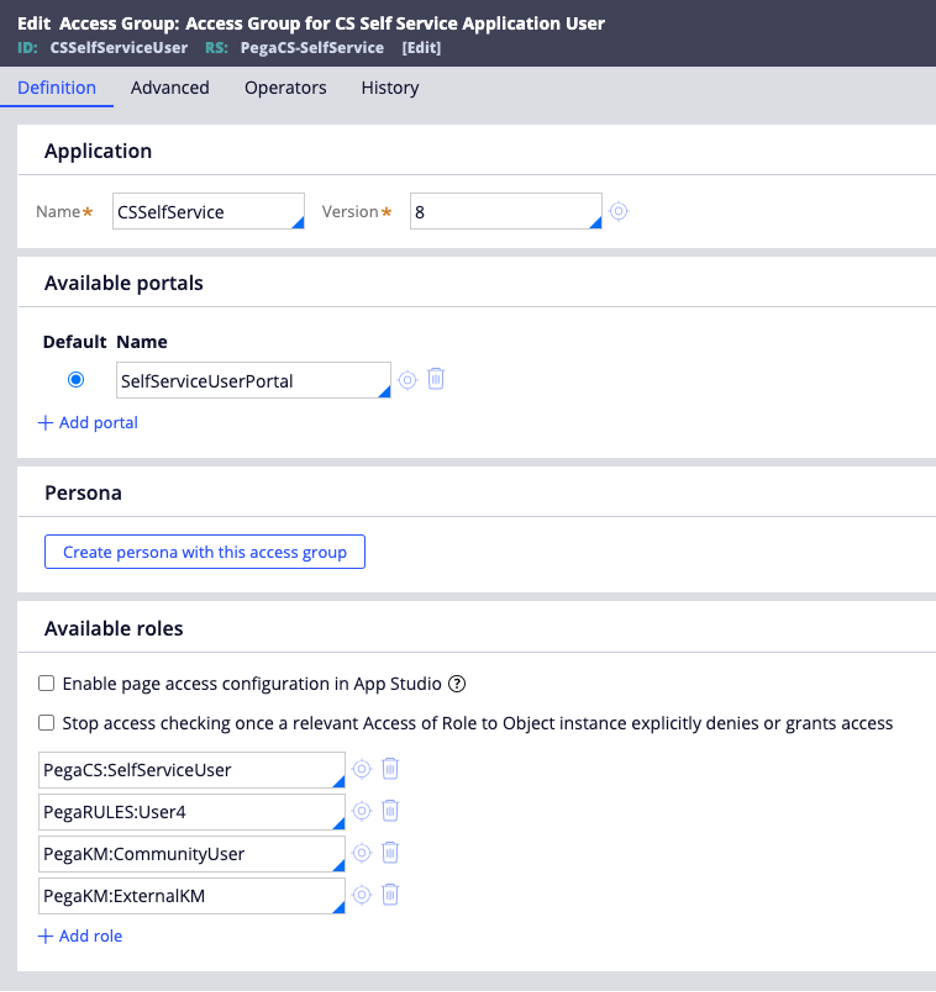
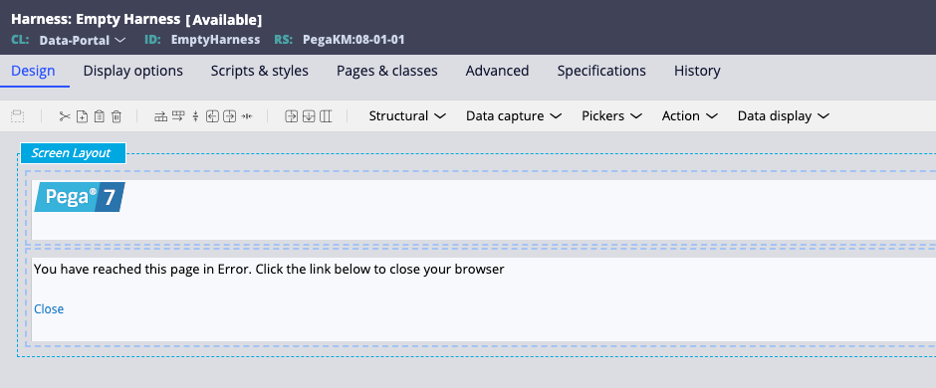
Fig. 4: The portal as defined (notice the harness name):
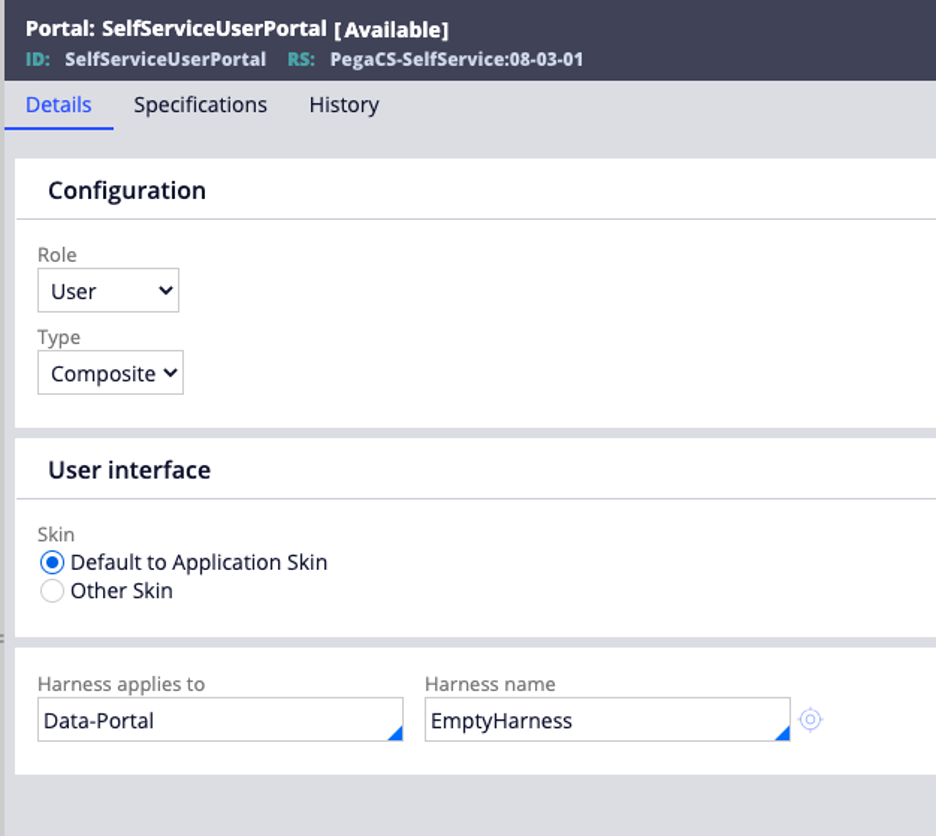
Fig. 5: The “Empty” Harness (note the harness is not truly empty, but contains no links leading away from the portal):