Headline
CVE-2021-3179: Yet another password manager app, how to better secure it?
GGLocker iOS application, contains an insecure data storage of the password hash value which results in an authentication bypass.
Insecure Data Storage found in GGLocker password manager app resulting in authentication bypass of the app

GGLocker for iOS
Password managers apps are an attractive target for hackers as they contain a users’ login credentials. This means that if you can break it, you gain access to a user’s credentials stored within. It is therefore important for the mobile app to be security conscious when handling the master password to access the vault of crown jewels.
When you first download the app, it will prompt you to enter a password which then create your own credentials database (the vault). After which, you will then proceed to enter the password you have entered to access the vault as shown below.
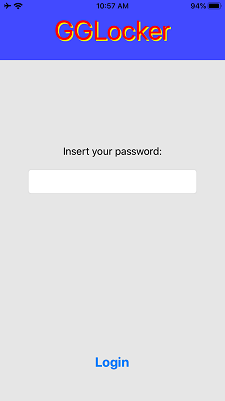
Entering the wrong password will deny access to the password vault and entering the correct password will allow access to the password vault.
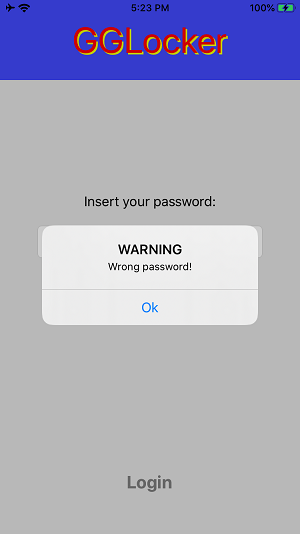
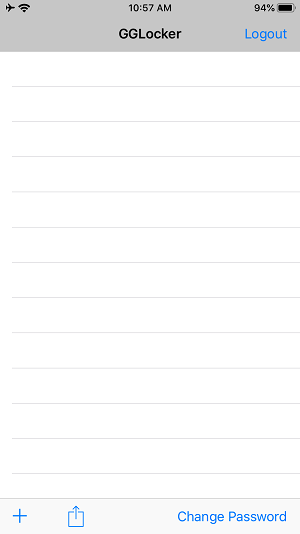
The main issue that I found is on the insecure storage of the password that is being used to access the vault.
Details: By inspecting the app’s source code found in the developer’s Github page, we know that the app does not store the password in plaintext. The text value is being hashed and the app stores the hash value.
We also identified that the LoginViewController has a function called perform that is responsible to validate the access to the vault. The perform function checks if the hash value the enter is identical to the hash value of the initial password set as shown below:
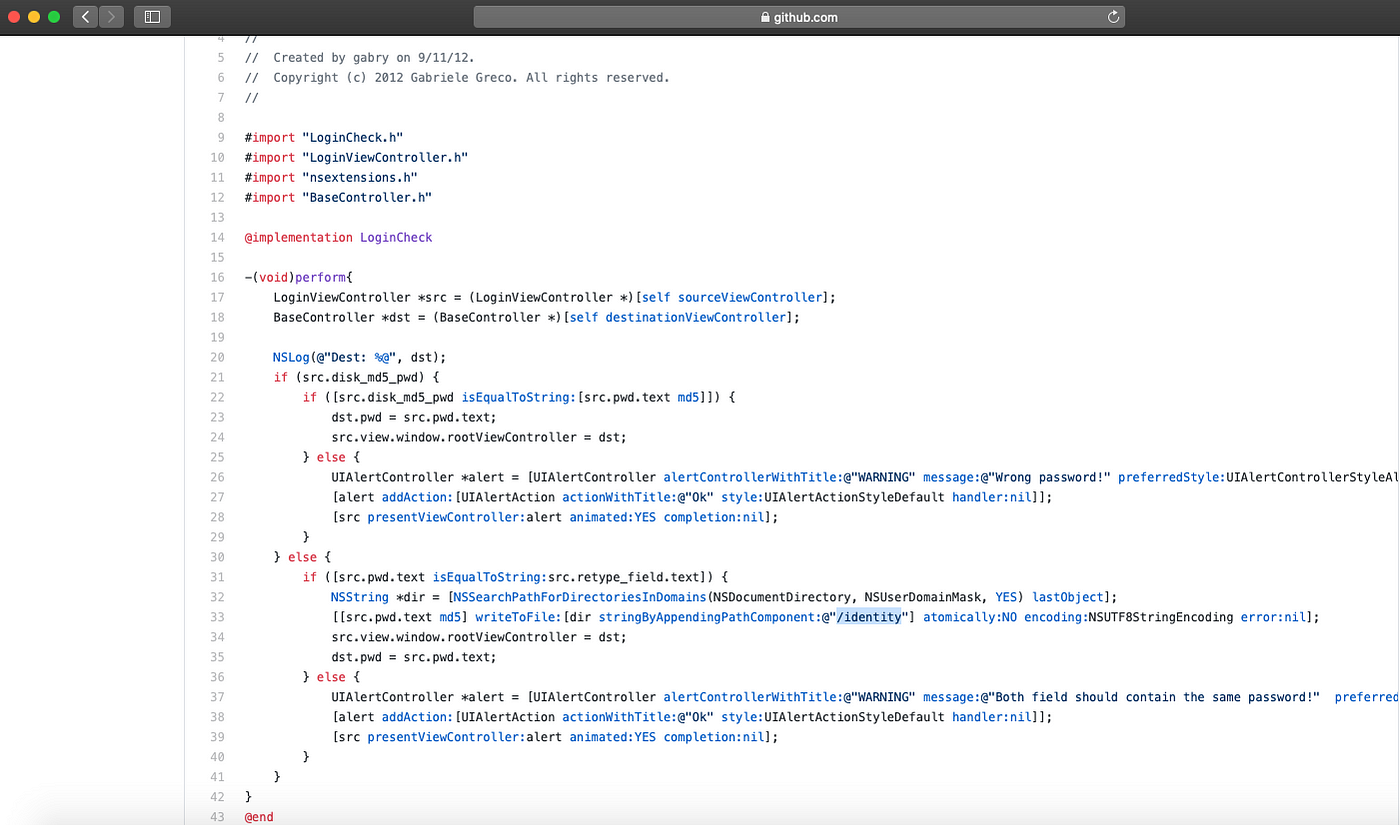
source code of “perform” function
As a hacker, this means that if I tamper the hash value of the perform function to an attacker controlled value, it is possible to perform an authentication bypass to access the vault! I believe that using a non jailbroken iPhone with Frida, Theos or Grapefruit would be able to perform the exploit. For demonstration purpose, I will be using Theos to perform hooking of LoginViewController to inspect the value of the return hashed value.
First, we will perform a classdump extraction of the mobile app to identify the function and we will then hook on the function to inspect the return value. The result should look something like this when inspecting app logs from macOS Console:
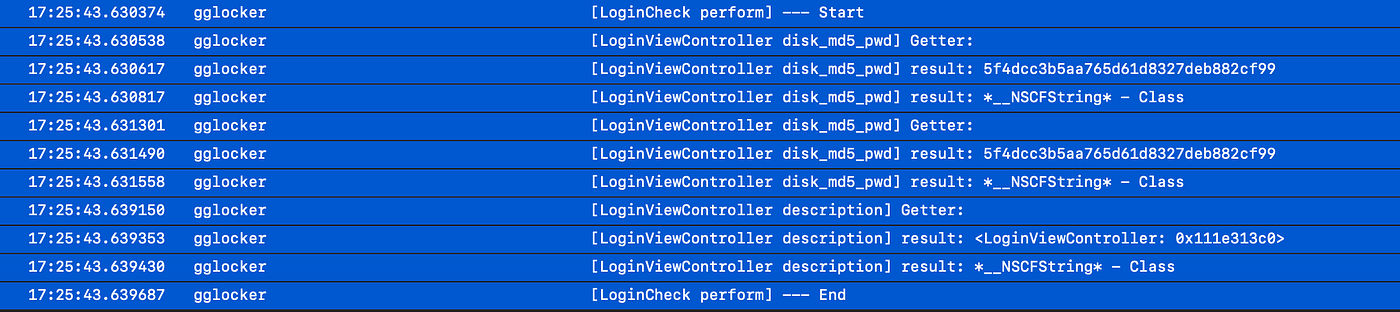
We noticed that “disk_md5_pwd” equals to “5f4dcc3b5aa765d61d8327deb882cf99” which translates to “password”. This also means that if a hacker enter the word “password”, the individual would be able to access the vault.
A skilled hacker can also take this vulnerability to the next level by manipulating the return value to a particular value of the individual choice :/
Recommendations:
- We can consider to implement jailbreak detection function to prevent the app from running in a jailbroken phone. By doing so, it makes things harder for a hacker to perform exploitation on the app. However do note that the vulnerability can still be performed in a non jailbroken environment (just that it will be much harder).
- To consider to store the hash value in a keychain to prevent unauthorized tampering of the value.
The purpose of the article is to educate and spread awareness on the importance of secure coding to better secure a mobile app. In no way I am promoting unethical hacking. Please hack responsibly and feel encouraged that you are taking baby steps in making the digital world more secure :)