Headline
CVE-2021-42749: Beaver Builder Vulnerabilities - Visibility and Conditional Logic (CVE-2021-42748 & CVE-2021-42749) - TEKFused
In Beaver Themer, attackers can bypass conditional logic controls (for hiding content) when viewing the post archives. Exploitation requires that a Themer layout is applied to the archives, and that the post excerpt field is not set.
Bottom line up front
I discovered two sensitive information disclosure vulnerabilities that affect Beaver Builder’s element visibility and Beaver Themer’s conditional logic controls. These vulnerabilities are resolved in Beaver Builder 2.5.1!
These vulnerabilities allow ANY user to view content that is hidden via the visibility or conditional logic controls.
NOTE: these vulnerabilities have been resolved by the Beaver Builder team, however, 3rd parties that have built their own modules (ie post archive /search modules) must update their module’s code so that their modules do not leak sensitive information. The Beaver Builder team has notified many of the 3rd party developers. The Beaver Builder team has also posted a developer oriented article about this issue.
The Issues
Content protected with visibility or conditional logic controls is accessible:
- to ANY user via the WordPress REST API (CVE-2021-42748)
- if a Beaver Themer layout is applied, and the post excerpt field is not set, the protected content may be shown in (CVE-2021-42749):
- post archive
- search results
- potentially in Google Search
What is affected****Beaver Builder
The lite (2.5.0.3 and older) and professional versions (2.5.0.3 and older) of the Beaver Builder page builder are affected. The lite version of Beaver Builder is installed on more than 200,000 websites.
NOTE: at the time of this writing, the Beaver Builder team hasn’t released an update for the lite version of Beaver Builder. They plan to release the Beaver Builder Lite update the week of 12/12/2021.
Beaver Themer
Beaver Themer is also affected. Beaver Themer is an add-on to the professional version of the Beaver Builder page builder which allows you to design every front-end area of WordPress.
The fix for the Beaver Themer vulnerability is included in Beaver Builder 2.5.1. Beaver Themer’s Conditional Logic feature is functionally separate from Beaver Builder’s visibility feature, but Beaver Themer uses a filter to hook into Beaver Builder’s codebase. The Beaver Builder 2.5.1 patch addresses both vulnerabilities.
Timeline
The Beaver Builder team was extremely responsive and professional as they developed a fix to remediate these vulnerabilities!
- Notification Sent to Beaver Builder
- Sunday, 10/17/2021
- 1st Response from Beaver Builder
- Monday, 10/18/2021
- Patch Sent to Me for Testing
- Tuesday, 11/16/2021
- Patch for Beaver Builder Professional Released
- Thursday, 12/9/2021
Vulnerability Summary
The lite & professional versions of Beaver Builder include visibility settings which allow you to limit the visibility of content based on the user’s login status. You can even specify a WordPress capability (aka permission) that the user must have to see the content.

Beaver Builder Lite visibility settings
Beaver Themer extends the visibility controls by adding conditional logic. Conditional logic allows you to create complex if-then-this conditions to control the visibility of content. A simple example would be “show the content only IF the user is a customer.”
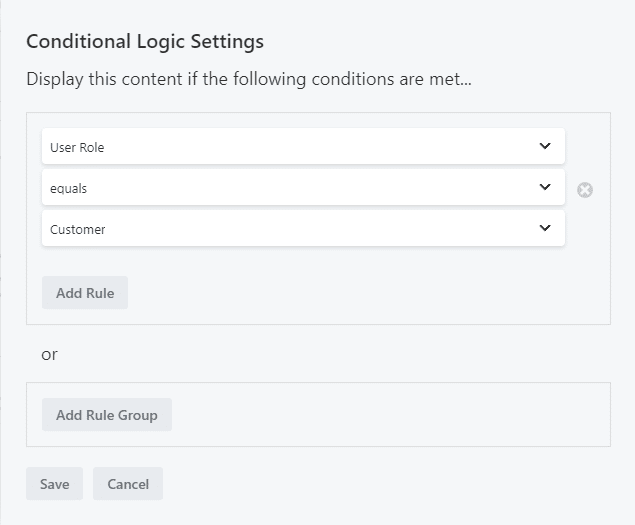
Beaver Themer Conditional Logic
Visibility rules & conditional logic are checked on the server side before delivering the rendered page. As such, these features should be able to be used to control access to sensitive content on a page.
The Beaver Builder team gave the following explanation:
The Post modules and the search module used the native WP the_excerpt() which looks at the saved data in post_content. The fix we implemented is to bypass that and use our layout functions. BB mirrors text based modules text in normal post content as a block so if you deactivate no text data or images are lost. So when WP looks up the excerpt it sees that data. As a result of that, it isn’t that we fixed a bug per se, more that we had to change default behavior.
The Test Page
The first row is hidden by using the visibility control “Display -> Logged In User” setting:

Row 1 settings
The second row is hidden by using the Conditional Logic setting (user role equals “Customer”):

Row 2 settings
The third row is visible to all users.

Row 3 settings
The page displays the “Content for the world!” text module for anonymous users as expected.

Test page seen as an unauthenticated user
The Vulnerabilities****Content Exposed in the WordPress REST API (CVE-2021-42748)
This vulnerability affects Beaver Builder (Lite & Professional) and Beaver Themer.
I sent a request to the “Posts” WordPress REST API endpoint as an unauthenticated (ie not logged in) user, and observed the protected content.

Unathenticated REST API call to WordPress
Content Exposed in the Post Archive (CVE-2021-42749)
This vulnerability affects Beaver Themer.
If:
- A Beaver Themer layout is applied to the post/search archive
- The post’s “Excerpt” field is not set
- The protected content is at the top of the post’s content
The protected content will be displayed under the post’s title.

Post archive showing protected content
Content Exposed in Google Search (CVE-2021-42749)
This vulnerability affects Beaver Themer.
Google lists the protected content in the Google SERP as it is displayed in the post category archive.
RSS Feeds
I tested the RSS feeds as an unauthenticated user, and they did NOT show the protected content.
Conclusion
The solution to these vulnerabilities is to update to Beaver Builder 2.5.1!
The principle of least functionality applies here – if you do not utilize the REST API, disable it – at least for unauthenticated users.