Headline
CVE-2021-41067: exploiting Listary: Searching your way to SYSTEM privileges
An issue was discovered in Listary through 6. Improper implementation of the update process leads to the download of software updates with a /check-update HTTP-based connection. This can be exploited with MITM techniques. Together with the lack of package validation, it can lead to manipulation of update packages that can cause an installation of malicious content.

Background:
While working on another research relating to DLL hijacking, I stumbled upon Listary. Listary is a known file-system search application used to index and quickly locate files.
First, I tried to find a DLL hijacking location. After restarting listary, Using Procmon with the appropriate filters, I could spot a few locations for hijacking from Admin->SYSTEM:


After discovering these locations, I decided to search for ways to get admin privileges in order to capitalize on this hijacking.
****Malicious update (MITM attack):****
By default, Listary will search for updates automatically
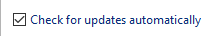
The Listary update process consists of the following steps:
1. Download the content of the following URL:
http://listray.com/check-update (HTTP communication!)
2. After downloading from the page (a simple html page with only a JSON string available publicly), the update process will parse the version number and the download URL from the json object without any validation!
3. The user will be prompted to download the new version of Listary from the parsed location
If an attacker has MITM capabilities, the attacker can manipulate the HTML response and plant a specially crafted JSON payload. The JSON payload can refer the user to download a malicious file instead of a legitimate update:
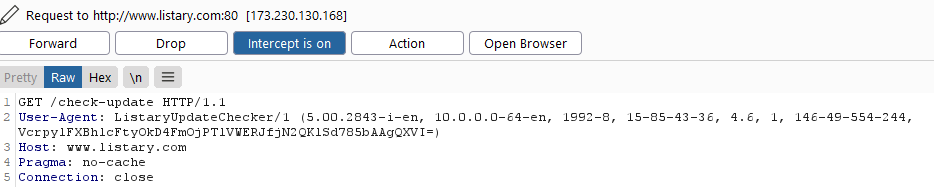
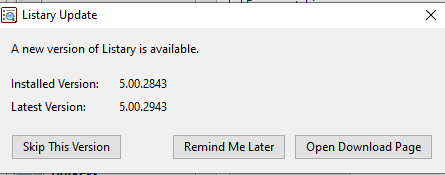
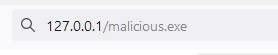
If the user that executed Listary has admin privileges, then the malicious update file can be configured to plant a malicious DLL in Listary’s folder that will be executed with SYSTEM privileges by using the above DLL hijacking location, Or just do other malicious actions with admin privileges…
Note that user would have to run the downloaded file, mistakenly treating it as a legitimate update file.
UAC Bypass:
Let’s say you don’t have a MITM but gained a foothold on an endpoint that has Listary installed to gain high integrity you just have to use the built-in option Listary provides to gain admin privileges through it:
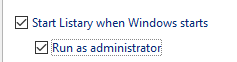
Listary will use its service to create a task that will execute listary’s client with highest possible privileges

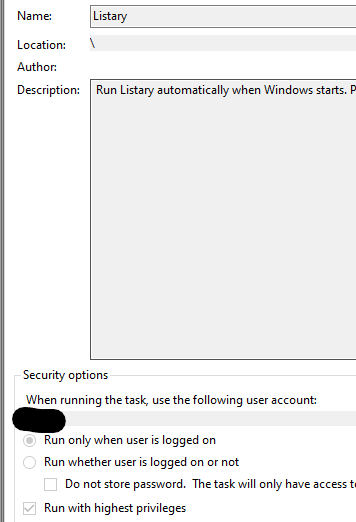
If a medium integrity user tries to click the “run with highest” button in task scheduler a UAC window will appear or a password prompt will appear:
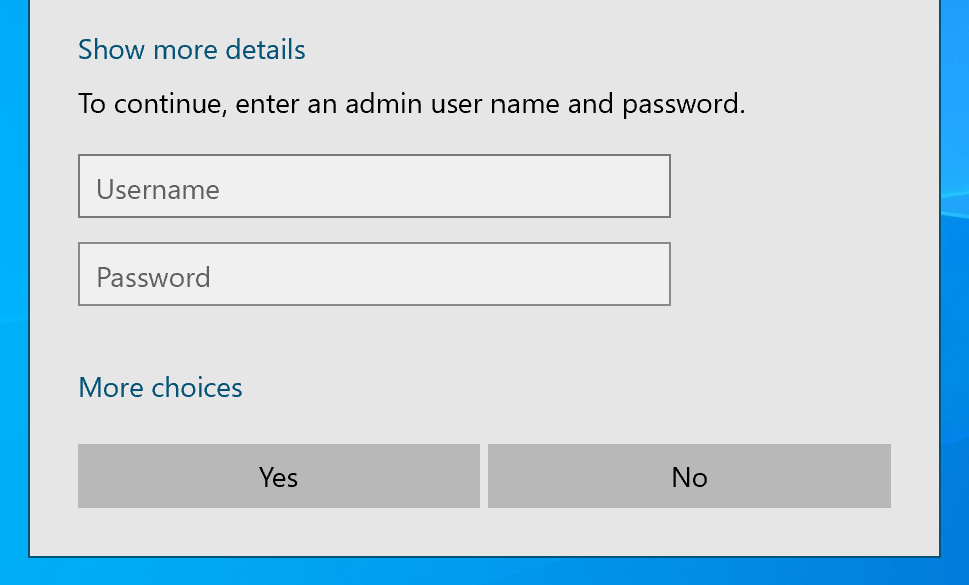
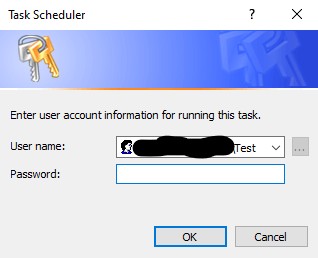
The upside of using this option is its evasiveness because it’s a legitimate program using its components and the downside is as mentioned above the requirement of some sort if interactive session with the victim’s endpoint.
The downside here is that you need an interactive session on the victim or an AutoIt script (or other script that will simulate mouse movement) to enable this option but once you do just restart the machine and Listary will run with the highest possible privileges for the “infected” account
After bypassing the UAC, you can plant a malicious DLL in Listary’s directory and gain SYSTEM privileges.
Named Pipes (Lateral Movement):
Pipes in OS’s are a way to allow inter process communication (IPC). By using pipes, one can direct a stream of data in his program to a waiting listener in another program.
There are two types of pipes in windows — named pipes and anonymous pipes.
Since Listary is using named pipes, we will focus on this type. Named pipes can be easily created by using the CreateNamedPipe WinApi call, specifying the pipe name in the format “\\\\.\\pipe\\mynamedpipe”
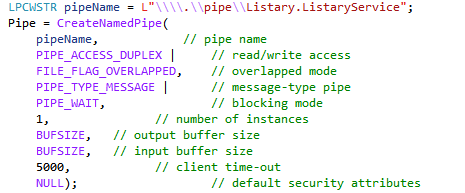
Named pipes can also be created using PowerShell in the following way:

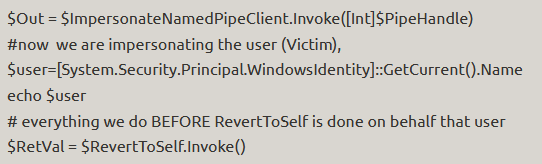
Named pipes can be accessed like normal files on a computer and therefore can be accessed with the normal WinAPI calls to ReadFile and WriteFile. More importantly, since named pipes are designed for servers to parse user input and act on it, Microsoft has provided programmers the WinAPI ImpersonateNamedPipeClient () — This function will allow a server to assume the security identity (Security Token) of the client’s thread and execute commands as the client.
This command has the same functionality as RpcImpersonateClient () (which we will elaborate on in a future post).
This technique was used widely by attackers to duplicate and impersonate genuine programs and perform privilege escalation and lateral movement attacks (like meterpreter’s GetSystem).
This impersonation can be done using PowerShell like so[7]:
Listary’s Service uses the named pipe \\.\pipe\Listary.ListaryService
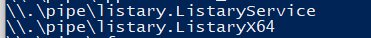
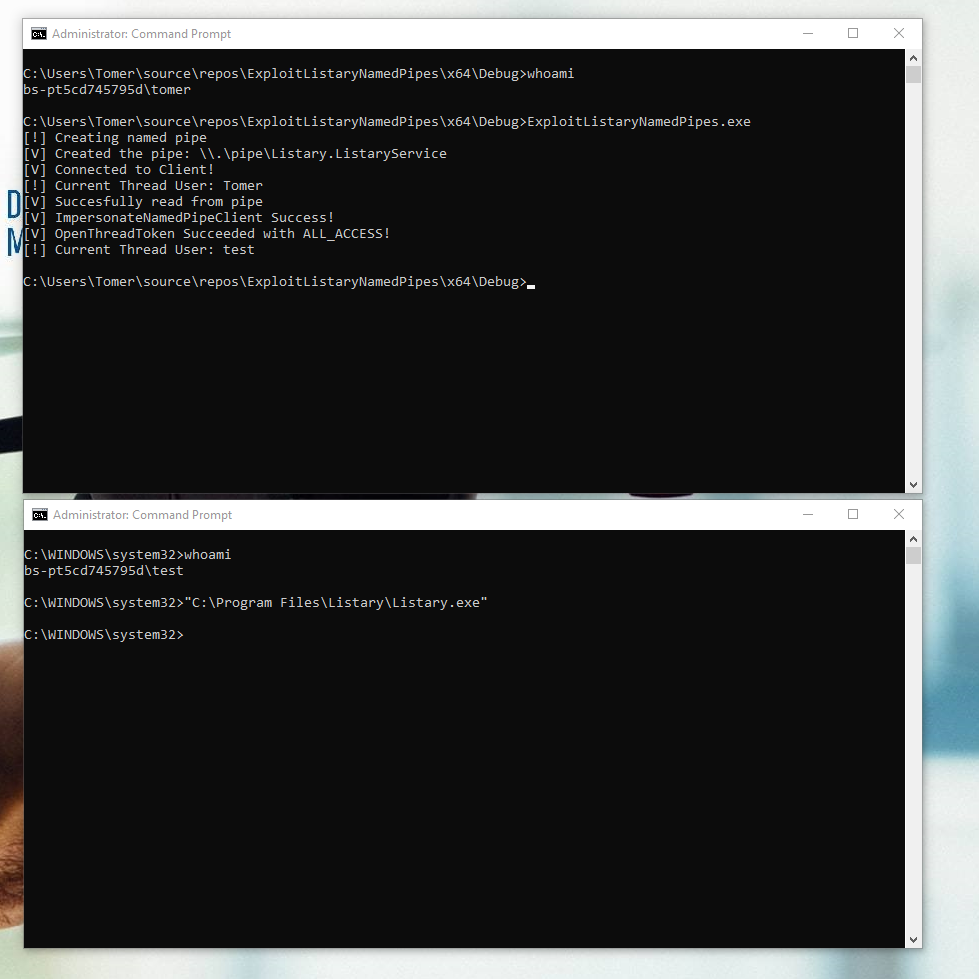
Because of that and the fact that Listary starts with windows by default we can use the information above about ImpersonateNamedPipeClient() and open a named pipe with CreateNamedPipe() and specify “\\.\pipe\Listary.ListaryService” as the name for the pipe.
For this example, let’s assume the attacker is a local admin since he needs to have “SeImpersonatePrivilege” for this to work.
The attacker just needs to wait for a domain admin (or any other user) to login, and once the user logged in into the endpoint the attacker can steal his privileges for lateral movement.
This will work since Listary client is configured to run on startup by default and will try to connect to the pipe server using a misconfigured CreateFile call:
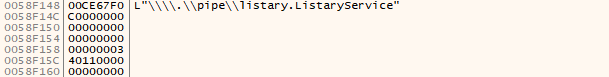
Notice that the security description is set to 0 and the flags are set to 0x40110000
Which translates to FILE_FLAG_OVERLAPPED | FILE_ATTRIBUTE_VIRTUAL | FILE_FLAG_OPEN_NO_RECALL no SQOS was specified therefore the default will be used which is
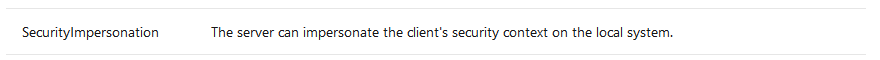
the attacker can leverage this connection as described to impersonate the Listary client’s thread.
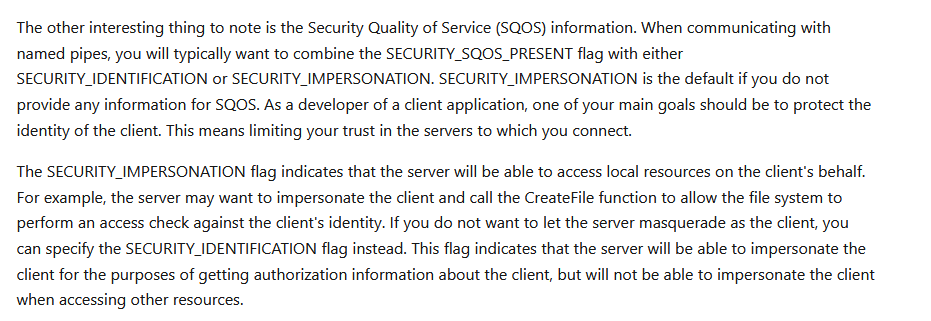
This technique was addressed by Microsoft with the addition of security flags for CreateFile namely a programmer needs to specify the flags “SECURITY_SQOS_PRESENT| SECURITY_IDENTIFICATION” which will prevent impersonation or execution of code on behalf of the client [8][3]
Conclusion:
Listary’s vulnerabilities present a problem for SOC/blue teams since they can be triggered as regular program activities.
In the best case; attackers can use Listary “only” for lateral movement but under the right circumstances’ attackers can use Listary for privilege escalation and remote code execution
Responsible disclosure:
29/08/2021 — vulnerabilities disclosed to Bopsoft/Listary team — No response
13/09/2021 — Vulnerabilities disclosed to MITRE — CVE numbers assigned CVE-2021–41065, CVE-2021–41066, CVE-2021–41067
19/09/2021 — Attempt to communicate with Bopsoft/Listary again — No response
09/12/2021 — Article published
References:
[1] https://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-createnamedpipea
[2] https://docs.microsoft.com/en-us/windows/win32/api/namedpipeapi/nf-namedpipeapi-impersonatenamedpipeclient
[3] https://itm4n.github.io/printspoofer-abusing-impersonate-privileges/
[4] https://itm4n.github.io/windows-dll-hijacking-clarified/
[5] https://en.wikipedia.org/wiki/Man-in-the-middle_attack
[6] https://pentestlab.blog/2017/05/03/uac-bypass-task-scheduler/
[7] https://decoder.cloud/2019/03/06/windows-named-pipes-impersonation/
[8] https://docs.microsoft.com/en-us/archive/msdn-magazine/2004/november/protect-your-apps-and-user-info-with-defensive-coding-techniques
[9] https://docs.microsoft.com/en-us/windows/win32/secauthz/impersonation-levels