Headline
TrickBot Operators Partner with Shathak Attackers for Conti Ransomware: TrickBot Operators Partner with Shathak Attackers for Conti Ransomware
The operators of TrickBot trojan are collaborating with the Shathak threat group to distribute their wares, ultimately leading to the deployment of Conti ransomware on infected machines. “The implementation of TrickBot has evolved over the years, with recent versions of TrickBot implementing malware-loading capabilities,” Cybereason security analysts Aleksandar Milenkoski and Eli Salem said in a
The operators of TrickBot trojan are collaborating with the Shathak threat group to distribute their wares, ultimately leading to the deployment of Conti ransomware on infected machines.
“The implementation of TrickBot has evolved over the years, with recent versions of TrickBot implementing malware-loading capabilities,” Cybereason security analysts Aleksandar Milenkoski and Eli Salem said in a report analysing recent malware distribution campaigns undertaken by the group. “TrickBot has played a major role in many attack campaigns conducted by different threat actors, from common cybercriminals to nation-state actors.”

The latest report builds on a report from IBM X-Force last month, which revealed TrickBot’s partnerships with other cybercrime gangs, including Shathak, to deliver proprietary malware. Also tracked under the moniker TA551, Shathak is a sophisticated cybercrime actor targeting end-users on a global scale, acting as a malware distributor by leveraging password-protected ZIP archives containing macro-enabled Office documents.
The TrickBot gang, known as ITG23 or Wizard Spider, is also responsible for developing and maintaining the Conti ransomware, in addition to leasing access to the malicious software to affiliates via a ransomware-as-a-service (RaaS) model.
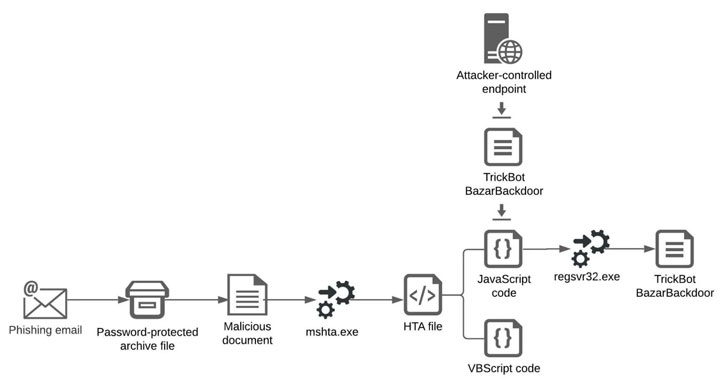
Infection chains involving Shathak typically involve sending phishing emails that come embedded with malware-laced Word documents that ultimately lead to the deployment of TrickBot or BazarBackdoor malware, which is then used as a conduit to deploy Cobalt Strike beacons as well as the ransomware, but not before conducting reconnaissance, lateral movement, credential theft, and data exfiltration activities.

Cybereason researchers said they observed an average Time-to-Ransom (TTR) of two days post the compromises, denoting the amount of time from when the threat actor gains initial access into a network to the time the threat actor actually deploys the ransomware.
The findings also come as the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) reported that no fewer than 400 Conti ransomware attacks had taken place targeting U.S. and international organizations as of September 2021.
To secure systems against Conti ransomware, the agencies recommend enforcing a variety of mitigation measures, including “requiring multi-factor authentication (MFA), implementing network segmentation, and keeping operating systems and software up to date.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.