Headline
North Korean Hackers Target Journalists with GOLDBACKDOOR Malware
A state-backed threat actor with ties to the Democratic People’s Republic of Korea (DRPK) has been attributed to a spear-phishing campaign targeting journalists covering the country with the ultimate goal of deploying a backdoor on infected Windows systems. The intrusions, said to be the work of Ricochet Chollima, resulted in the deployment of a novel malware strain called GOLDBACKDOOR, an

A state-backed threat actor with ties to the Democratic People’s Republic of Korea (DRPK) has been attributed to a spear-phishing campaign targeting journalists covering the country with the ultimate goal of deploying a backdoor on infected Windows systems.
The intrusions, said to be the work of Ricochet Chollima, resulted in the deployment of a novel malware strain called GOLDBACKDOOR, an artifact that shares technical overlaps with another malware named BLUELIGHT, which has been previously linked to the group.
“Journalists are high-value targets for hostile governments,” cybersecurity firm Stairwell said in a report published last week. “Compromising a journalist can provide access to highly-sensitive information and enable additional attacks against their sources.”

Ricochet Chollima, also known as APT37, InkySquid, and ScarCruft, is a North Korean-nexus targeted intrusion adversary that has been involved in espionage attacks since at least 2016. The threat actor has a track record of targeting the Republic of Korea with a noted focus on government officials, non-governmental organizations, academics, journalists, and North Korean defectors.
In November 2021, Kaspersky unearthed evidence of the hacking crew delivering a previously undocumented implant called Chinotto as part of a new wave of highly-targeted surveillance attacks, while other prior operations have made use of a remote access tool called BLUELIGHT.
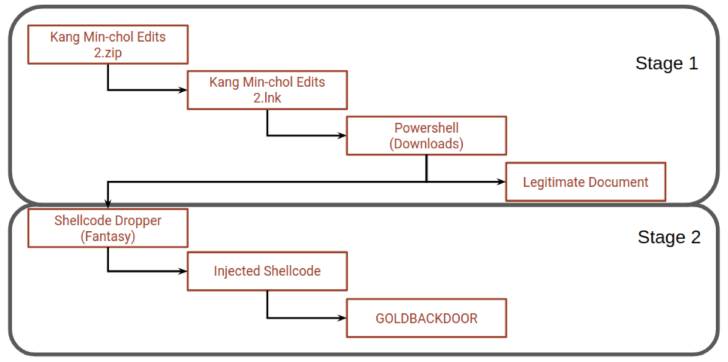
Stairwell’s investigation into the campaign comes weeks after NK News disclosed that the lure messages were sent from a personal email address belonging to a former South Korean intelligence official, ultimately leading to the deployment of the backdoor in a multi-stage infection process to evade detection.

The email messages were found to contain a link to download a ZIP archive from a remote server designed to impersonate the North Korea-focused news portal. Embedded within the file is a Windows shortcut file that acts as a jumping-off point to execute the PowerShell script, which opens a decoy document while simultaneously installing the GOLDBACKDOOR backdoor.
The implant, for its part, is fashioned as a Portable Executable file that’s capable of retrieving commands from a remote server, uploading and downloading files, recording files, and remotely uninstalling itself from the compromised machines.
“Over the past 10 years, the Democratic People’s Republic of Korea DPRK has adopted cyber operations as a key means of supporting the regime,” Stairwell’s Silas Cutler said.
“While significant attention has been paid to the purported use of these operations as a means of funding DPRK’s military programs, the targeting of researchers, dissidents, and journalists likely remains a key area for supporting the country’s intelligence operations.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.