Source
ghsa
An issue in OpenStack magnum yoga-eom version allows a remote attacker to execute arbitrary code via the cert_manager.py. component.
### Summary Timber is vulnerable to [PHAR deserialization](https://portswigger.net/web-security/deserialization/exploiting#phar-deserialization) due to a lack of checking the input before passing it into the` file_exists()` function. If an attacker can upload files of any type to the server, he can pass in the `phar://` protocol to unserialize the uploaded file and instantiate arbitrary PHP objects. This can lead to remote code execution especially when Timber is used with frameworks with documented POP chains like Wordpress/ vulnerable developer code. ### Details The vulnerability lies in the run function within the `toJpg.php` file. The two parameters passed into it are not checked or sanitized, hence an attacker could potentially inject malicious input leading to Deserialization of Untrusted Data, allowing for remote code execution: 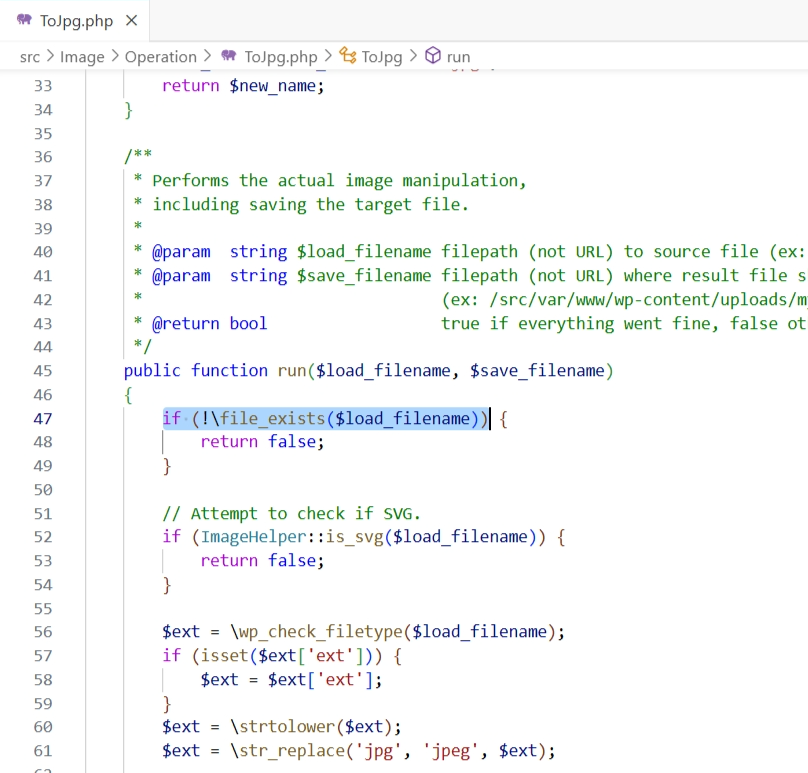 ### PoC Setup the following code in `/var/www/html`: `...
### Impact Prior to the patched version, logged in users of Mautic are vulnerable to a self XSS vulnerability in the notifications within Mautic. Users could inject malicious code into the notification when saving Dashboards. ### Patches Update to Mautic 4.4.12. ### Workarounds None ### References - https://owasp.org/www-project-top-ten/2017/A7_2017-Cross-Site_Scripting_(XSS) If you have any questions or comments about this advisory: Email us at [[email protected]](mailto:[email protected])
While an Apache Kafka cluster is being migrated from ZooKeeper mode to KRaft mode, in some cases ACLs will not be correctly enforced. Two preconditions are needed to trigger the bug: 1. The administrator decides to remove an ACL 2. The resource associated with the removed ACL continues to have two or more other ACLs associated with it after the removal. When those two preconditions are met, Kafka will treat the resource as if it had only one ACL associated with it after the removal, rather than the two or more that would be correct. The incorrect condition is cleared by removing all brokers in ZK mode, or by adding a new ACL to the affected resource. Once the migration is completed, there is no metadata loss (the ACLs all remain). The full impact depends on the ACLs in use. If only ALLOW ACLs were configured during the migration, the impact would be limited to availability impact. if DENY ACLs were configured, the impact could include confidentiality and integrity impact depending ...
An issue in tiagorlampert CHAOS v5.0.1 allows a remote attacker to execute arbitrary code via the BuildClient function within client_service.go
An issue discovered in Reportico Till 8.1.0 allows attackers to obtain sensitive information via execute_mode parameter of the URL.
### Impact Prior to the patched version, there is an XSS vulnerability in the description fields within the Mautic application which could be exploited by a logged in user of Mautic with the appropriate permissions. This could lead to the user having elevated access to the system. ### Patches Update to 4.4.12 ### Workarounds None ### References - https://owasp.org/www-project-top-ten/2017/A7_2017-Cross-Site_Scripting_(XSS) - https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/07-Input_Validation_Testing/02-Testing_for_Stored_Cross_Site_Scripting If you have any questions or comments about this advisory: Email us at [[email protected]](mailto:[email protected])
### Impact A specially crafted argument to the `idna.encode()` function could consume significant resources. This may lead to a denial-of-service. ### Patches The function has been refined to reject such strings without the associated resource consumption in version 3.7. ### Workarounds Domain names cannot exceed 253 characters in length, if this length limit is enforced prior to passing the domain to the `idna.encode()` function it should no longer consume significant resources. This is triggered by arbitrarily large inputs that would not occur in normal usage, but may be passed to the library assuming there is no preliminary input validation by the higher-level application. ### References * https://huntr.com/bounties/93d78d07-d791-4b39-a845-cbfabc44aadb
### Impact Users may be impacted if sending requests including sensitive data in specific headers with `followRedirects` enabled. ### Patches The [follow-redirects](https://github.com/follow-redirects/follow-redirects) library is now being used for redirects and removes some headers that may contain sensitive information in some situations. ### Workarounds N/A. Please update to resolve the issue.
### Impact The matrix-appservice-irc before version 2.0.0 can be exploited to leak the truncated body of a message if a malicious user sends a Matrix reply to an event ID they don't have access to. As a precondition to the attack, the malicious user needs to know the event ID of the message they want to leak, as well as to be joined to both the Matrix room and the IRC channel it is bridged to. The message reply containing the leaked message content is visible to IRC channel members when this happens. ### Patches matrix-appservice-irc 2.0.0 checks whether the user has permission to view an event before constructing a reply. Administrators should upgrade to this version. ### Workarounds It's possible to limit the amount of information leaked by setting a reply template that doesn't contain the original message. See [these lines](https://github.com/matrix-org/matrix-appservice-irc/blob/d5d67d1d3ea3f0f6962a0af2cc57b56af3ad2129/config.sample.yaml#L601-L604) in the configuration file. ...