Headline
U.S. Offers $10 Million Bounty for Information on 6 Russian Military Hackers
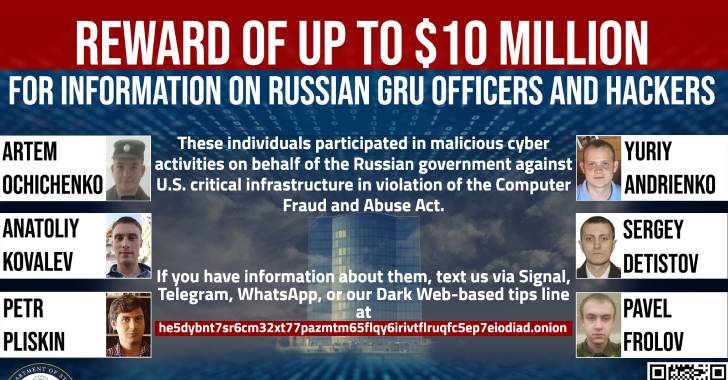
The U.S. government on Tuesday announced up to $10 million in rewards for information on six hackers associated with the Russian military intelligence service. “These individuals participated in malicious cyber activities on behalf of the Russian government against U.S. critical infrastructure in violation of the Computer Fraud and Abuse Act,” the State Department’s Rewards for Justice Program
The U.S. government on Tuesday announced up to $10 million in rewards for information on six hackers associated with the Russian military intelligence service.
“These individuals participated in malicious cyber activities on behalf of the Russian government against U.S. critical infrastructure in violation of the Computer Fraud and Abuse Act,” the State Department’s Rewards for Justice Program said.
All the six Russian officers are members of an advanced persistent threat group called Sandworm (aka Voodoo Bear or Iron Viking), which is known to be operating since at least 2008 with a specific focus on targeting entities in Ukraine with the goal of establishing an illicit, long-term presence in order to mine highly sensitive data.

The hacker, who are officers of the Main Intelligence Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU), are as follows -
Artem Valeryevich Ochichenko, who has been linked to technical reconnaissance and spear-phishing campaigns to gain unauthorized access to IT networks of critical infrastructure facilities worldwide
Petr Nikolayevich Pliskin, Sergey Vladimirovich Detistov, Pavel Valeryevich Frolov, and Yuriy Sergeyevich Andrienko, who are said to have developed components of the NotPetya and Olympic Destroyer malware used by the Russian government on June 27, 2017 to infect computer systems, and
Anatoliy Sergeyevich Kovalev, who is accused of developing spear-phishing techniques and messages used by the Russian government to breach computer systems of critical infrastructure facilities

On October 15, 2020, the U.S. Justice Department indicted the aforementioned officers for carrying out destructive malware attacks with an aim to disrupt and destabilize other nations and cause monetary losses, charging them with conspiracy to commit wire fraud and aggravated identity theft.

As part of the initiative, the Rewards of Justice has set up a Tor website at “he5dybnt7sr6cm32xt77pazmtm65flqy6irivtflruqfc5ep7eiodiad[.]onion” that can be used to submit tips about these threat actors anonymously, or alternatively share the information via Signal, Telegram, or WhatsApp.
The Sandworm collective was most recently attributed to a now-neutralized sophisticated botnet malware dubbed Cyclops Blink that ensnared internet-connected firewall devices and routers from WatchGuard and ASUS.
Other recent hacking activities associated with the group include the deployment of an upgraded version of the Industroyer malware against high-voltage electrical substations in Ukraine amidst the ongoing invasion.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.