Tag
#js
Red Hat Security Advisory 2024-1500-03 - An update for thunderbird is now available for Red Hat Enterprise Linux 8.2 Advanced Update Support, Red Hat Enterprise Linux 8.2 Telecommunications Update Service, and Red Hat Enterprise Linux 8.2 Update Services for SAP Solutions. Issues addressed include integer overflow, out of bounds write, and use-after-free vulnerabilities.
Red Hat Security Advisory 2024-1499-03 - An update for thunderbird is now available for Red Hat Enterprise Linux 8.4 Advanced Mission critical Update Support, Red Hat Enterprise Linux 8.4 Telecommunications Update Service, and Red Hat Enterprise Linux 8.4 Update Services for SAP Solutions. Issues addressed include integer overflow, out of bounds write, and use-after-free vulnerabilities.
Red Hat Security Advisory 2024-1497-03 - An update for thunderbird is now available for Red Hat Enterprise Linux 8.6 Extended Update Support. Issues addressed include integer overflow, out of bounds write, and use-after-free vulnerabilities.
Red Hat Security Advisory 2024-1496-03 - An update for thunderbird is now available for Red Hat Enterprise Linux 8.8 Extended Update Support. Issues addressed include integer overflow, out of bounds write, and use-after-free vulnerabilities.
Red Hat Security Advisory 2024-1491-03 - An update for firefox is now available for Red Hat Enterprise Linux 8.4 Advanced Mission critical Update Support, Red Hat Enterprise Linux 8.4 Telecommunications Update Service, and Red Hat Enterprise Linux 8.4 Update Services for SAP Solutions. Issues addressed include integer overflow, out of bounds write, and use-after-free vulnerabilities.
Red Hat Security Advisory 2024-1490-03 - An update for firefox is now available for Red Hat Enterprise Linux 8.2 Advanced Update Support, Red Hat Enterprise Linux 8.2 Telecommunications Update Service, and Red Hat Enterprise Linux 8.2 Update Services for SAP Solutions. Issues addressed include integer overflow, out of bounds write, and use-after-free vulnerabilities.
Red Hat Security Advisory 2024-1489-03 - An update for firefox is now available for Red Hat Enterprise Linux 8.6 Extended Update Support. Issues addressed include integer overflow, out of bounds write, and use-after-free vulnerabilities.
Red Hat Security Advisory 2024-1488-03 - An update for firefox is now available for Red Hat Enterprise Linux 8.8 Extended Update Support. Issues addressed include integer overflow, out of bounds write, and use-after-free vulnerabilities.
Red Hat Security Advisory 2024-1487-03 - An update for firefox is now available for Red Hat Enterprise Linux 9.0 Extended Update Support. Issues addressed include integer overflow, out of bounds write, and use-after-free vulnerabilities.
### Summary An attacker with admin privileges can upload an attachment containing JS code without extension and the application will render it as HTML which allows for XSS attacks. ### Details When attachments are uploaded without an extension, the application renders it as HTML by default. Therefore allowing attackers to upload .html files containing javascript code to perform XSS attacks. The direct file path to the uploaded attachment is also easily obtainable as it is made up of substrings of the file's MD5 hashes. ### PoC 1. Admin users can upload attachments containing XSS payloads in files without extensions to bypass the .html extension check. 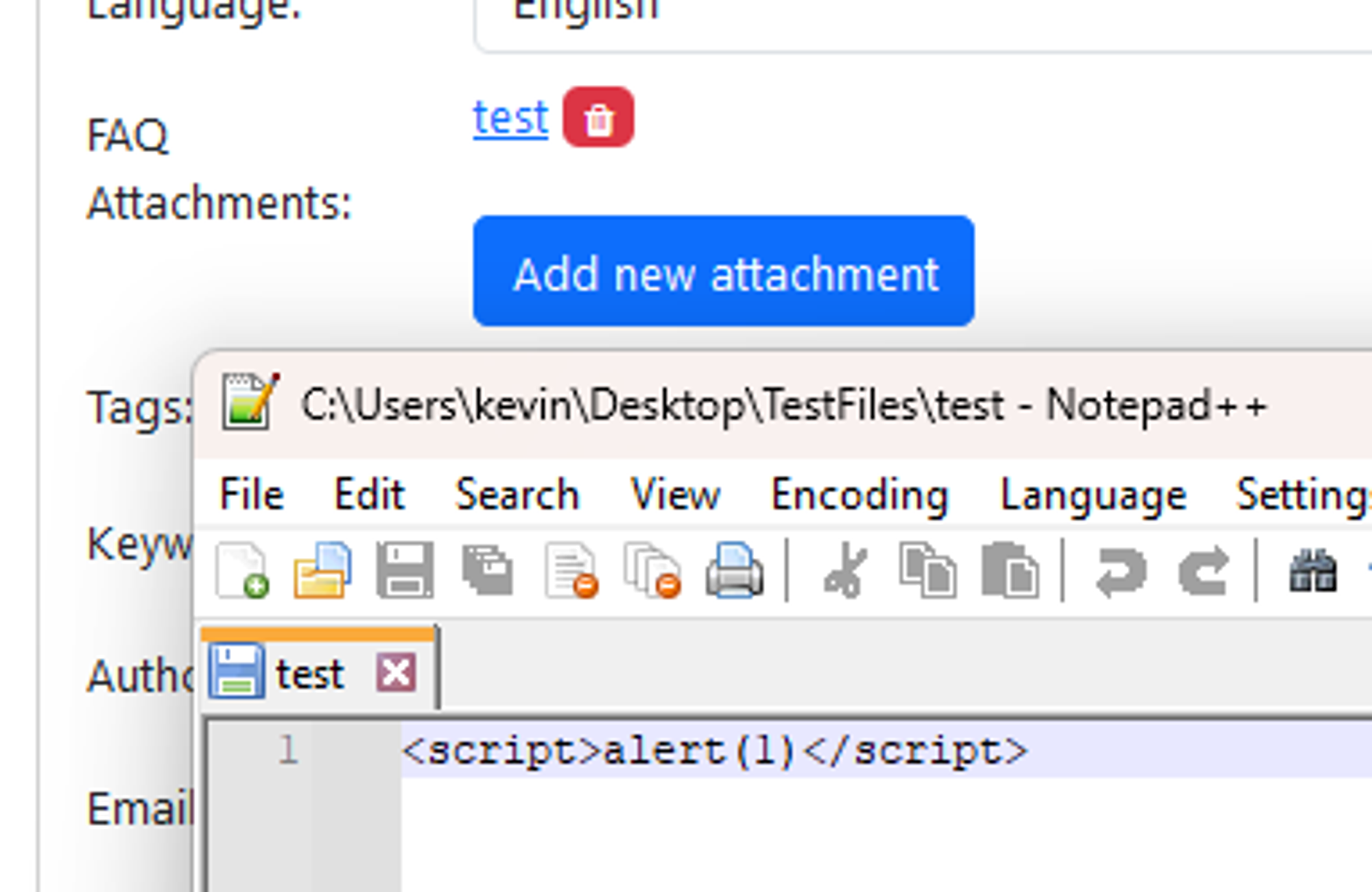 2. Since the path of the uploaded file is built entirely on the file’s MD5 hash and the attachment directory, it is possible for an attacker to know the direct path of the uploaded file. E.g file MD5 hash: 38fff51cb7248a06d6142c6bdf84...