Tag
#rce
### Summary Timber is vulnerable to [PHAR deserialization](https://portswigger.net/web-security/deserialization/exploiting#phar-deserialization) due to a lack of checking the input before passing it into the` file_exists()` function. If an attacker can upload files of any type to the server, he can pass in the `phar://` protocol to unserialize the uploaded file and instantiate arbitrary PHP objects. This can lead to remote code execution especially when Timber is used with frameworks with documented POP chains like Wordpress/ vulnerable developer code. ### Details The vulnerability lies in the run function within the `toJpg.php` file. The two parameters passed into it are not checked or sanitized, hence an attacker could potentially inject malicious input leading to Deserialization of Untrusted Data, allowing for remote code execution: 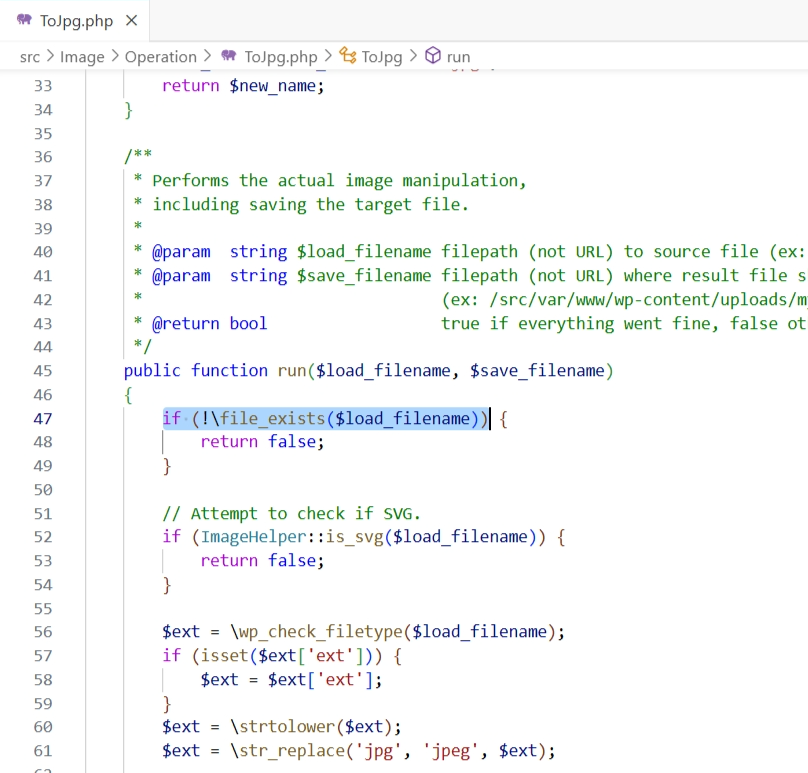 ### PoC Setup the following code in `/var/www/html`: `...
The Ray Project dashboard contains a CPU profiling page, and the format parameter is not validated before being inserted into a system command executed in a shell, allowing for arbitrary command execution. If the system is configured to allow passwordless sudo (a setup some Ray configurations require) this will result in a root shell being returned to the user. If not configured, a user level shell will be returned. Versions 2.6.3 and below are affected.
The security community is still reflecting on the “What If” of the XZ backdoor.
GUnet OpenEclass E-learning platform version 3.15 suffers from an unrestricted file upload vulnerability in certbadge.php that allows for remote command execution.
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens' ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: Telecontrol Server Basic Vulnerabilities: Inadequate Encryption Strength, Double Free, Integer Overflow or Wraparound, External Control of File Name or Path, Path Traversal, Improper Input Validation, Missing Encryption of Sensitive Data, Use After Free, Improper Certificate Validation, Inefficient Regular Expression Complexity, Improper Check for Unusual or Exceptional Conditions, NULL Pointer Dereference, Improper Restriction of Operations within the Bounds of a Memory Buffer 2. RISK EVALUATION Successful exploitation of this vulnerability could 3. TEC...
As of January 10, 2023, CISA will no longer be updating ICS security advisories for Siemens product vulnerabilities beyond the initial advisory. For the most up-to-date information on vulnerabilities in this advisory, please see Siemens' ProductCERT Security Advisories (CERT Services | Services | Siemens Global). View CSAF 1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low attack complexity Vendor: Siemens Equipment: Scalance W1750D Vulnerabilities: Classic Buffer Overflow 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow an attacker to exploit buffer overflow and information disclosure vulnerabilities which could lead to information disclosure or unauthenticated remote code execution. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following products of Siemens Scalance W1750D, a direct access point, are affected: Siemens SCALANCE W1750D (JP) (6GK5750-2HX01-1AD0): All versions prior to V8.10.0.9 Siemens SCALANCE W1750D (ROW) (6GK5750-2HX...
Versions of the package mysql2 before 3.9.4 are vulnerable to Remote Code Execution (RCE) via the `readCodeFor` function due to improper validation of the `supportBigNumbers` and `bigNumberStrings` values.
The huggingface/transformers library is vulnerable to arbitrary code execution through deserialization of untrusted data within the `load_repo_checkpoint()` function of the `TFPreTrainedModel()` class. Attackers can execute arbitrary code and commands by crafting a malicious serialized payload, exploiting the use of `pickle.load()` on data from potentially untrusted sources. This vulnerability allows for remote code execution (RCE) by deceiving victims into loading a seemingly harmless checkpoint during a normal training process, thereby enabling attackers to execute arbitrary code on the targeted machine.
A critical Remote Code Execution (RCE) vulnerability was identified in the aimhubio/aim project, specifically within the `/api/runs/search/run/` endpoint, affecting versions >= 3.0.0. The vulnerability resides in the `run_search_api` function of the `aim/web/api/runs/views.py` file, where improper restriction of user access to the `RunView` object allows for the execution of arbitrary code via the `query` parameter. This issue enables attackers to execute arbitrary commands on the server, potentially leading to full system compromise.
gradio-app/gradio is vulnerable to a local file inclusion vulnerability due to improper validation of user-supplied input in the UploadButton component. Attackers can exploit this vulnerability to read arbitrary files on the filesystem, such as private SSH keys, by manipulating the file path in the request to the `/queue/join` endpoint. This issue could potentially lead to remote code execution. The vulnerability is present in the handling of file upload paths, allowing attackers to redirect file uploads to unintended locations on the server.