Headline
Chinese Hackers Targeting Russian Military Personnel with Updated PlugX Malware
A China-linked government-sponsored threat actor has been observed targeting Russian speakers with an updated version of a remote access trojan called PlugX. Secureworks attributed the attempted intrusions to a threat actor it tracks as Bronze President, and by the wider cybersecurity community under the monikers Mustang Panda, TA416, HoneyMyte, RedDelta, and PKPLUG. "The war in Ukraine has
A China-linked government-sponsored threat actor has been observed targeting Russian speakers with an updated version of a remote access trojan called PlugX.
Secureworks attributed the attempted intrusions to a threat actor it tracks as Bronze President, and by the wider cybersecurity community under the monikers Mustang Panda, TA416, HoneyMyte, RedDelta, and PKPLUG.
“The war in Ukraine has prompted many countries to deploy their cyber capabilities to gain insight about global events, political machinations, and motivations,” the cybersecurity firm said in a report shared with The Hacker News. “This desire for situational awareness often extends to collecting intelligence from allies and 'friends.’”
Bronze President, active since at least July 2018, has a history of conducting espionage operations by leveraging custom and publicly available tools to compromise, maintain long-term access, and collect data from targets of interest.

Chief among its tools is PlugX, a Windows backdoor that enables threat actors to execute a variety of commands on infected systems and which has been employed by several Chinese state-sponsored actors over the years.
The latest findings from Secureworks suggest an expansion of the same campaign previously detailed by Proofpoint and ESET last month, which has involved the use of a new variant of PlugX codenamed Hodur, so labeled owing to its overlaps with another version called THOR that emerged on the scene in July 2021.
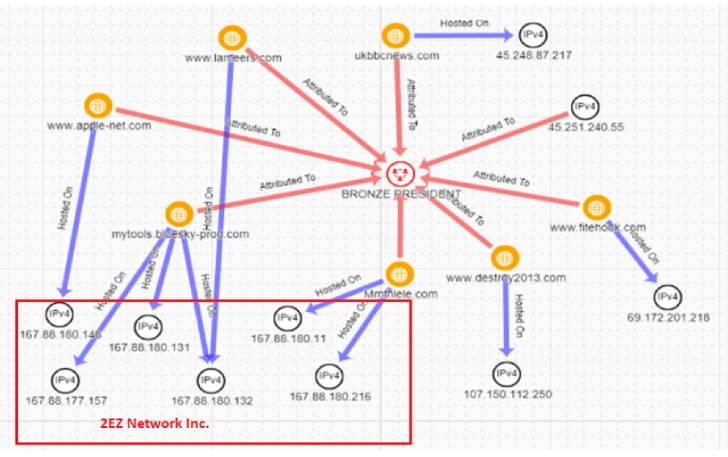
The attack chain commences with a malicious executable named “Blagoveshchensk - Blagoveshchensk Border Detachment.exe” that masquerades as a seemingly legitimate document with a PDF icon, which, when opened, leads to the deployment of an encrypted PlugX payload from a remote server.
“Blagoveshchensk is a Russian city close to the China border and is home to the 56th Blagoveshchenskiy Red Banner Border Guard Detachment,” the researchers said. “This connection suggests that the filename was chosen to target officials or military personnel familiar with the region.”
The fact that Russian officials may have been the target of the March 2022 campaign indicates that the threat actor is evolving its tactics in response to the political situation in Europe and the war in Ukraine.

“Targeting Russian-speaking users and European entities suggests that the threat actors have received updated tasking that reflects the changing intelligence collection requirements of the [People’s Republic of China],” the researchers said.
The findings come weeks after another China-based nation-state group known as Nomad Panda (aka RedFoxtrot) was linked with medium confidence to attacks against defense and telecom sectors in South Asia by leveraging yet another version of PlugX dubbed Talisman.
“PlugX has been associated with various Chinese actors in recent years,” Trellix noted last month. “This fact raises the question if the malware’s code base is shared among different Chinese state-backed groups.”
“On the other hand, the alleged leak of the PlugX v1 builder, as reported by Airbus in 2015, indicates that not all occurrences of PlugX are necessarily tied to Chinese actors,” the cybersecurity company added.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
Related news
A campaign by APT37 used a sophisticated malware to steal information about sources , which appears to be a successor to Bluelight.
Spear-phishing campaign loaded with new "Goldbackdoor" malware targeted journalists with NK News, analysts found.