Headline
Emotet Testing New Delivery Ideas After Microsoft Disables VBA Macros by Default
The threat actor behind the prolific Emotet botnet is testing new attack methods on a small scale before co-opting them into their larger volume malspam campaigns, potentially in response to Microsoft’s move to disable Visual Basic for Applications (VBA) macros by default across its products. Calling the new activity a “departure” from the group’s typical behavior, ProofPoint alternatively

The threat actor behind the prolific Emotet botnet is testing new attack methods on a small scale before co-opting them into their larger volume malspam campaigns, potentially in response to Microsoft’s move to disable Visual Basic for Applications (VBA) macros by default across its products.
Calling the new activity a “departure” from the group’s typical behavior, ProofPoint alternatively raised the possibility that the latest set of phishing emails distributing the malware show that the operators are now “engaged in more selective and limited attacks in parallel to the typical massive scale email campaigns.”

Emotet, the handiwork of a cybercrime group tracked as TA542 (aka Mummy Spider or Gold Crestwood), staged a revival of sorts late last year after a 10-month-long hiatus following a coordinated law enforcement operation to take down its attack infrastructure.
Since then, Emotet campaigns have targeted thousands of customers with tens of thousands of messages in several geographic regions, with the message volume surpassing over one million per campaign in select cases.
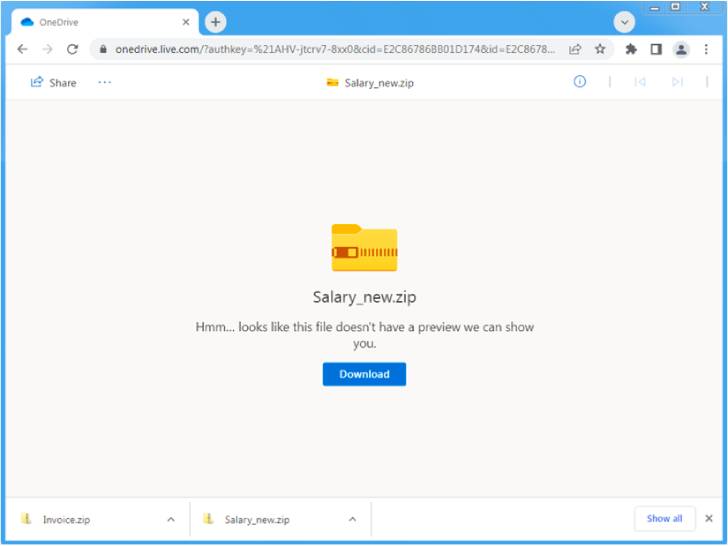
The new “low volume” email campaign analyzed by the enterprise security firm involved the use of salary-themed lures and OneDrive URLs hosting ZIP archives that contain Microsoft Excel Add-in (XLL) files, which, when executed, drop and run the Emotet payload.
The new set of social engineering attacks is said to have taken place between April 4, 2022, and April 19, 2022, when other widespread Emotet campaigns were put on hold.

The absence of macro-enabled Microsoft Excel or Word document attachments is a significant shift from previously observed Emotet attacks, suggesting that the threat actor is pivoting away from the technique as a way to get around Microsoft’s plans to block VBA macros by default starting April 2022.
The development also comes as the malware authors last week fixed an issue that prevented potential victims from getting compromised upon opening the weaponized email attachments.
“After months of consistent activity, Emotet is switching things up,” Sherrod DeGrippo, vice president of threat research and detection at Proofpoint, said.
“It is likely the threat actor is testing new behaviors on a small scale before delivering them to victims more broadly, or to distribute via new TTPs alongside its existing high-volume campaigns. Organizations should be aware of the new techniques and ensure they are implementing defenses accordingly.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
Related news
Microsoft on Tuesday disclosed a set of two privilege escalation vulnerabilities in the Linux operating system that could potentially allow threat actors to carry out an array of nefarious activities. Collectively called "Nimbuspwn," the flaws "can be chained together to gain root privileges on Linux systems, allowing attackers to deploy payloads, like a root backdoor, and perform other
New 'trust' tool improves online experience and helps tackle digital fraud.