Tag
#git
### Summary There is improper sanitization on Service template name which is reflecting in delete button onclick event. This value can be modified and crafted as any other javascript code. ### Vulnerable Code https://github.com/librenms/librenms/blob/a61c11db7e8ef6a437ab55741658be2be7d14d34/app/Http/Controllers/ServiceTemplateController.php#L67C23-L67C23 Above is vulnerable code line which needs to be properly sanitized ### PoC 1. Go to /services/templates 2. Enter name as `testing', '14', 'http://172.105.62.194:8000/services/templates/14');alert(1);//` 3. Submit it and try to delete it, you will see popup If you inspect element on delete button, you will notice this:- <img width="748" alt="Screenshot 2023-11-23 at 9 30 24 PM" src="https://user-images.githubusercontent.com/31764504/285260018-7672a93d-e29b-4444-8057-e6ffcb8dabfc.png"> ### Impact Cross site scripting can lead to cookie stealing or an attacker can execute any other feature using this feature.
### Summary SQL injection vulnerability in POST /search/search=packages in LibreNMS 24.3.0 allows a user with global read privileges to execute SQL commands via the package parameter. ### Details There is a lack of hygiene of data coming from the user in line 83 of the file librenms/includes/html/pages/search/packages.inc.php 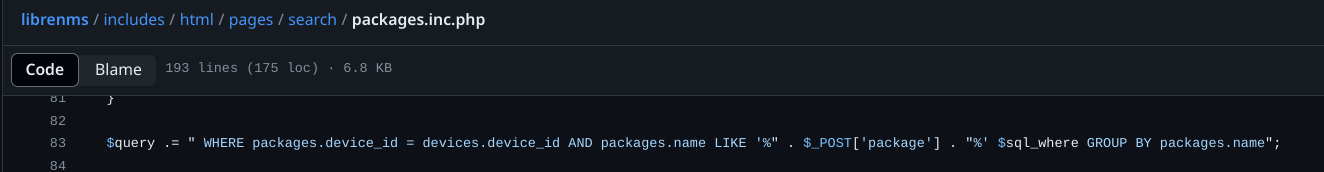 ### PoC https://doc.clickup.com/9013166444/p/h/8ckm0bc-53/16811991bb5fff6 ### Impact With this vulnerability, we can exploit a SQL injection time based vulnerability to extract all data from the database, such as administrator credentials
### Impact Under very specific conditions changes to a users groups may not have the expected results. The specific conditions are: * The file authentication backend is being used. * The [watch](https://www.authelia.com/configuration/first-factor/file/#watch) option is set to true. * The [refresh_interval](https://www.authelia.com/configuration/first-factor/introduction/#refresh_interval) is configured to a non-disabled value. * The users groups are adjusted by an administrator. * The user attempts to access a resource that their groups previously had access to but their new groups do not have access to. When these conditions are met administrators may find the changes are not taken into account by access control for longer than expected periods. While this may not necessarily be a security vulnerability it's security-adjacent and because of the unexpected nature of it and our dedication to a security-first culture we feel it's important to make users aware of this behaviour utiliz...
### Impact We have identified a local privilege escalation vulnerability in Ant Media Server which allows any unprivileged operating system user account to escalate privileges to the root user account on the system. This vulnerability arises from Ant Media Server running with Java Management Extensions (JMX) enabled and authentication disabled on localhost on port 5599/TCP. This vulnerability is nearly identical to the local privilege escalation vulnerability CVE-2023-26269 identified in Apache James. Any unprivileged operating system user can connect to the JMX service running on port 5599/TCP on localhost and leverage the MLet Bean within JMX to load a remote MBean from an attacker-controlled server. This allows an attacker to execute arbitrary code within the Java process run by Ant Media Server and execute code within the context of the “antmedia” service account on the system. ### Patches 2.9.0 ### Workarounds Remote the following parameters from antmedia.service file ```-Dcom....
RCE-Remote Command Execution vulnerability in Apache HugeGraph-Server.This issue affects Apache HugeGraph-Server: from 1.0.0 before 1.3.0 in Java8 & Java11 Users are recommended to upgrade to version 1.3.0 with Java11 & enable the Auth system, which fixes the issue.
Authentication Bypass by Spoofing vulnerability in Apache HugeGraph-Server.This issue affects Apache HugeGraph-Server: from 1.0.0 before 1.3.0. Users are recommended to upgrade to version 1.3.0, which fixes the issue.
Server-Side Request Forgery (SSRF) vulnerability in Apache HugeGraph-Hubble. This issue affects Apache HugeGraph-Hubble: from 1.0.0 before 1.3.0. Users are recommended to upgrade to version 1.3.0, which fixes the issue.
Over the past two years, a shocking 51% of organizations surveyed in a leading industry report have been compromised by a cyberattack. Yes, over half. And this, in a world where enterprises deploy an average of 53 different security solutions to safeguard their digital domain. Alarming? Absolutely. A recent survey of CISOs and CIOs, commissioned by Pentera and
By Deeba Ahmed IT professionals are under attack! This article exposes a malicious malvertising campaign targeting IT teams with a novel backdoor named MadMxShell. Learn how attackers use typosquatting and DNS techniques to compromise systems. This is a post from HackRead.com Read the original post: Malvertising: Fake Popular Software Ads Deliver New MadMxShell Backdoor
An internet scraping platform is offering access to a database filled with over four billion Discord messages and combined user profiles.