Tag
#git
### Summary Piccolo's admin panel provides the ability to upload media files and view them within the admin panel. If SVG is an allowed file type for upload; the default; an attacker can upload an SVG which when loaded under certain contexts allows for arbitrary access to the admin page. This access allows the following actions for example: - The ability for an attacker to gain access to all data stored within the admin page - The ability for an attacker to make any action within the admin page such as creating, modifying or deleting table records As the SVG is executed from the context of an authenticated admin session, any actions they may be able to make can be made by the attacker. *N.b. The relevant session cookies are inaccessible from JavaScript due to httponly being set so all exploits must be present within the SVG file* ### PoC _Complete instructions, including specific configuration details, to reproduce the vulnerability._ Currently, this requires the ability for a ...
### Summary The Casa OS Login page has disclosed the username enumeration vulnerability in the login page which was patched in `CasaOS v0.4.7`. ### Details It is observed that the attacker can enumerate the CasaOS username using the application response. If the username is incorrect the application gives the error "**User does not exist**" with success code "**10006**", If the password is incorrect the application gives the error "**User does not exist or password is invalid**" with success code "**10013**". ### PoC 1. If the Username is invalid application gives "User does not exist" with success code "**10006**". 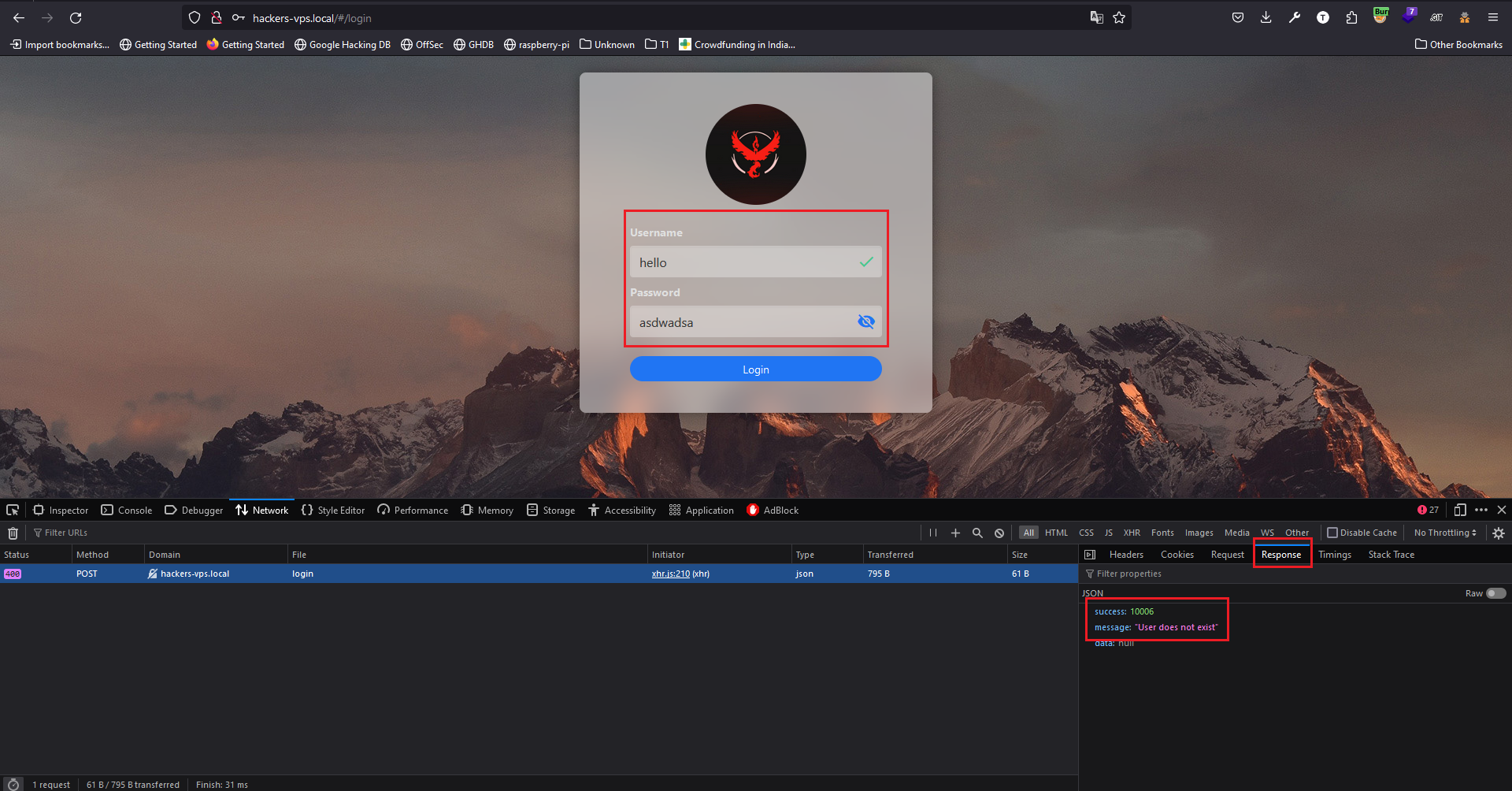 2. If the Password is invalid application gives "**User does not exist or password is invalid**" with success code "**10013**". 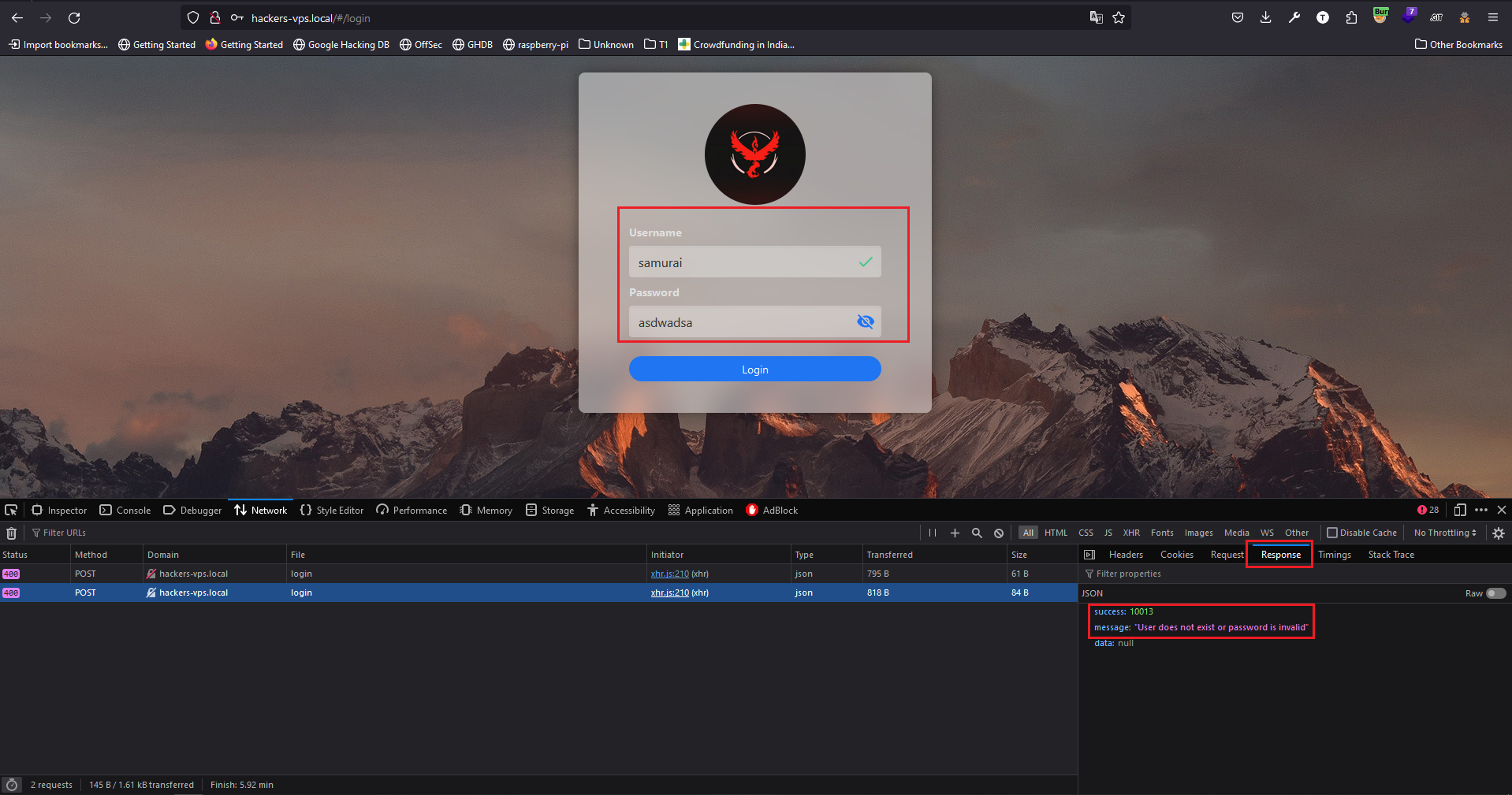 ### Impact Using...
ARIS: Business Process Management version 10.0.21.0 suffers from a persistent cross site scripting vulnerability.
Gibbon version 26.0.00 suffers from a server-side template injection vulnerability that allows for remote code execution.
Millions lost internet service after three cables in the Red Sea were damaged. Houthi rebels deny targeting the cables, but their missile attack on a cargo ship, left adrift for months, is likely to blame.
JJWT (aka Java JWT) through 0.12.5 ignores certain characters and thus a user might falsely conclude that they have a strong key. The impacted code is the setSigningKey() method within the DefaultJwtParser class and the signWith() method within the DefaultJwtBuilder class.
Bonita before 10.1.0.W11 allows stored XSS via a UI screen in the administration panel.
By Waqas Another day, another alleged data breach putting hundred of thousands of unsuspecting users at risk. This is a post from HackRead.com Read the original post: Israeli LGBTQ App Atraf Faces Data Leak, 700,000 Users Affected
Plus: “MFA bombing” attacks target Apple users, Israel deploys face recognition tech on Gazans, AI gets trained to spot tent encampments, and OSINT investigators find fugitive Amond Bundy.
By Uzair Amir Learn how blockchain is transforming digital identity management by empowering individuals with self-sovereign control over personal data through… This is a post from HackRead.com Read the original post: Blockchain in Identity Management: Securing Personal Data and Identities