Tag
#git
### Impact The steps are as follows: 1. Access https://IP:PORT/ in the browser, which prompts the user to access with a secure entry point. 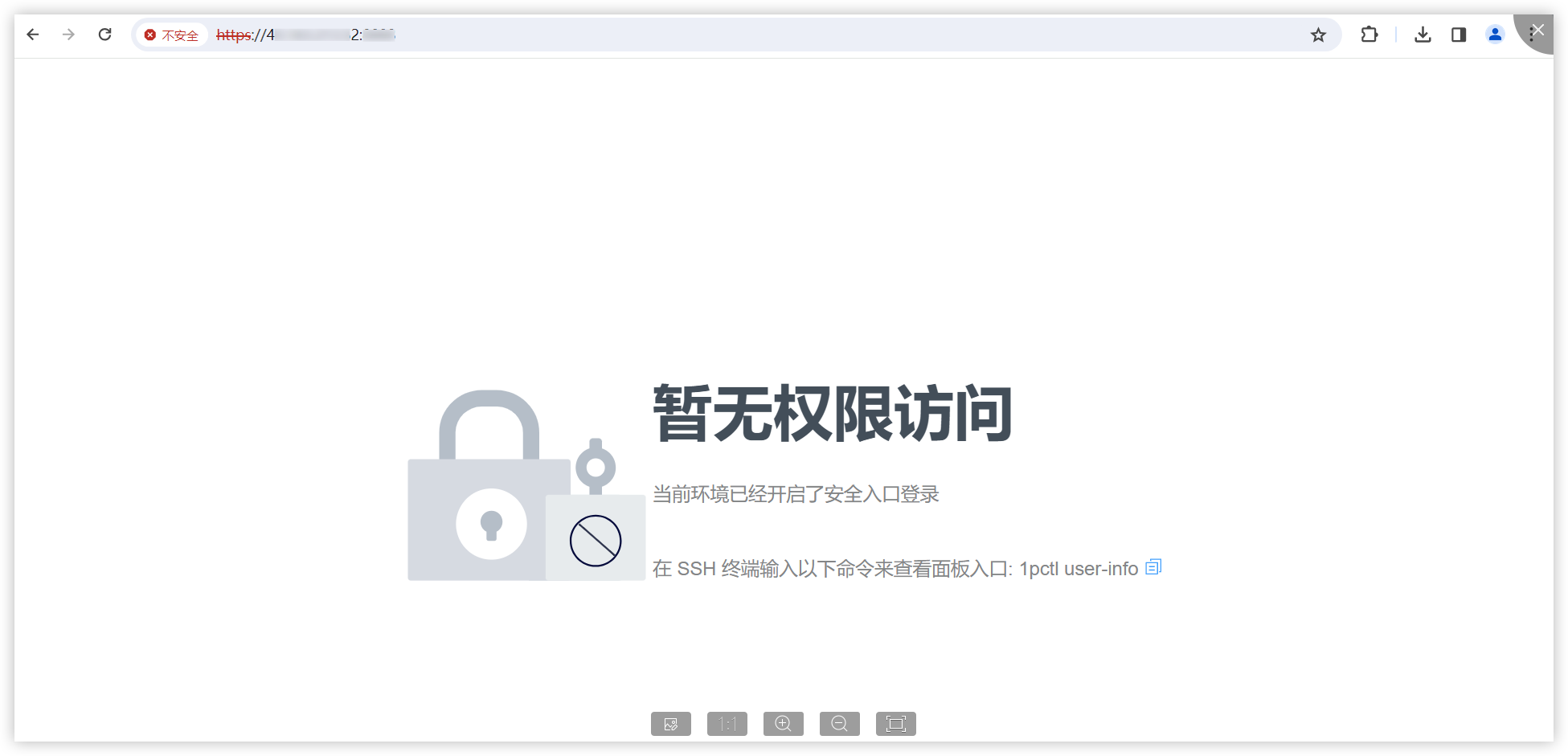 2. Use Burp to intercept: 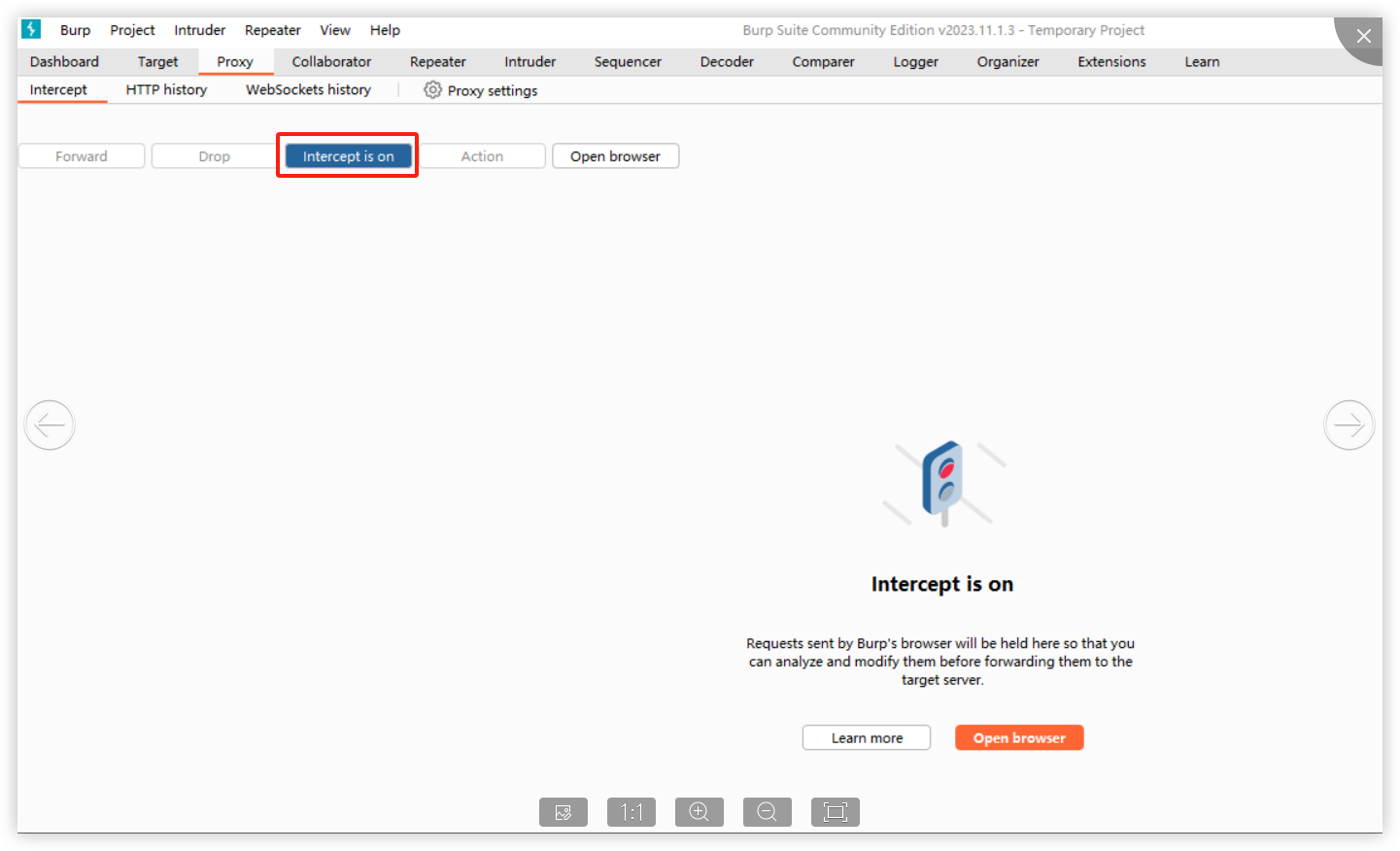 When opening the browser and entering the URL (allowing the first intercepted packet through Burp), the following is displayed: 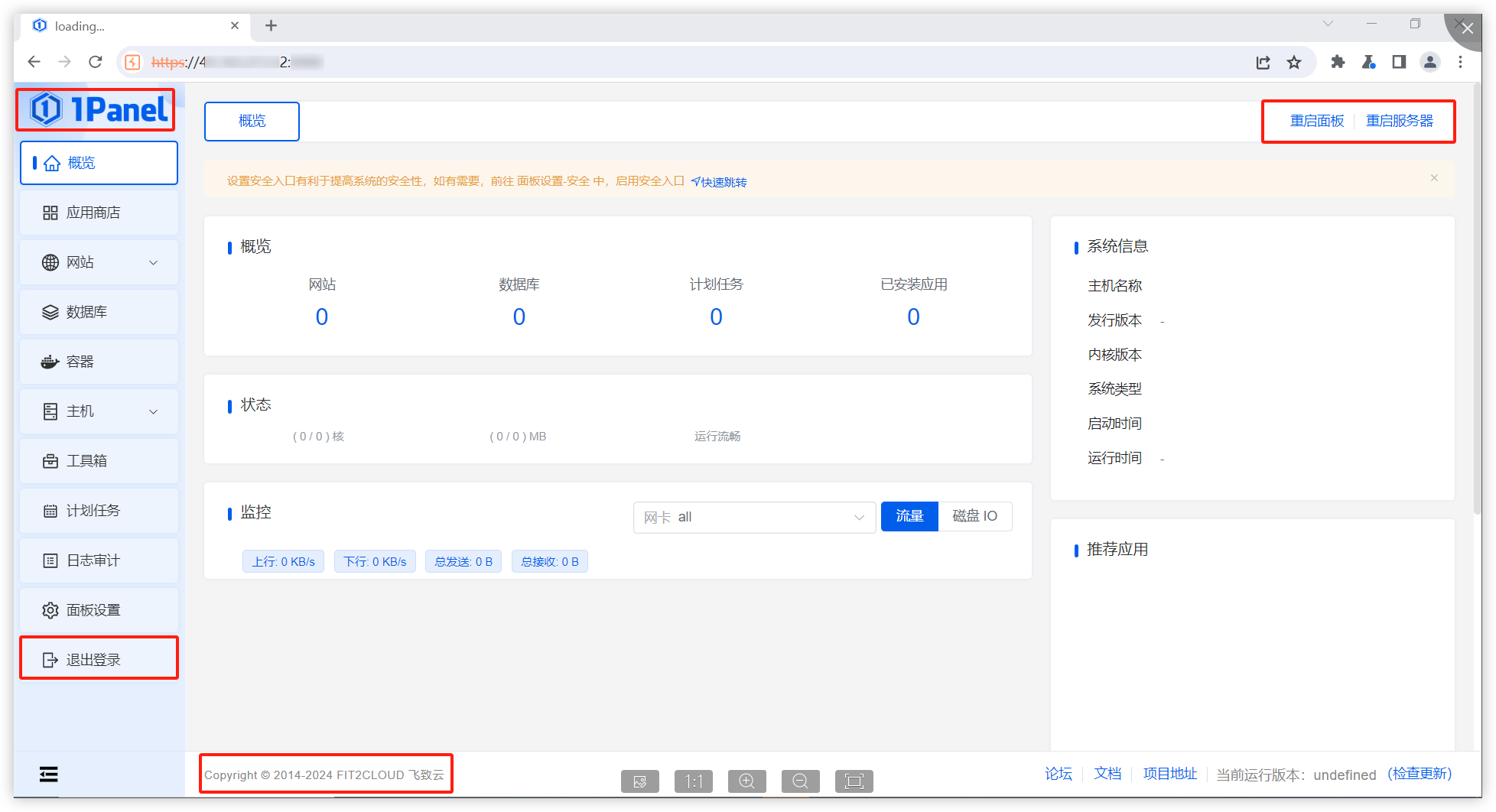 It is found that in this situation, we can access the console page (although no data is returned and no modification operations can be performed)." Affected versions: <= 1.10.0-lts ### Patches The vulnerability has been fixed in v1.10.1-lts. ### Workarounds It is recommended to upgrade the version to 1.10.1-lts. ### References If you have any questions or comments about this advisory: Open ...
### Summary Here it is observed that the CasaOS doesn't defend against password brute force attacks, which leads to having full access to the server. ### Details The web application lacks control over the login attempts i.e. why attacker can use a password brute force attack to find and get full access over the. ### PoC 1. Capture login request in proxy tool like Burp Suite and select password field.  2. Here I have started attack with total number of 271 password tries where the last one is the correct password and as we can see in the following image we get a **400 Bad Request** status code with the message "**Invalid Password**" and response length **769** on 1st request which was sent at **_Tue, 16 Jan 2024 18:31:32 GMT_**  **Note**: _We have tested this vulnerabil...
### Summary The Casa OS Login page has disclosed the username enumeration vulnerability in the login page. ### Details It is observed that the attacker can enumerate the CasaOS username using the application response. If the username is incorrect application gives the error "**User does not exist**", If the password is incorrect application gives the error "**Invalid password**". ### PoC Capture the login request in a tool like Burp Suit and use the intruder tab for trying multiple usernames. Keep checking the response of each request if the response says **Invalid password** then the username is right. ### Impact Using this error attacker can enumerate the username of CasaOS. ### The logic behind the issue If the username is incorrect, then throw an error "User does not exist" else throw an error "Invalid password". This condition can be vice versa like: If the password is incorrect, then throw an error "Invalid password" else throw an error "User does not exist". ### ...
### Summary http://demo.casaos.io/v1/users/image?path=/var/lib/casaos/1/avatar.png Originally it was to get the url of the user's avatar, but the path filtering was not strict, making it possible to get any file on the system. ### Details Construct paths to get any file. Such as the CasaOS user database, and furthermore can obtain system root privileges. ### PoC http://demo.casaos.io/v1/users/image?path=/var/lib/casaos/conf/../db/user.db ### Impact v0.4.6 all previous versions
### Impact The Symfony Session Handler, pop's the Session Cookie and assign it to the Response. Since Shopware 6.5.8.0 the 404 pages, are cached, to improve the performance of 404 pages. So the cached Response, contains a Session Cookie when the Browser accessing the 404 page, has no cookies yet. The Symfony Session Handler is in use, when no explicit Session configuration has been done. When Redis is in use for Sessions using the PHP Redis extension, this exploiting code is not used. ### Patches Update to Shopware version 6.5.8.7 ### Workarounds Using Redis for Sessions, as this does not trigger the exploit code. Example configuration for Redis ```ini # php.ini session.save_handler = redis session.save_path = "tcp://127.0.0.1:6379" ``` ## Consequences As an guest browser session has been cached on a 404 page, every missing image or directly reaching a 404 page will logout the customer or clear his cart.
Deserialization of Untrusted Data vulnerability in Apache InLong.This issue affects Apache InLong: from 1.8.0 through 1.10.0, the attackers can use the specific payload to read from an arbitrary file. Users are advised to upgrade to Apache InLong's 1.11.0 or cherry-pick [1] to solve it. [1] https://github.com/apache/inlong/pull/9673
## Duplicate Advisory This advisory has been withdrawn because it is a duplicate of GHSA-3qx3-6hxr-j2ch. This link is maintained to preserve external references. ## Original Description Buffer Overflow vulnerability in eza before version 0.18.2, allows local attackers to execute arbitrary code via the .git/HEAD, .git/refs, and .git/objects components.
Due to incorrect access control in Plone version v6.0.9, remote attackers can view and list all files hosted on the website via sending a crafted request.
By Deeba Ahmed Group-IB Report Warns of Evolving Cyber Threats Including AI and macOS Vulnerabilities and Ransomware Attacks. This is a post from HackRead.com Read the original post: Report Uncovers Massive Sale of Compromised ChatGPT Credentials
Concrete CMS version 9 before 9.2.7 is vulnerable to Stored XSS via the Name field of a Group type since there is insufficient validation of administrator provided data for that field. A rogue administrator could inject malicious code into the Name field which might be executed when users visit the affected page. The Concrete CMS security team gave this vulnerability a CVSS v3.1 score of 2.2 with a vector of AV:N/AC:H/PR:H/UI:N/S:U/C:L/I:N/A:N Concrete versions below 9 do not include group types so they are not affected by this vulnerability. Thanks Luca Fuda for reporting.