Tag
#php
Ubuntu Security Notice 6757-1 - It was discovered that PHP incorrectly handled PHP_CLI_SERVER_WORKERS variable. An attacker could possibly use this issue to cause a crash or execute arbitrary code. This issue only affected Ubuntu 20.04 LTS, and Ubuntu 22.04 LTS. It was discovered that PHP incorrectly handled certain cookies. An attacker could possibly use this issue to cookie by pass.
Doctor Appointment Management System version 1.0 suffers from a cross site scripting vulnerability.
Ubuntu Security Notice 6751-1 - It was discovered that Zabbix incorrectly handled input data in the discovery and graphs pages. A remote authenticated attacker could possibly use this issue to perform reflected cross-site scripting attacks.
### ECDSA Canonicalization PHPECC is vulnerable to malleable ECDSA signature attacks. ### Constant-Time Signer When generating a new ECDSA signature, the GMPMath adapter was used. This class wraps the GNU Multiple Precision arithmetic library (GMP), which does not aim to provide constant-time implementations of algorithms. An attacker capable of triggering many signatures and studying the time it takes to perform each operation would be able to leak the secret number, `k`, and thereby learn the private key. ### EcDH Timing Leaks When calculating a shared secret using the `EcDH` class, the scalar-point multiplication is based on the arithmetic defined by the `Point` class. Even though the library implements a Montgomery ladder, the `add()`, `mul()`, and `getDouble()` methods on the `Point` class are not constant-time. This means that your ECDH private keys are leaking information about each bit of your private key through a timing side-channel.
SQL injection vulnerability in Zend Framework before 1.12.9, 2.2.x before 2.2.8, and 2.3.x before 2.3.3, when using the sqlsrv PHP extension, allows remote attackers to execute arbitrary SQL commands via a null byte.
A remote code execution vulnerability in Gambio online webshop versions 4.9.2.0 and below allows remote attackers to run arbitrary commands via an unauthenticated HTTP POST request. The identified vulnerability within Gambio pertains to an insecure deserialization flaw, which ultimately allows an attacker to execute remote code on affected systems. The insecure deserialization vulnerability in Gambio poses a significant risk to affected systems. As it allows remote code execution, adversaries could exploit this flaw to execute arbitrary commands, potentially resulting in complete system compromise, data exfiltration, or unauthorized access to sensitive information.
Debian Linux Security Advisory 5670-1 - Multiple security issues were discovered in Thunderbird, which could result in denial of service or the execution of arbitrary code.
### Summary Get a valid API token, make sure you can access api functions, then replace string on my PoC code, Test on offical OVA image, it's a old version 23.9.1, but this vulerable is also exists on latest version 24.2.0 ### Details in file `api_functions.php`, line 307 for function list_devices ```php $order = $request->get('order'); $type = $request->get('type'); $query = $request->get('query'); $param = []; if (empty($order)) { $order = 'hostname'; } if (stristr($order, ' desc') === false && stristr($order, ' asc') === false) { $order = 'd.`' . $order . '` ASC'; } /* ... */ $devices = []; $dev_query = "SELECT $select FROM `devices` AS d $join WHERE $sql GROUP BY d.`hostname` ORDER BY $order"; foreach (dbFetchRows($dev_query, $param) as $device) { ``` The "order" parameter is obtained from $request. After performing a string check, the value is directly incorporated into an SQL statement and concatenated, resulting in...
### Summary There is improper sanitization on Service template name which is reflecting in delete button onclick event. This value can be modified and crafted as any other javascript code. ### Vulnerable Code https://github.com/librenms/librenms/blob/a61c11db7e8ef6a437ab55741658be2be7d14d34/app/Http/Controllers/ServiceTemplateController.php#L67C23-L67C23 Above is vulnerable code line which needs to be properly sanitized ### PoC 1. Go to /services/templates 2. Enter name as `testing', '14', 'http://172.105.62.194:8000/services/templates/14');alert(1);//` 3. Submit it and try to delete it, you will see popup If you inspect element on delete button, you will notice this:- <img width="748" alt="Screenshot 2023-11-23 at 9 30 24 PM" src="https://user-images.githubusercontent.com/31764504/285260018-7672a93d-e29b-4444-8057-e6ffcb8dabfc.png"> ### Impact Cross site scripting can lead to cookie stealing or an attacker can execute any other feature using this feature.
### Summary SQL injection vulnerability in POST /search/search=packages in LibreNMS 24.3.0 allows a user with global read privileges to execute SQL commands via the package parameter. ### Details There is a lack of hygiene of data coming from the user in line 83 of the file librenms/includes/html/pages/search/packages.inc.php 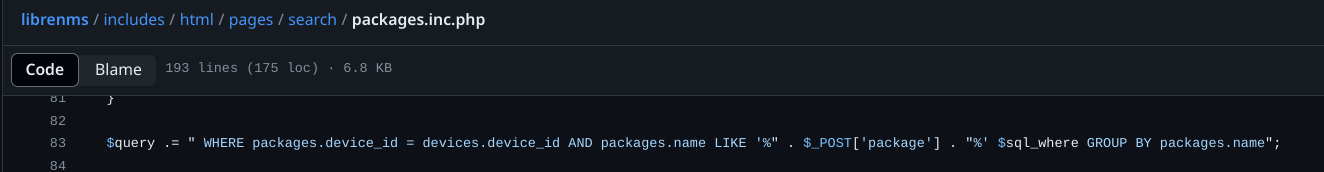 ### PoC https://doc.clickup.com/9013166444/p/h/8ckm0bc-53/16811991bb5fff6 ### Impact With this vulnerability, we can exploit a SQL injection time based vulnerability to extract all data from the database, such as administrator credentials