Tag
#auth
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added two security flaws impacting Palo Alto Networks PAN-OS and SonicWall SonicOS SSLVPN to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The flaws are listed below - CVE-2025-0108 (CVSS score: 7.8) - An authentication bypass vulnerability in the Palo Alto Networks PAN-OS
The campaign heavily uses Dropbox folders and PowerShell scripts to evade detection and quickly scrapped infrastructure components after researchers began poking around.
Acquisition strengthens Deepwatch Platform capabilities with actionable insights and risk-based prioritization.
A new report reveals how cheap Infostealer malware is exposing US military and defense data, putting national security at risk. Hackers exploit human error to gain access.
Attackers are using patched bugs to potentially gain unfettered access to an organization's Windows environment under certain conditions.
Winnti once used a variety of malware but is now focused on SQL vulnerabilities and obfuscation, updated encryption, and new evasion methods to gain access.
### Description Authentication using Spid and CIE is based on the SAML2 standard which provides for two entities: Identity Provider (IdP): the system that authenticates users and provides identity information ( SAML assertions ) to the Service Provider, essentially, it is responsible for managing user credentials and identity; Service Provider (SP): The system that provides a service to the user and relies on the Identity Provider to authenticate the user, receives SAML assertions from the IdP to grant access to resources. The library `cie-aspnetcorerefers` to the second entity, i.e. the SP, and implements the validation logic of the SAML assertions present within the SAML response . The following is a summary diagram of an authentication flow via SAML: 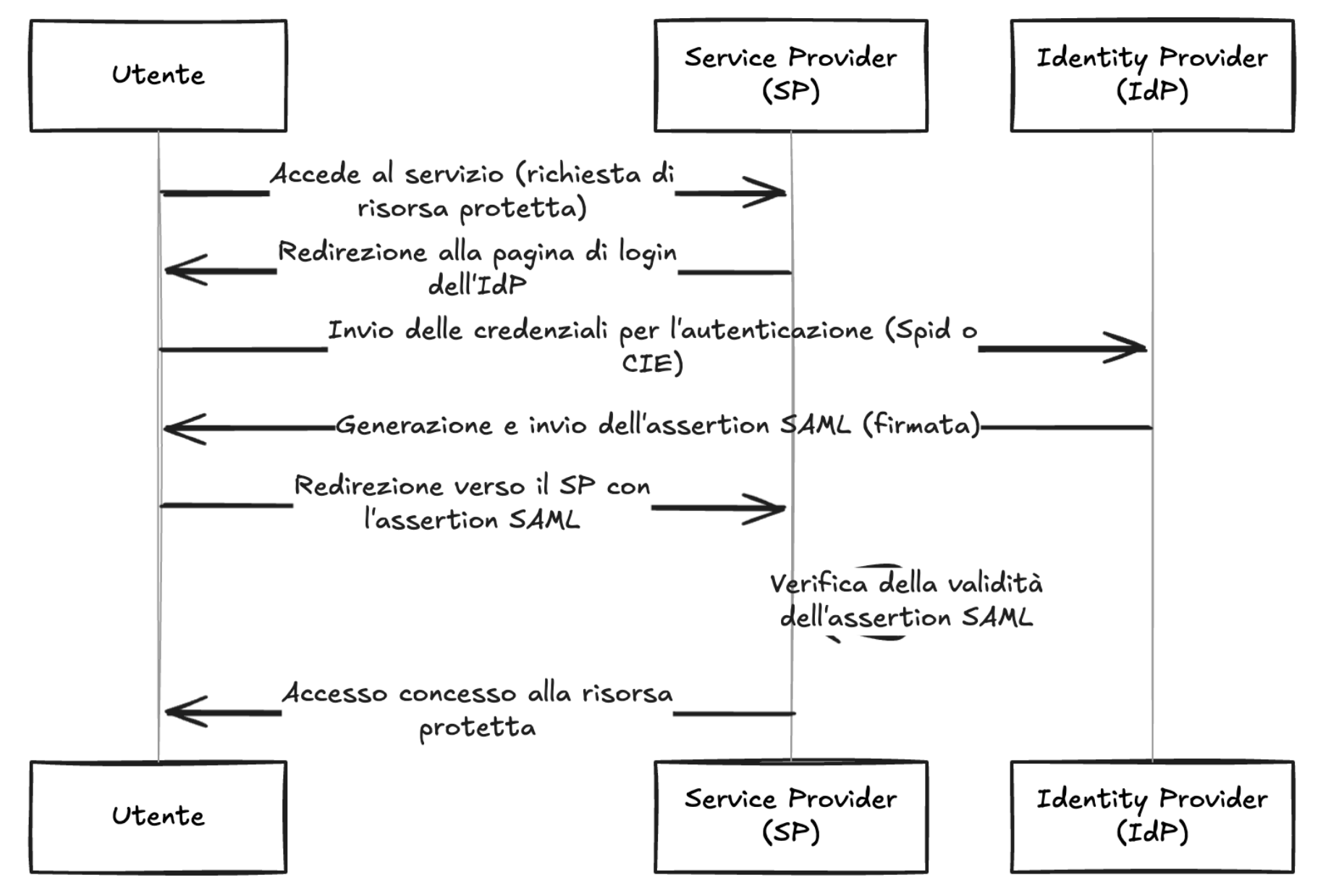 As shown in the diagram, the IdP, after verifying the user's credentials, generates a signed SAML response, this is propagated to the SP by the use...
### Description Authentication using Spid and CIE is based on the SAML2 standard which provides for two entities: Identity Provider (IdP): the system that authenticates users and provides identity information ( SAML assertions ) to the Service Provider, essentially, it is responsible for managing user credentials and identity; Service Provider (SP): The system that provides a service to the user and relies on the Identity Provider to authenticate the user, receives SAML assertions from the IdP to grant access to resources. The library `spid-aspnetcorerefers` to the second entity, i.e. the SP, and implements the validation logic of the SAML assertions present within the SAML response . The following is a summary diagram of an authentication flow via SAML:  As shown in the diagram, the IdP, after verifying the user's credentials, generates a signed SAML response, this is propagated to the SP by the us...
Microsoft is warning the modular and potentially wormable Apple-focused infostealer boasts new capabilities for obfuscation, persistence, and infection, and could lead to a supply chain attack.
Carding -- the underground business of stealing, selling and swiping stolen payment card data -- has long been the dominion of Russia-based hackers. Happily, the broad deployment of more secure chip-based payment cards in the United States has weakened the carding market. But a flurry of innovation from cybercrime groups in China is breathing new life into the carding industry, by turning phished card data into mobile wallets that can be used online and at main street stores.