Tag
#auth
Multilaser RE160V web management interface versions 12.03.01.08_pt and 12.03.01.09_pt along with RE160 versions 5.07.51_pt_MTL01 and 5.07.52_pt_MTL01 suffer from an access control bypass vulnerability through URL manipulation.
Multilaser RE160V web management interface versions 12.03.01.09_pt and 12.03.01.10_pt suffer from an access control bypass vulnerability through header manipulation.
A-PDF All to MP3 Converter version 2.0.0 overflow exploit with DEP Bypass with HeapCreate + HeapAlloc + some_memory_copy_function ROP chain.
By Deeba Ahmed It is unclear how much the hacker received as part of the Facebook bug bounty program. This is a post from HackRead.com Read the original post: Nepali Hacker Tops Hall of Fame by Exposing Facebook’s Zero-Click Flaw
Any SpiceDB cluster with any schema where a resource being checked has more than 65535 relationships for the same resource and subject type is affected by this problem. The issue may also lead to a panic rendering the server unavailable The following API methods are affected: - [CheckPermission](https://buf.build/authzed/api/docs/main:authzed.api.v1#authzed.api.v1.PermissionsService.CheckPermission) - [BulkCheckPermission](https://buf.build/authzed/api/docs/main:authzed.api.v1#authzed.api.v1.ExperimentalService.BulkCheckPermission) - [LookupSubjects](https://buf.build/authzed/api/docs/main:authzed.api.v1#authzed.api.v1.PermissionsService.LookupSubjects) #### Impact Permission checks that are expected to be allowed are instead denied, and lookup subjects will return fewer subjects than expected. #### Workarounds There is no workaround other than making sure that the SpiceDB cluster does not have very wide relations, with the maximum value being the maximum value of an 16-bit unsig...
By Deeba Ahmed Russia Tightens Grip on Internet Freedom: VPN Ban Sparks Concerns. This is a post from HackRead.com Read the original post: Russia Clamps Down on VPNs, Furthering Restrictions on Internet Access
### Impact Currently the exact Directus version number is being shipped in compiled JS bundles which are accessible without authentication. With this information a malicious attacker can trivially look for known vulnerabilities in Directus core or any of its shipped dependencies in that specific running version. ### Patches The problem has been resolved in versions 10.8.3 and newer ### Workarounds None
### Summary Security misconfiguration in edit configuration file API in dashboard component of ESPHome version 2023.12.9 (command line installation) allows authenticated remote attackers to read and write arbitrary files under the configuration directory rendering remote code execution possible. ### Details It is possible to abuse this path traversal vulnerability both in command line installation and Home Assistant add-on, but it is possible to read and write files only under the configuration directory. The vulnerability is present and exploitable in the command line installation, but it was not possible to confirm an impact in the home assistant add-on version. ### PoC <img width="482" alt="/edit?configuration=/config/.esphome/esphome.json" src="https://github.com/esphome/esphome/assets/115887876/d2da3180-976e-4bed-b4b9-35ac960a7fb4"> <br/> <img width="344" alt="/edit?configuration=/config/.esphome/build/test01/src/main.cpp (firmware for board named test01)" src="https://github...
### Impact Previously, budibase used a library called `vm2` for code execution inside the Budibase builder and apps, such as the UI below for configuring bindings in the design section. 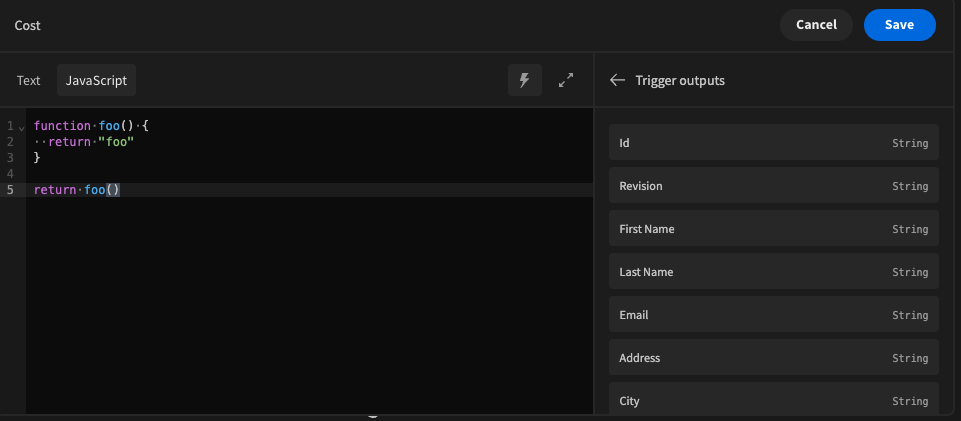 Due to a [vulnerability in vm2](https://github.com/advisories/GHSA-cchq-frgv-rjh5), any environment that executed the code server side (automations and column formulas) was susceptible to this vulnerability, allowing users to escape the sandbox provided by `vm2`, and to expose server side variables such as `process.env`. It's recommended by the authors of `vm2` themselves that you should move to another solution for remote JS execution due to this vulnerability. ### Patches We moved our entire JS sandbox infrastructure over to `isolated-vm`, a much more secure and recommended library for remote code execution in 2.20.0. This also comes with a performance benefit in the way w...
** UNSUPPORTED WHEN ASSIGNED ** Incorrect Authorization vulnerability in Apache Archiva. Apache Archiva has a setting to disable user registration, however this restriction can be bypassed. As Apache Archiva has been retired, we do not expect to release a version of Apache Archiva that fixes this issue. You are recommended to look into migrating to a different solution, or isolate your instance from any untrusted users. NOTE: This vulnerability only affects products that are no longer supported by the maintainer