Tag
#git
### Impact KaTeX users who render untrusted mathematical expressions could encounter malicious input using `\edef` that causes a near-infinite loop, despite setting `maxExpand` to avoid such loops. This can be used as an availability attack, where e.g. a client rendering another user's KaTeX input will be unable to use the site due to memory overflow, tying up the main thread, or stack overflow. ### Patches Upgrade to KaTeX v0.16.10 to remove this vulnerability. ### Workarounds Forbid inputs containing the substring `"\\edef"` before passing them to KaTeX. (There is no easy workaround for the auto-render extension.) ### Details KaTeX supports an option named `maxExpand` which prevents infinitely recursive macros from consuming all available memory and/or triggering a stack overflow error. However, what counted as an "expansion" is a single macro expanding to any number of tokens. The expand-and-define TeX command `\edef` can be used to build up an exponential number of tokens using ...
subprocess call with shell=True identified, security issue. #### Code On file [src/ansys/geometry/core/connection/product_instance.py](https://github.com/ansys/pyansys-geometry/blob/52cba1737a8a7812e5430099f715fa2160ec007b/src/ansys/geometry/core/connection/product_instance.py#L403-L428): ``` 403 def _start_program(args: List[str], local_env: Dict[str, str]) -> subprocess.Popen: 404 """ 405 Start the program where the path is the first item of the ``args`` array argument. 406 407 Parameters 408 ---------- 409 args : List[str] 410 List of arguments to be passed to the program. The first list's item shall 411 be the program path. 412 local_env : Dict[str,str] 413 Environment variables to be passed to the program. 414 415 Returns 416 ------- 417 subprocess.Popen 418 The subprocess object. 419 """ 420 return subprocess.Popen( 421 args, 422 shell=os.name != "nt", 423 stdin=subprocess.DEVN...
An issue was discovered in RDoc 6.3.3 through 6.6.2, as distributed in Ruby 3.x through 3.3.0. When parsing `.rdoc_options` (used for configuration in RDoc) as a YAML file, object injection and resultant remote code execution are possible because there are no restrictions on the classes that can be restored. When loading the documentation cache, object injection and resultant remote code execution are also possible if there were a crafted cache. We recommend to update the RDoc gem to version 6.6.3.1 or later. In order to ensure compatibility with bundled version in older Ruby series, you may update as follows instead: * For Ruby 3.0 users: Update to `rdoc` 6.3.4.1 * For Ruby 3.1 users: Update to `rdoc` 6.4.1.1 * For Ruby 3.2 users: Update to `rdoc` 6.5.1.1 You can use `gem update rdoc` to update it. If you are using bundler, please add `gem "rdoc", ">= 6.6.3.1"` to your `Gemfile`. Note: 6.3.4, 6.4.1, 6.5.1 and 6.6.3 have a incorrect fix. We recommend to upgrade 6.3.4.1, 6.4.1.1, ...
An issue was discovered in StringIO 3.0.1, as distributed in Ruby 3.0.x through 3.0.6 and 3.1.x through 3.1.4. The `ungetbyte` and `ungetc` methods on a StringIO can read past the end of a string, and a subsequent call to `StringIO.gets` may return the memory value. This vulnerability is not affected StringIO 3.0.3 and later, and Ruby 3.2.x and later. We recommend to update the StringIO gem to version 3.0.3 or later. In order to ensure compatibility with bundled version in older Ruby series, you may update as follows instead: * For Ruby 3.0 users: Update to `stringio` 3.0.1.1 * For Ruby 3.1 users: Update to `stringio` 3.1.0.2 You can use `gem update stringio` to update it. If you are using bundler, please add `gem "stringio", ">= 3.0.1.2"` to your `Gemfile`.
### Summary There is a Path Traversal vulnerability in Attachments that allows attackers with admin rights to upload malicious files to other locations of the web root. ### PoC 1. In settings, the attachment location is vulnerable to path traversal and can be set to e.g ..\hacked 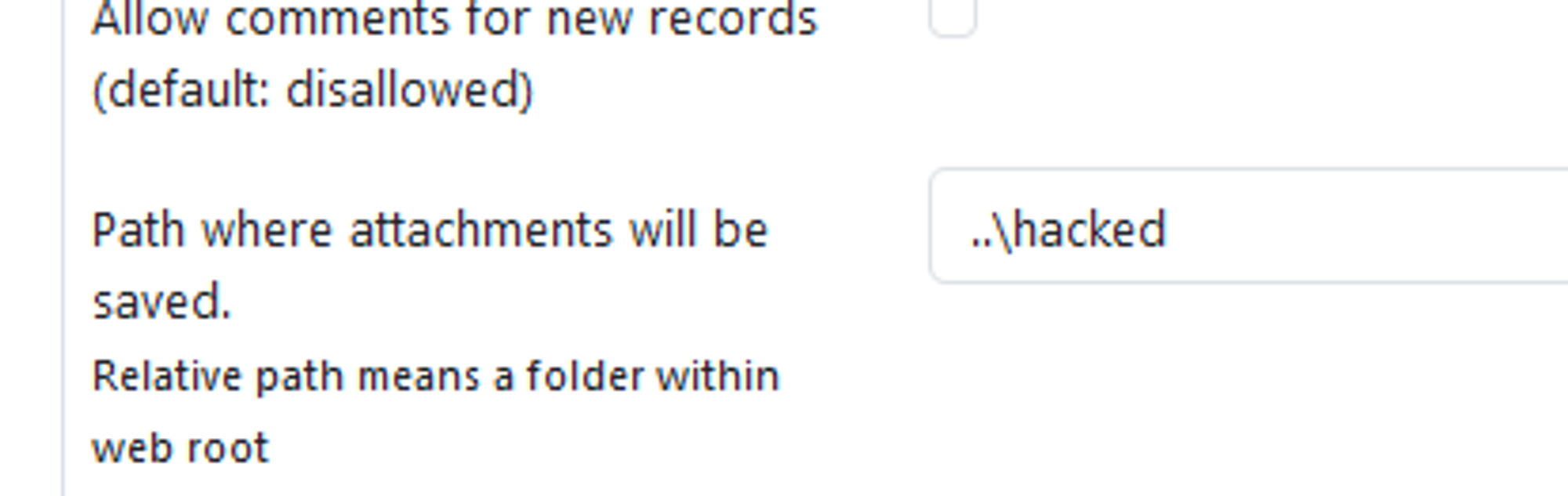 2. When the above is set, attachments files are now uploaded to e.g C:\Apps\XAMPP\htdocs\hacked instead of C:\Apps\XAMPP\htdocs\phpmyfaq\attachments 3. Verify this by uploading an attachment and see that the "hacked" directory is now created in the web root folder with the attachment file inside. 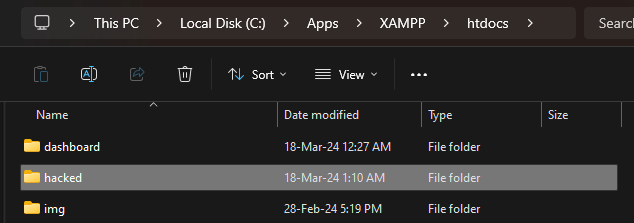 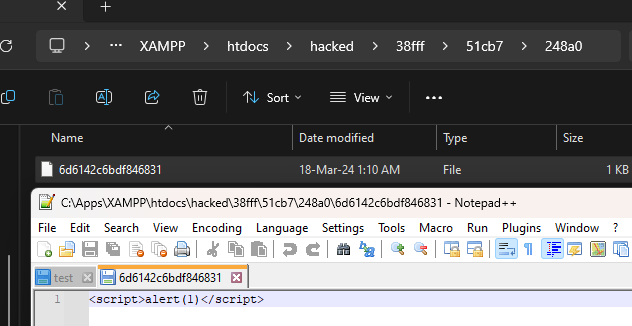 ### Impact Attackers can potentially upload malicious files outside the specified directory.
An issue in @thi.ng/paths v.5.1.62 and before allows a remote attacker to execute arbitrary code via the `mutIn` and `mutInManyUnsafe` components.
By Deeba Ahmed New Dark Web Tool GEOBOX, sold for $700 on Telegram and underground forums, hijacks Raspberry Pi, allowing cybercriminals to fake locations and evade detection. This is a post from HackRead.com Read the original post: New GEOBOX Tool Hijacks Raspberry Pi, Lets Hackers Fake Location
Unidentified adversaries orchestrated a sophisticated attack campaign that has impacted several individual developers as well as the GitHub organization account associated with Top.gg, a Discord bot discovery site. "The threat actors used multiple TTPs in this attack, including account takeover via stolen browser cookies, contributing malicious code with verified commits, setting up a custom
By Owais Sultan Entering the dynamic world of cryptocurrencies is pretty exciting. But one can easily get overwhelmed with the amount… This is a post from HackRead.com Read the original post: Step-by-Step Guide to Creating Your First Crypto Wallet
The Iran-affiliated threat actor tracked as MuddyWater (aka Mango Sandstorm or TA450) has been linked to a new phishing campaign in March 2024 that aims to deliver a legitimate Remote Monitoring and Management (RMM) solution called Atera. The activity, which took place from March 7 through the week of March 11, targeted Israeli entities spanning global manufacturing, technology, and