Tag
#js
### Description Authentication using Spid and CIE is based on the SAML2 standard which provides for two entities: Identity Provider (IdP): the system that authenticates users and provides identity information ( SAML assertions ) to the Service Provider, essentially, it is responsible for managing user credentials and identity; Service Provider (SP): The system that provides a service to the user and relies on the Identity Provider to authenticate the user, receives SAML assertions from the IdP to grant access to resources. The library `cie-aspnetcorerefers` to the second entity, i.e. the SP, and implements the validation logic of the SAML assertions present within the SAML response . The following is a summary diagram of an authentication flow via SAML: 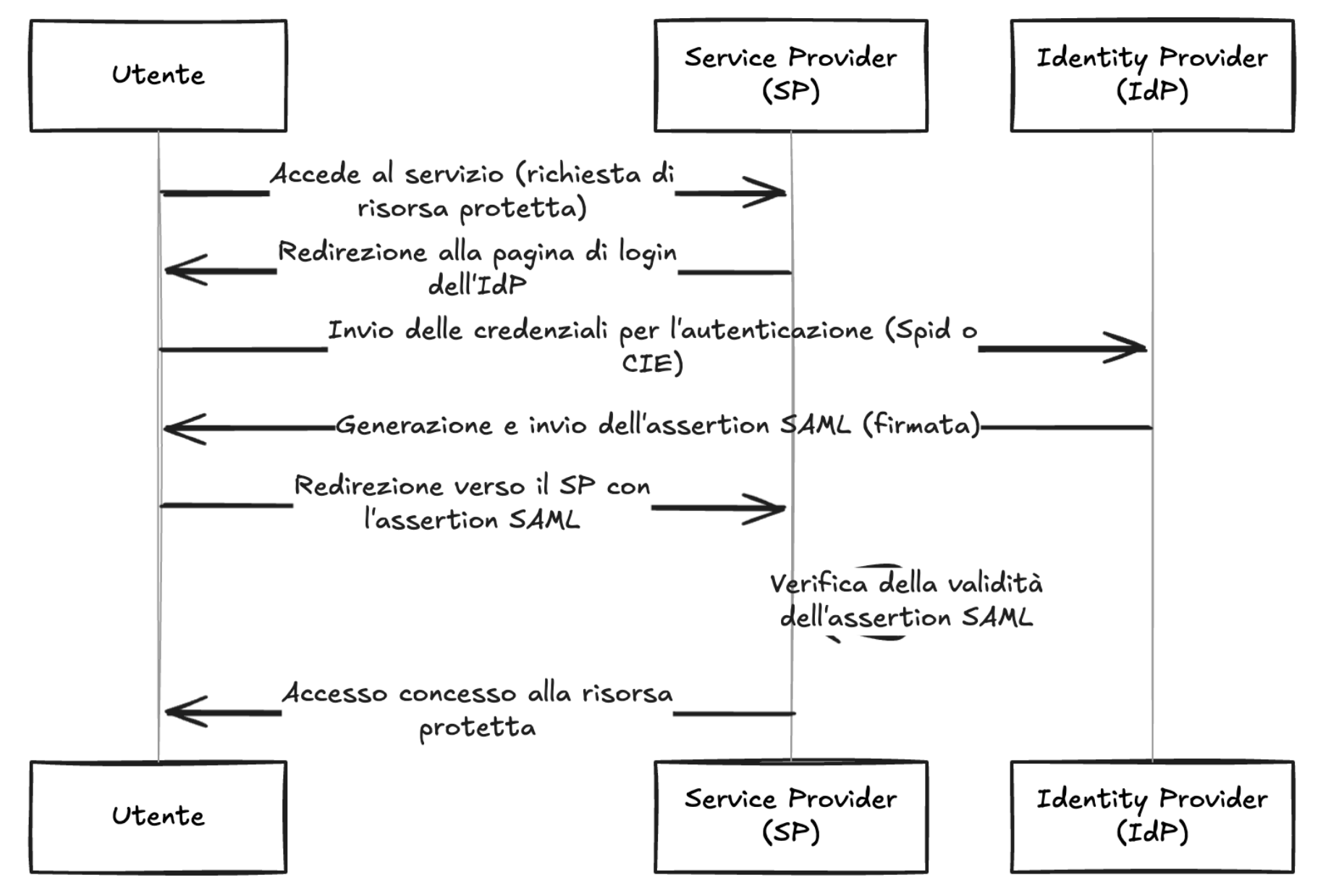 As shown in the diagram, the IdP, after verifying the user's credentials, generates a signed SAML response, this is propagated to the SP by the use...
### Description Authentication using Spid and CIE is based on the SAML2 standard which provides for two entities: Identity Provider (IdP): the system that authenticates users and provides identity information ( SAML assertions ) to the Service Provider, essentially, it is responsible for managing user credentials and identity; Service Provider (SP): The system that provides a service to the user and relies on the Identity Provider to authenticate the user, receives SAML assertions from the IdP to grant access to resources. The library `spid-aspnetcorerefers` to the second entity, i.e. the SP, and implements the validation logic of the SAML assertions present within the SAML response . The following is a summary diagram of an authentication flow via SAML:  As shown in the diagram, the IdP, after verifying the user's credentials, generates a signed SAML response, this is propagated to the SP by the us...
Versions of the package jsonpath-plus before 10.3.0 are vulnerable to Remote Code Execution (RCE) due to improper input sanitization. An attacker can execute aribitrary code on the system by exploiting the unsafe default usage of eval='safe' mode. **Note:** This is caused by an incomplete fix for CVE-2024-21534.
### Summary The regular expression `/<([^>]+)>; rel="deprecation"/` used to match the `link` header in HTTP responses is vulnerable to a ReDoS (Regular Expression Denial of Service) attack. This vulnerability arises due to the unbounded nature of the regex's matching behavior, which can lead to catastrophic backtracking when processing specially crafted input. An attacker could exploit this flaw by sending a malicious `link` header, resulting in excessive CPU usage and potentially causing the server to become unresponsive, impacting service availability. ### Details The vulnerability resides in the regular expression `/<([^>]+)>; rel="deprecation"/`, which is used to match the `link` header in HTTP responses. This regular expression captures content between angle brackets (`<>`) followed by `; rel="deprecation"`. However, the pattern is vulnerable to ReDoS (Regular Expression Denial of Service) attacks due to its susceptibility to catastrophic backtracking when processing malicious inp...
### Summary A Regular Expression Denial of Service (ReDoS) vulnerability exists in the processing of HTTP request headers. By sending an authorization header containing an excessively long sequence of spaces followed by a newline and "@", an attacker can exploit inefficient regular expression processing, leading to excessive resource consumption. This can significantly degrade server performance or cause a denial-of-service (DoS) condition, impacting availability. ### Details The issue occurs at [line 52](https://github.com/octokit/request-error.js/blob/main/src/index.ts) of iterator.ts in the @octokit/request-error repository. The vulnerability is caused by the use of an inefficient regular expression in the handling of the `authorization` header within the request processing logic: ```js authorization: options.request.headers.authorization.replace( / .*$/, " [REDACTED]" ) ``` The regular expression `/ .*$/` matches a space followed by any number of characters until the end of th...
### Summary For the npm package `@octokit/plugin-paginate-rest`, when calling `octokit.paginate.iterator()`, a specially crafted `octokit` instance—particularly with a malicious `link` parameter in the `headers` section of the `request`—can trigger a ReDoS attack. ### Details The issue occurs at [line 39](https://github.com/octokit/plugin-paginate-rest.js/blob/main/src/iterator.ts) of iterator.ts in the @octokit/plugin-paginate-rest repository. The relevant code is as follows: ```js url = ((normalizedResponse.headers.link || "").match( /<([^>]+)>;\s*rel="next"/, ) || [])[1]; ``` The regular expression `/<([^>]+)>;\s*rel="next"/` may lead to a potential backtracking vulnerability, resulting in a ReDoS (Regular Expression Denial of Service) attack. This could cause high CPU utilization and even service slowdowns or freezes when processing specially crafted `Link` headers. ### PoC [The gist of PoC.js](https://gist.github.com/ShiyuBanzhou/d3f2ad000be8384d2105c87c2ed7ce7d) 1. run npm i ...
### Summary By crafting specific `options` parameters, the `endpoint.parse(options)` call can be triggered, leading to a regular expression denial-of-service (ReDoS) attack. This causes the program to hang and results in high CPU utilization. ### Details The issue occurs in the `parse` function within the `parse.ts` file of the npm package `@octokit/endpoint`. The specific code is located at the following link: https://github.com/octokit/endpoint.js/blob/main/src/parse.ts, at line 62: ```ts headers.accept.match(/[\w-]+(?=-preview)/g) || ([] as string[]); ``` The regular expression `/[\w-]+(?=-preview)/g` encounters a backtracking issue when it processes `a large number of characters` followed by the `-` symbol. e.g., the attack string: ```js "" + "A".repeat(100000) + "-" ``` ### PoC [The gist](https://gist.github.com/ShiyuBanzhou/a17202ac1ad403a80ca302466d5e56c4) Here is the reproduction process for the vulnerability: 1. run 'npm i @octokit/endpoint' 2. Move `poc.js` to the root dir...
### Summary The `vlSelectionTuples` function can be used to call JavaScript functions, leading to XSS. ### Details [`vlSelectionTuples`](https://github.com/vega/vega/blob/b45cf431cd6c0d0c0e1567f087f9b3b55bc236fa/packages/vega-selections/src/selectionTuples.js#L14) calls multiple functions that can be controlled by an attacker, including one call with an attacker-controlled argument. Example call: `vlSelectionTuples([{datum:<argument>}], {fields:[{getter:<function>}]})` This can be used to call `Function()` with arbitrary JavaScript and the resulting function can be called with `vlSelectionTuples` or using a type coercion to call `toString` or `valueOf`. ### PoC ``` {"$schema":"https://vega.github.io/schema/vega/v5.json","signals":[{"name":"a","init":"+{valueOf:vlSelectionTuples([{datum:'alert(1)'}],{fields:[{getter:[].at.constructor}]})[0].values[0]}"}]} ```
A vulnerability exists due to an insecure backup.tgz file that, when obtained, contains sensitive system files, including main.db, SSL/TLS certificates and keys, the system shadow file with hashed passwords, and the license key. Although authentication is required to access the backup, an attacker with access could extract these files to retrieve stored credentials, decrypt secure communications, and escalate privileges by cracking password hashes. This exposure poses a significant security risk, potentially leading to unauthorized access, data breaches, and full system compromise.
A timing attack vulnerability exists in ABB Cylon FLXeon's authentication process due to improper comparison of password hashes in login.js and uukl.js. Specifically, the verifyPassword() function in login.js and the verify() function in uukl.js both calculate the password hash and compare it to the stored hash. In these implementations, small differences in response times are introduced based on how much of the password or the username matches the stored hash, making the system vulnerable to timing-based analysis.