Tag
#php
### Summary A SQL injection vulnerability has been discovered in the the "Add News" functionality due to improper escaping of the email address. This allows any authenticated user with the rights to add/edit FAQ news to exploit this vulnerability to exfiltrate data, take over accounts and in some cases, even achieve RCE. ### Details The vulnerable field lies in the `authorEmail` field which uses PHP's `FILTER_VALIDATE_EMAIL` filter. This filter is insufficient in protecting against SQL injection attacks and should still be properly escaped. However, in this version of phpMyFAQ (3.2.5), this field is not escaped properly can be used together with other fields to fully exploit the SQL injection vulnerability. ### PoCs 4 PoCs are demonstrated here to illustrate the potential impacts. #### PoC 1 - Postgres Time Based SQLi 1. Login as admin or any user with the rights to view and save news. 2. Navigate to "../phpmyfaq/admin/?action=news", click on "Add news", fill in some data, send and...
### Impact WP Crontrol includes a feature that allows administrative users to create events in the WP-Cron system that store and execute PHP code [subject to the restrictive security permissions documented here](https://wp-crontrol.com/docs/php-cron-events/). While there is _no known vulnerability in this feature on its own_, there exists potential for this feature to be vulnerable to RCE if it were specifically targeted via vulnerability chaining that exploited a separate SQLi (or similar) vulnerability. This is exploitable on a site if one of the below preconditions are met: * The site is vulnerable to a writeable SQLi vulnerability in any plugin, theme, or WordPress core * The site's database is compromised at the hosting level * The site is vulnerable to a method of updating arbitrary options in the `wp_options` table * The site is vulnerable to a method of triggering an arbitrary action, filter, or function with control of the parameters ### Patches As a hardening measure, WP...
### Impact Logged in user can access page state data of pinned pages of other users by pageId hash. ### Patch ```patch --- src/Oro/Bundle/NavigationBundle/Controller/Api/PagestateController.php +++ src/Oro/Bundle/NavigationBundle/Controller/Api/PagestateController.php @@ -158,6 +158,13 @@ AbstractPageState::generateHash($this->get('request_stack')->getCurrentRequest()->get('pageId')) ); + if ($entity) { + $entity = $this->getEntity($entity->getId()); + } + if (!$entity) { + return $this->handleNotFound(); + } + return $this->handleView($this->view($this->getState($entity), Response::HTTP_OK)); } ```
### Summary There is a Path Traversal vulnerability in Attachments that allows attackers with admin rights to upload malicious files to other locations of the web root. ### PoC 1. In settings, the attachment location is vulnerable to path traversal and can be set to e.g ..\hacked 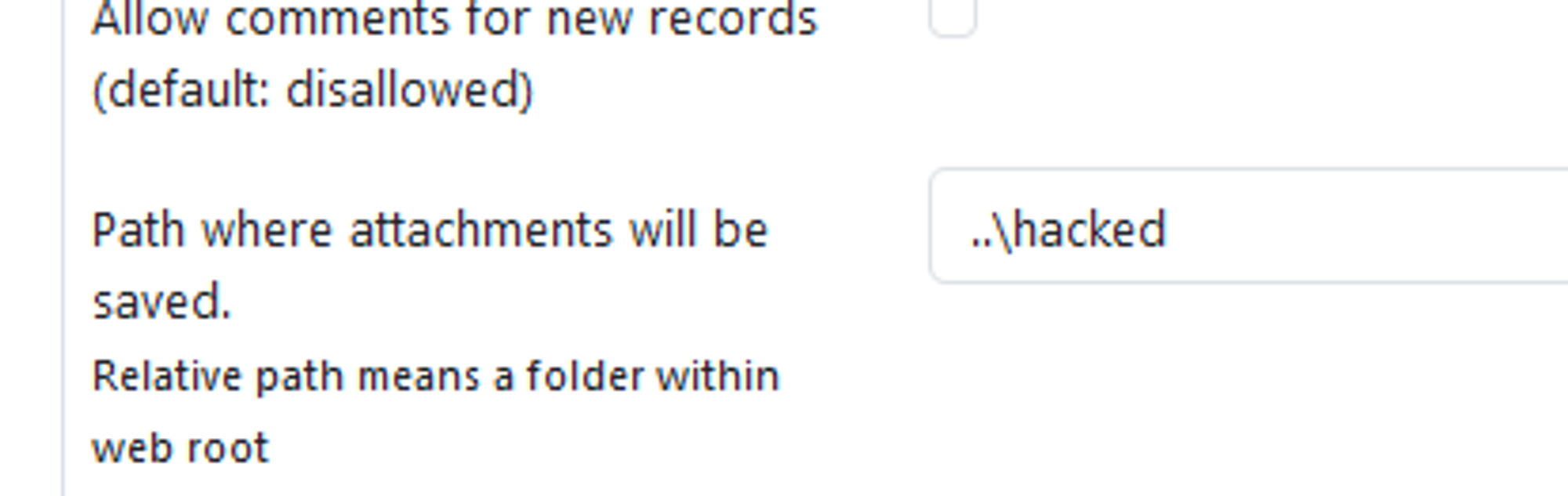 2. When the above is set, attachments files are now uploaded to e.g C:\Apps\XAMPP\htdocs\hacked instead of C:\Apps\XAMPP\htdocs\phpmyfaq\attachments 3. Verify this by uploading an attachment and see that the "hacked" directory is now created in the web root folder with the attachment file inside. 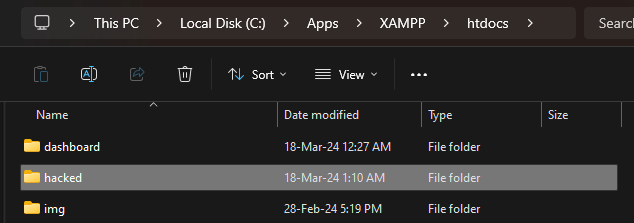 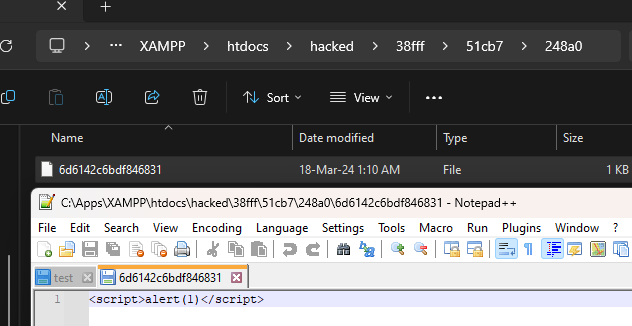 ### Impact Attackers can potentially upload malicious files outside the specified directory.
A malicious ad for the popular admin tool PuTTY leads victims to a fake site that downloads malware.
Win32.STOP.Ransomware (smokeloader) malware suffers from both local and remote code execution vulnerabilities. The remote code execution can be achieved by leveraging a man-in-the-middle attack.
Task Management System version 1.0 suffers from multiple remote SQL injection vulnerabilities.
## Impacted Resources bref/src/Event/Http/Psr7Bridge.php:94-125 multipart-parser/src/StreamedPart.php:383-418 ## Description When Bref is used with the Event-Driven Function runtime and the handler is a `RequestHandlerInterface`, then the Lambda event is converted to a PSR7 object. During the conversion process, if the request is a MultiPart, each part is parsed. In the parsing process, the `Content-Type` header of each part is read using the [`Riverline/multipart-parser`](https://github.com/Riverline/multipart-parser/) library. The library, in the `StreamedPart::parseHeaderContent` function, performs slow multi-byte string operations on the header value. Precisely, the [`mb_convert_encoding`](https://www.php.net/manual/en/function.mb-convert-encoding.php) function is used with the first (`$string`) and third (`$from_encoding`) parameters read from the header value. ## Impact An attacker could send specifically crafted requests which would force the server into performing long op...
### Summary Symfony 1 has a gadget chain due to dangerous unserialize in `sfNamespacedParameterHolder` class that would enable an attacker to get remote code execution if a developer unserialize user input in his project. ### Details This vulnerability present no direct threat but is a vector that will enable remote code execution if a developper deserialize user untrusted data. For example: ```php public function executeIndex(sfWebRequest $request) { $a = unserialize($request->getParameter('user')); } ``` We will make the assumption this is the case in the rest of this explanation. Symfony 1 provides the class `sfNamespacedParameterHolder` which implements `Serializable` interface. In particular, when an instance of this class is deserialized, the normal php behavior is hooked by implementing `unserialize()` method: ```php public function unserialize($serialized) { $this->__unserialize(unserialize($serialized)); } ``` Which make an array access on the ...
### Summary Due to the unrestricted access to twig extension class from grav context, an attacker can redefine the escape function and execute arbitrary commands. ### Details https://github.com/twigphp/Twig/blob/3.x/src/Extension/EscaperExtension.php#L99 ```php /** * Defines a new escaper to be used via the escape filter. * * @param string $strategy The strategy name that should be used as a strategy in the escape call * @param callable $callable A valid PHP callable */ public function setEscaper($strategy, callable $callable) { $this->escapers[$strategy] = $callable; } ``` Twig supports the functionality to redefine the escape function through the setEscaper method. However, that method is not originally exposed to the twig environment, but it is accessible through the payload below. ```plaintext {{ grav.twig.twig.extensions.core.setEscaper('a','a') }} ``` At this point, it accepts callable type as an argument, but as there is no val...