Tag
#web
Winnti once used a variety of malware but is now focused on SQL vulnerabilities and obfuscation, updated encryption, and new evasion methods to gain access.
### Description Authentication using Spid and CIE is based on the SAML2 standard which provides for two entities: Identity Provider (IdP): the system that authenticates users and provides identity information ( SAML assertions ) to the Service Provider, essentially, it is responsible for managing user credentials and identity; Service Provider (SP): The system that provides a service to the user and relies on the Identity Provider to authenticate the user, receives SAML assertions from the IdP to grant access to resources. The library `cie-aspnetcorerefers` to the second entity, i.e. the SP, and implements the validation logic of the SAML assertions present within the SAML response . The following is a summary diagram of an authentication flow via SAML: 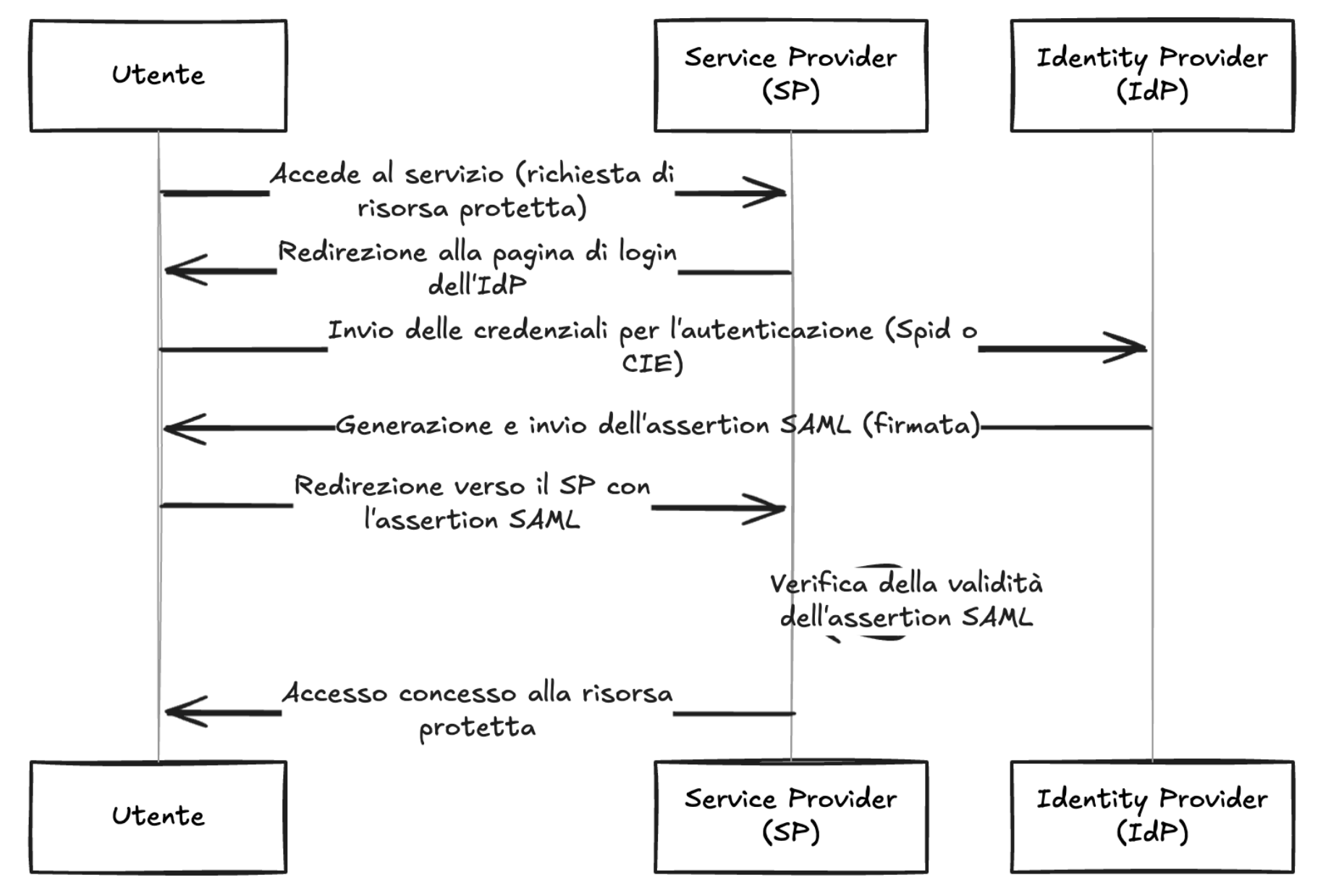 As shown in the diagram, the IdP, after verifying the user's credentials, generates a signed SAML response, this is propagated to the SP by the use...
### Description Authentication using Spid and CIE is based on the SAML2 standard which provides for two entities: Identity Provider (IdP): the system that authenticates users and provides identity information ( SAML assertions ) to the Service Provider, essentially, it is responsible for managing user credentials and identity; Service Provider (SP): The system that provides a service to the user and relies on the Identity Provider to authenticate the user, receives SAML assertions from the IdP to grant access to resources. The library `spid-aspnetcorerefers` to the second entity, i.e. the SP, and implements the validation logic of the SAML assertions present within the SAML response . The following is a summary diagram of an authentication flow via SAML:  As shown in the diagram, the IdP, after verifying the user's credentials, generates a signed SAML response, this is propagated to the SP by the us...
Microsoft is warning the modular and potentially wormable Apple-focused infostealer boasts new capabilities for obfuscation, persistence, and infection, and could lead to a supply chain attack.
Carding -- the underground business of stealing, selling and swiping stolen payment card data -- has long been the dominion of Russia-based hackers. Happily, the broad deployment of more secure chip-based payment cards in the United States has weakened the carding market. But a flurry of innovation from cybercrime groups in China is breathing new life into the carding industry, by turning phished card data into mobile wallets that can be used online and at main street stores.
New episode “In The Trend of VM” (#11): vulnerabilities that became trending in December and the final report on trending vulnerabilities for 2024. I made this episode exclusively for the Telegram channel @avleonovcom “Vulnerability Management and More”. 😉 📹 Video on YouTube, LinkedIn🗞 Post on Habr (rus)🗒 Digest on the PT website Content: 🔻 00:00 […]
The New Snake Keylogger variant targets Windows users via phishing emails, using AutoIt for stealth. Learn how it…
Cybersecurity researchers are alerting to a new campaign that leverages web injects to deliver a new Apple macOS malware known as FrigidStealer. The activity has been attributed to a previously undocumented threat actor known as TA2727, with the information stealers for other platforms such as Windows (Lumma Stealer or DeerStealer) and Android (Marcher). TA2727 is a "threat actor that uses fake
Two Estonian nationals plead guilty to a $577M cryptocurrency Ponzi scheme through HashFlare, defrauding hundreds of thousands globally.…