Tag
#web
### Summary The `email` field in phpMyFAQ's user control panel page is vulnerable to stored XSS attacks due to the inadequacy of PHP's `FILTER_VALIDATE_EMAIL` function, which only validates the email format, not its content. This vulnerability enables an attacker to execute arbitrary client-side JavaScript within the context of another user's phpMyFAQ session. ### Details Despite using PHP's `FILTER_VALIDATE_EMAIL` function, the email field does not adequately validate the content of the email address. This means that malicious input, such as JavaScript code, can be accepted and stored in the database without being detected. When the stored data is retrieved and displayed on web pages, it is not properly sanitized to remove or neutralize any potentially harmful content, such as JavaScript code which leads to Stored XSS. ### PoC 1. Login as any user, go to the user control panel, change email to any valid email and intercept the request. 2. Modify the request’s email parameter to t...
### Summary The category image upload function in phpmyfaq is vulnerable to manipulation of the `Content-type` and `lang` parameters, allowing attackers to upload malicious files with a .php extension, potentially leading to remote code execution (RCE) on the system. ### Details In the file upload function of the category image, the `Content-type` can be manipulated to return an empty string for the extension and the `lang` parameter can be set to `.php.` to allow an attacker to save a file as `.PHP`. This allows the uploading of web shells which could lead to RCE on phpmyfaq. ### PoC 1. Generate a fake .GIF file that contains a php command using the tool `gifsicle` a. Cmd: `gifsicle < test1.gif --comment "<?php system('whoami'); ?>" > output.php.gif` 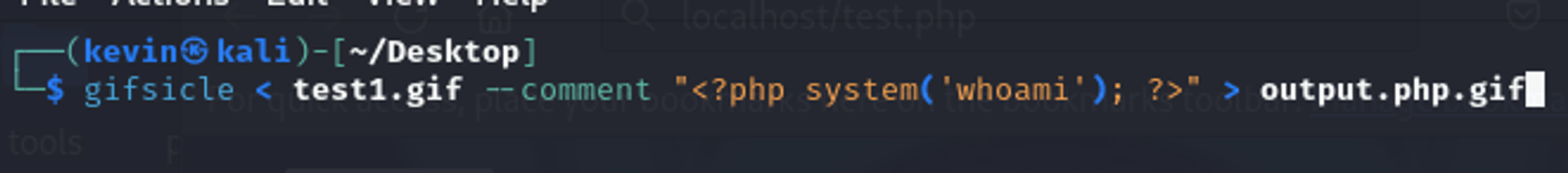 b. The contents of the file should look like this:  2. Verify the HTML injection by viewing the FAQ itself, “All categories” → “CategoryName” → ”QuestionName”. 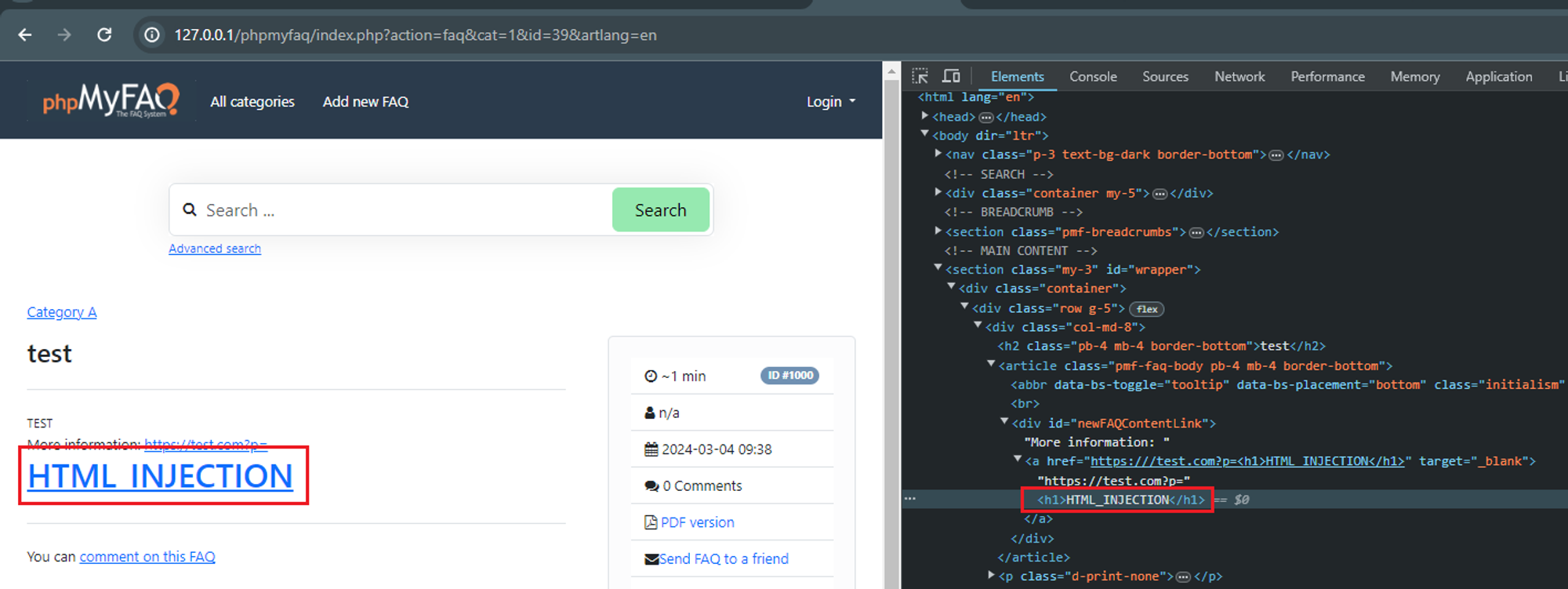 ### Impact Attackers can manipulate the appearance and functionality of web pages by injecting malicious HTML code. This can lead to various undesirable outcomes, such as defacing the website, redirecting users to malicious sites, or alte...
### Summary A SQL injection vulnerability has been discovered in the the "Add News" functionality due to improper escaping of the email address. This allows any authenticated user with the rights to add/edit FAQ news to exploit this vulnerability to exfiltrate data, take over accounts and in some cases, even achieve RCE. ### Details The vulnerable field lies in the `authorEmail` field which uses PHP's `FILTER_VALIDATE_EMAIL` filter. This filter is insufficient in protecting against SQL injection attacks and should still be properly escaped. However, in this version of phpMyFAQ (3.2.5), this field is not escaped properly can be used together with other fields to fully exploit the SQL injection vulnerability. ### PoCs 4 PoCs are demonstrated here to illustrate the potential impacts. #### PoC 1 - Postgres Time Based SQLi 1. Login as admin or any user with the rights to view and save news. 2. Navigate to "../phpmyfaq/admin/?action=news", click on "Add news", fill in some data, send and...
## Summary A security vulnerability exists in oneuptime's local storage handling, where a regular user can escalate privileges by modifying the `is_master_admin` key to `true`. This allows unauthorized access to administrative functionalities. ## Details The vulnerability lies in the improper validation of client-side stored data within the web application. Specifically, the `is_master_admin` key, stored in the local storage of the browser, can be manipulated by an attacker. By changing this key from false to true, the application grants administrative privileges to the user, without proper server-side validation. ## POC (I am using Firefox Developer to demonstrate this vulnerability) Log in as a normal user. Open developer tools (hit F12), click Storage, then Local Storage. Modify the `is_master_admin` key from `false` to `true`. ## Impact This vulnerability represents a high security risk as it allows any authenticated user to gain administrative privileges through client-side ma...
### Summary There is a Path Traversal vulnerability in Attachments that allows attackers with admin rights to upload malicious files to other locations of the web root. ### PoC 1. In settings, the attachment location is vulnerable to path traversal and can be set to e.g ..\hacked 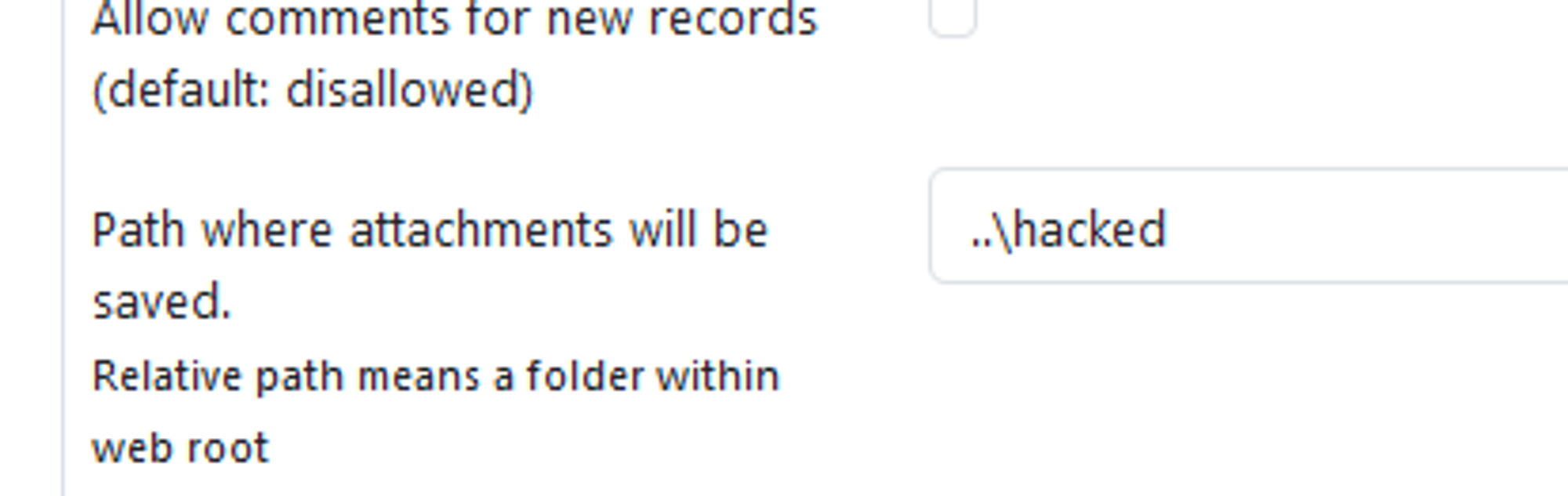 2. When the above is set, attachments files are now uploaded to e.g C:\Apps\XAMPP\htdocs\hacked instead of C:\Apps\XAMPP\htdocs\phpmyfaq\attachments 3. Verify this by uploading an attachment and see that the "hacked" directory is now created in the web root folder with the attachment file inside. 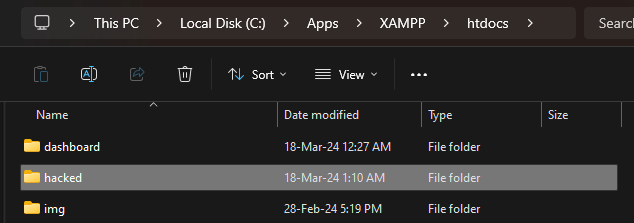 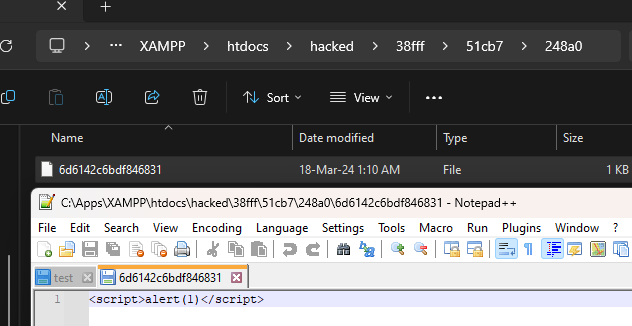 ### Impact Attackers can potentially upload malicious files outside the specified directory.
By Waqas Another day, another popular dark web marketplace bites the dust! This is a post from HackRead.com Read the original post: International Sting Takes Down Major Dark Web Marketplace “Nemesis Market”
By Deeba Ahmed New Dark Web Tool GEOBOX, sold for $700 on Telegram and underground forums, hijacks Raspberry Pi, allowing cybercriminals to fake locations and evade detection. This is a post from HackRead.com Read the original post: New GEOBOX Tool Hijacks Raspberry Pi, Lets Hackers Fake Location
A list of topics we covered in the week of March 18 to March 24 of 2024
Versions of the package web3-utils before 4.2.1 are vulnerable to Prototype Pollution via the utility functions format and mergeDeep, due to insecure recursive merge. An attacker can manipulate an object's prototype, potentially leading to the alteration of the behavior of all objects inheriting from the affected prototype by passing specially crafted input to these functions.