Tag
#git
Centreon updateGroups SQL Injection Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Centreon. Authentication is required to exploit this vulnerability. The specific flaw exists within the updateGroups function. The issue results from the lack of proper validation of a user-supplied string before using it to construct SQL queries. An attacker can leverage this vulnerability to execute code in the context of the service account. Was ZDI-CAN-22295.
Centreon updateDirectory SQL Injection Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Centreon. Authentication is required to exploit this vulnerability. The specific flaw exists within the updateDirectory function. The issue results from the lack of proper validation of a user-supplied string before using it to construct SQL queries. An attacker can leverage this vulnerability to execute code in the context of the service account. Was ZDI-CAN-22294.
Had a Microsoft developer not spotted the malware when he did, the outcome could have been much worse.
From ransomware to LOTL attacks, the top threats your educational institution needs to be aware of in 2024.
### Impact Versions from 1.2.0 to 1.3.1 of Astro-Shield allow to bypass the allow-lists for cross-origin resources by introducing valid `integrity` attributes to the injected code. This implies that the injected SRI hash would be added to the generated CSP header, which would lead the browser to believe that the injected resource is legit. To exploit this vulnerability, the attacker needs to first inject code into the rendered pages by exploiting other not-related potential vulnerabilities. ### Patches Version [1.3.2](https://github.com/kindspells/astro-shield/releases/tag/1.3.2) provides a patch. ### Workarounds - To not use the middleware functionality of Astro-Shield. - To use the middleware functionality of Astro-Shield ONLY for content that cannot be controlled in any way by external users. ### References _Are there any links users can visit to find out more?_
### Summary Piccolo's admin panel provides the ability to upload media files and view them within the admin panel. If SVG is an allowed file type for upload; the default; an attacker can upload an SVG which when loaded under certain contexts allows for arbitrary access to the admin page. This access allows the following actions for example: - The ability for an attacker to gain access to all data stored within the admin page - The ability for an attacker to make any action within the admin page such as creating, modifying or deleting table records As the SVG is executed from the context of an authenticated admin session, any actions they may be able to make can be made by the attacker. *N.b. The relevant session cookies are inaccessible from JavaScript due to httponly being set so all exploits must be present within the SVG file* ### PoC _Complete instructions, including specific configuration details, to reproduce the vulnerability._ Currently, this requires the ability for a ...
### Summary The Casa OS Login page has disclosed the username enumeration vulnerability in the login page which was patched in `CasaOS v0.4.7`. ### Details It is observed that the attacker can enumerate the CasaOS username using the application response. If the username is incorrect the application gives the error "**User does not exist**" with success code "**10006**", If the password is incorrect the application gives the error "**User does not exist or password is invalid**" with success code "**10013**". ### PoC 1. If the Username is invalid application gives "User does not exist" with success code "**10006**". 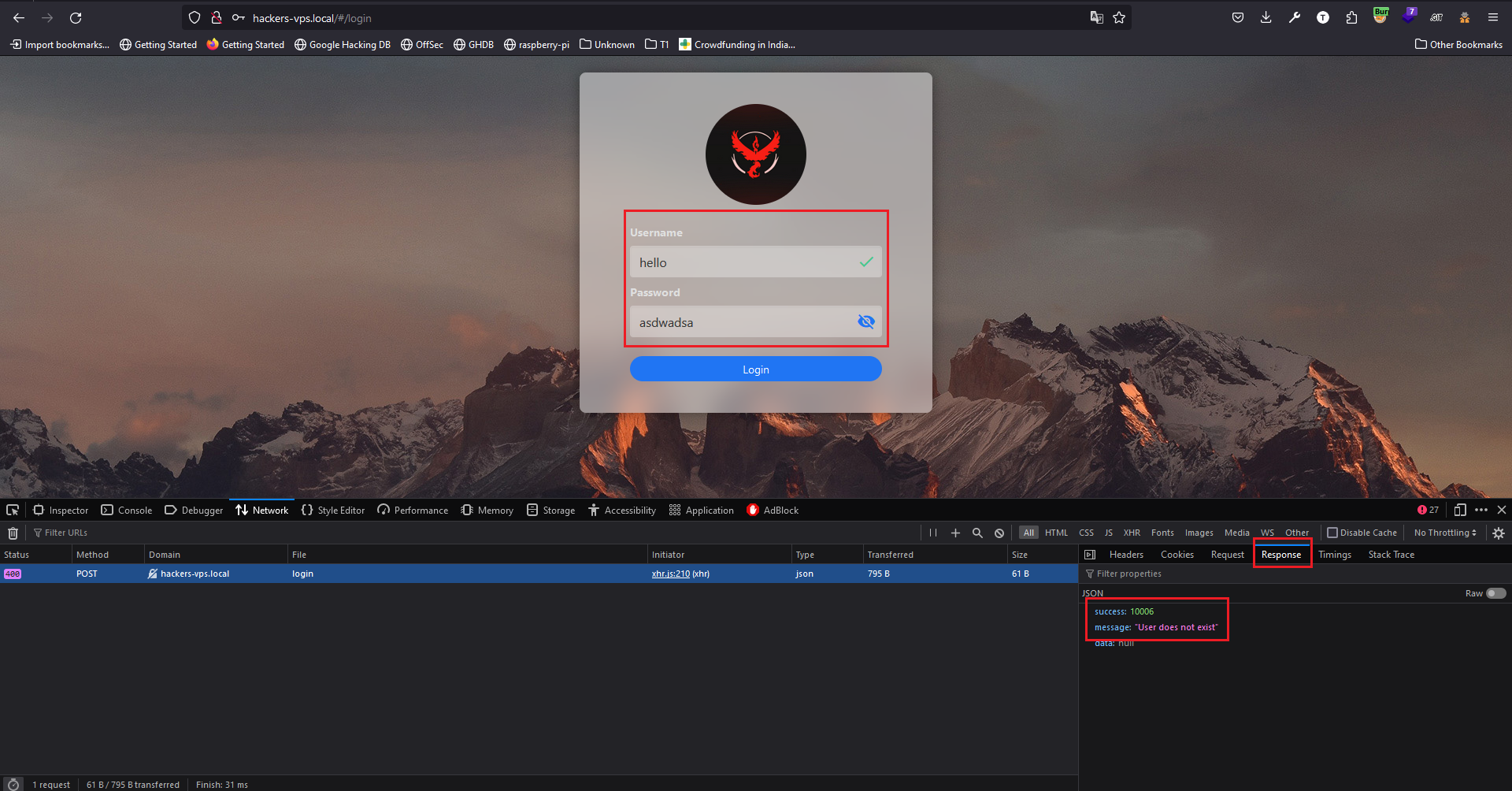 2. If the Password is invalid application gives "**User does not exist or password is invalid**" with success code "**10013**". 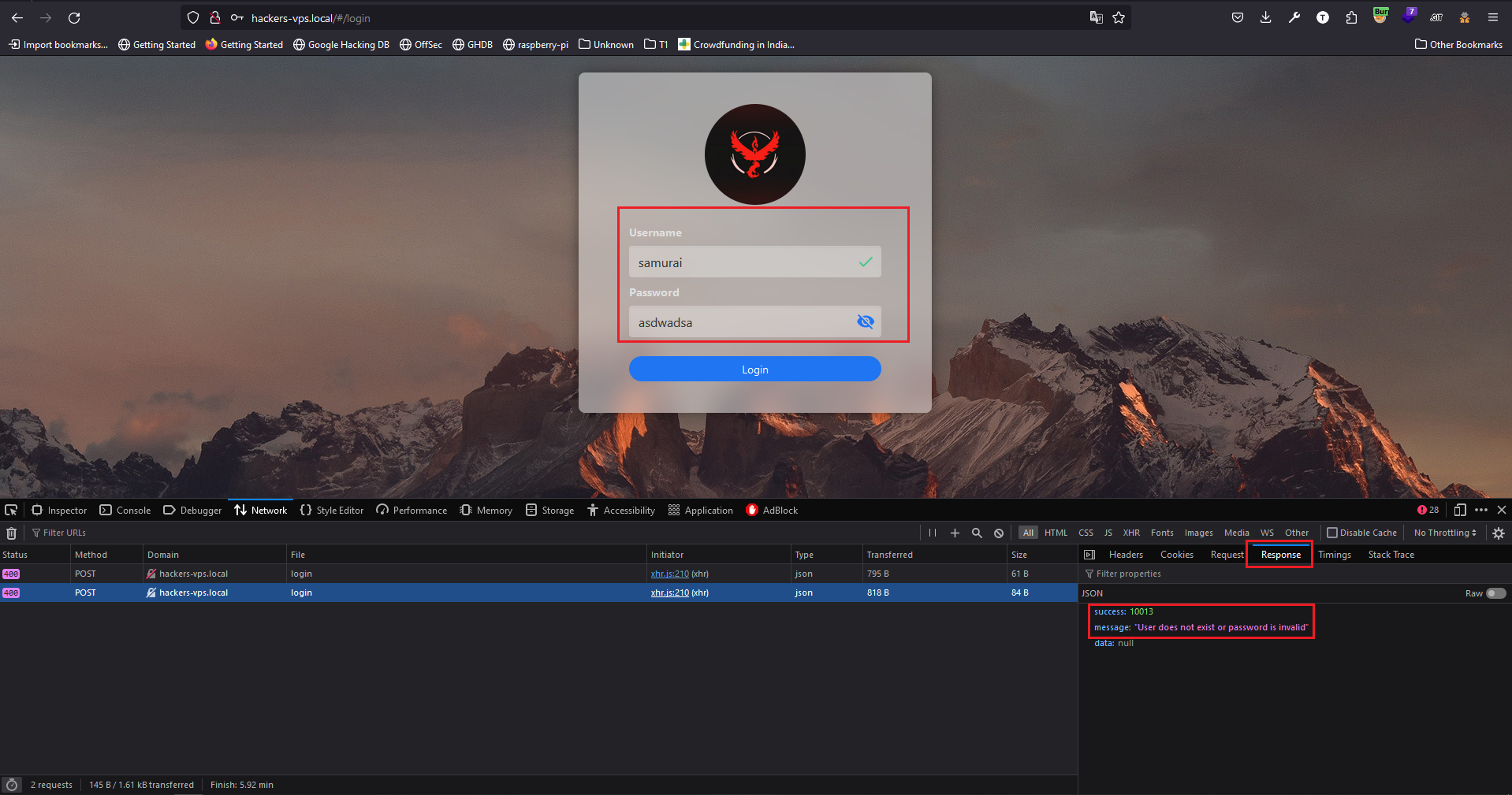 ### Impact Using...
ARIS: Business Process Management version 10.0.21.0 suffers from a persistent cross site scripting vulnerability.
Gibbon version 26.0.00 suffers from a server-side template injection vulnerability that allows for remote code execution.
Millions lost internet service after three cables in the Red Sea were damaged. Houthi rebels deny targeting the cables, but their missile attack on a cargo ship, left adrift for months, is likely to blame.