Tag
#java
Debian Linux Security Advisory 5672-1 - Several vulnerabilities have been discovered in the OpenJDK Java runtime, which may result in denial of service or information disclosure.
Debian Linux Security Advisory 5671-1 - Several vulnerabilities have been discovered in the OpenJDK Java runtime, which may result in denial of service or information disclosure.
The infamous Russian threat actor has created a custom tool called GooseEgg to exploit CVE-2022-38028 in cyber-espionage attacks against targets in Ukraine, Western Europe, and North America.
Talos also discovered a new PowerShell command-line argument embedded in the LNK file to bypass anti-virus products and download the final payload into the victims’ host.
The head of counterintelligence for a division of the Russian Federal Security Service (FSB) was sentenced last week to nine years in a penal colony for accepting a USD $1.7 million bribe to ignore the activities of a prolific Russian cybercrime group that hacked thousands of e-commerce websites. The protection scheme was exposed in 2022 when Russian authorities arrested six members of the group, which sold millions of stolen payment cards at flashy online shops like Trump's Dumps.
### Observations The Hoppscotch desktop app takes multiple precautions to be secure against arbitrary JavaScript and system command execution. It does not render user-controlled HTML or Markdown, uses Tauri instead of Electron, and sandboxes pre-request scripts with a simple yet secure implementation using web workers. Unfortunately, web workers are not available in a pure Node.js application like Hoppscotch CLI. That is why the [@hoppscotch/js-sandbox](https://github.com/hoppscotch/hoppscotch/tree/main/packages/hoppscotch-js-sandbox) package also provides a Javascript sandbox that uses the Node.js `vm` module. However, the `vm` module is not safe for sandboxing untrusted Javascript code, as stated [in the documentation](https://nodejs.org/api/vm.html#vm-executing-javascript). This is because [code inside the vm context can break out](https://thegoodhacker.com/posts/the-unsecure-node-vm-module/) if it can get a hold of any reference to an object created outside of the vm. In the cas...
### Summary There is improper sanitization on Service template name which is reflecting in delete button onclick event. This value can be modified and crafted as any other javascript code. ### Vulnerable Code https://github.com/librenms/librenms/blob/a61c11db7e8ef6a437ab55741658be2be7d14d34/app/Http/Controllers/ServiceTemplateController.php#L67C23-L67C23 Above is vulnerable code line which needs to be properly sanitized ### PoC 1. Go to /services/templates 2. Enter name as `testing', '14', 'http://172.105.62.194:8000/services/templates/14');alert(1);//` 3. Submit it and try to delete it, you will see popup If you inspect element on delete button, you will notice this:- <img width="748" alt="Screenshot 2023-11-23 at 9 30 24 PM" src="https://user-images.githubusercontent.com/31764504/285260018-7672a93d-e29b-4444-8057-e6ffcb8dabfc.png"> ### Impact Cross site scripting can lead to cookie stealing or an attacker can execute any other feature using this feature.
### Summary when jadx parses a resource file, there is an escape problem with the style file, which can overwrite other files in the directory when saving the decompile result. Although I don't think this vulnerability realizes path traversal in the true sense of the word , I reported it anyway ### Details I see that getResAlias does something with the filename. ```java private String getResAlias(int resRef, String origKeyName, @Nullable FieldNode constField) { ``` but type style will return the original filename directly. 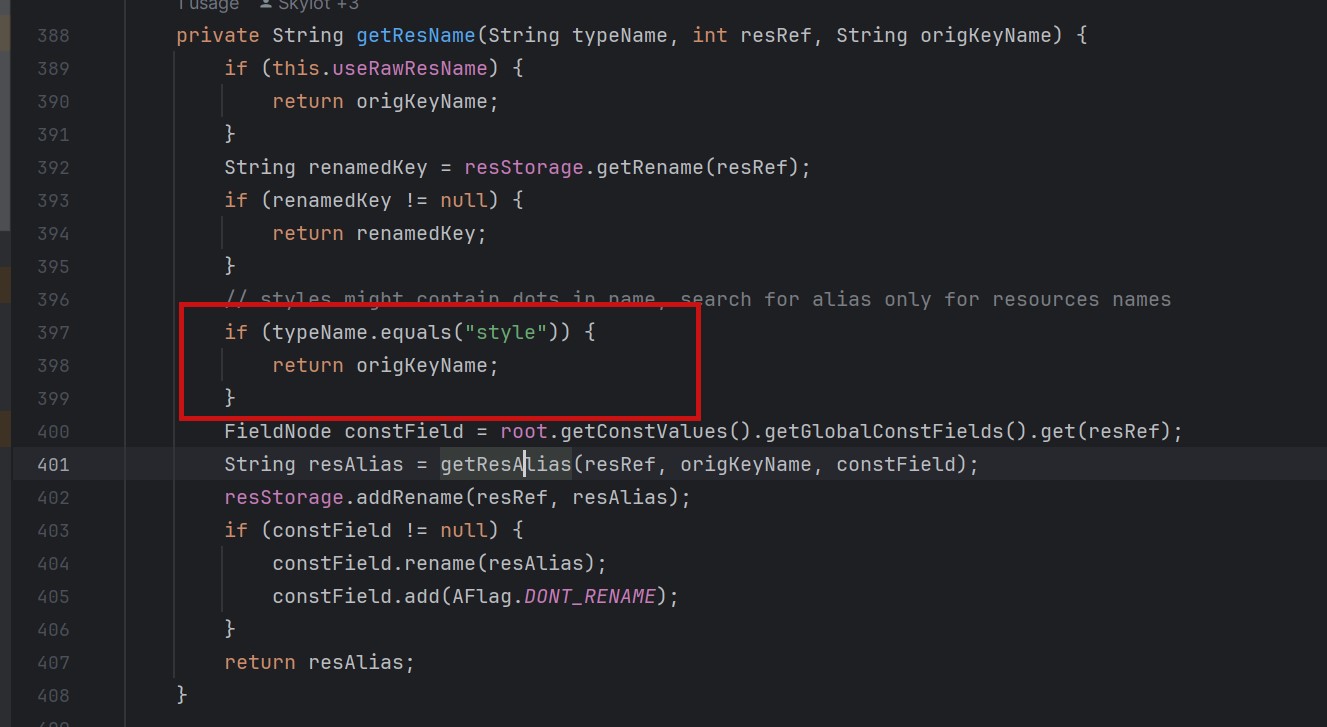 so our goal is to take a malicious file that was originally of type raw, modify its type to style, trick jadx into #### step1 create an android project using androidstudio and create a raw folder with the name attack_file_sayhiiiiiiiiiiiii, it doesn't matter what the content is! 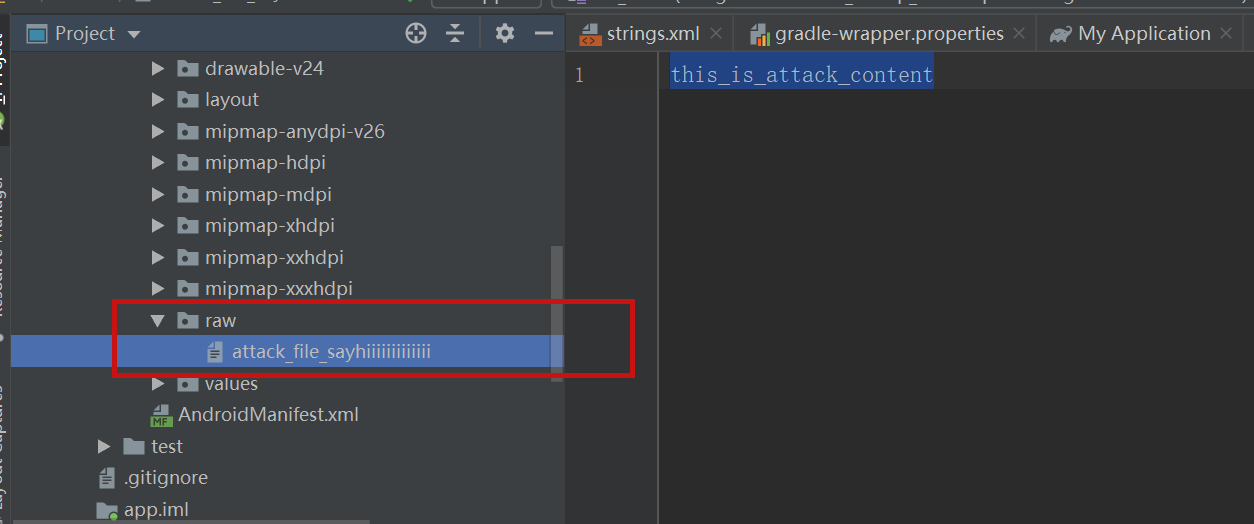 generate an initial APK #### s...
### Impact We have identified a local privilege escalation vulnerability in Ant Media Server which allows any unprivileged operating system user account to escalate privileges to the root user account on the system. This vulnerability arises from Ant Media Server running with Java Management Extensions (JMX) enabled and authentication disabled on localhost on port 5599/TCP. This vulnerability is nearly identical to the local privilege escalation vulnerability CVE-2023-26269 identified in Apache James. Any unprivileged operating system user can connect to the JMX service running on port 5599/TCP on localhost and leverage the MLet Bean within JMX to load a remote MBean from an attacker-controlled server. This allows an attacker to execute arbitrary code within the Java process run by Ant Media Server and execute code within the context of the “antmedia” service account on the system. ### Patches 2.9.0 ### Workarounds Remote the following parameters from antmedia.service file ```-Dcom....
RCE-Remote Command Execution vulnerability in Apache HugeGraph-Server.This issue affects Apache HugeGraph-Server: from 1.0.0 before 1.3.0 in Java8 & Java11 Users are recommended to upgrade to version 1.3.0 with Java11 & enable the Auth system, which fixes the issue.