Tag
#php
Kruxton version 1.0 suffers from a remote shell upload vulnerability.
WBCE version 1.6.0 suffers from a remote SQL injection vulnerability.
AMPLE BILLS version 0.1 suffers from a remote SQL injection vulnerability.
Moodle version 3.10.1 suffers from a remote time-based SQL injection vulnerability.
By Deeba Ahmed Critical 'BatBadBut' Flaw in Windows Lets Hackers Inject Commands (Patch Now!) This is a post from HackRead.com Read the original post: Windows Apps Vulnerable to Command Injection via “BatBadBut” Flaw
The Dusk plugin provides some special routes as part of its testing framework to allow a browser environment (such as headless Chrome) to act as a user in the Backend or User plugin without having to go through authentication. This route is `[[URL]]/_dusk/login/[[USER ID]]/[[MANAGER]]` - where `[[URL]]` is the base URL of the site, `[[USER ID]]` is the ID of the user account and `[[MANAGER]]` is the authentication manager (either `backend` for Backend, or `user` for the User plugin). If a configuration of a site using the Dusk plugin is set up in such a way that the Dusk plugin is available publicly and the test cases in Dusk are run with live data, this route may potentially be used to gain access to any user account in either the Backend or User plugin without authentication. As indicated in the [README](https://github.com/wintercms/wn-dusk-plugin/blob/main/README.md), this plugin should only be used in development and should *NOT* be used in a production instance. It is specifical...
### Summary Timber is vulnerable to [PHAR deserialization](https://portswigger.net/web-security/deserialization/exploiting#phar-deserialization) due to a lack of checking the input before passing it into the` file_exists()` function. If an attacker can upload files of any type to the server, he can pass in the `phar://` protocol to unserialize the uploaded file and instantiate arbitrary PHP objects. This can lead to remote code execution especially when Timber is used with frameworks with documented POP chains like Wordpress/ vulnerable developer code. ### Details The vulnerability lies in the run function within the `toJpg.php` file. The two parameters passed into it are not checked or sanitized, hence an attacker could potentially inject malicious input leading to Deserialization of Untrusted Data, allowing for remote code execution: 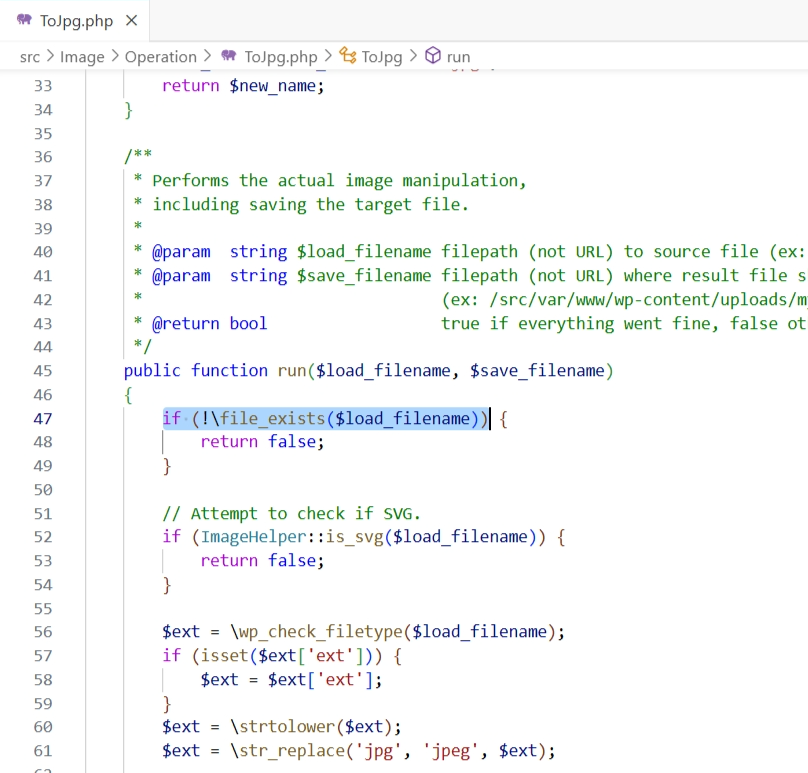 ### PoC Setup the following code in `/var/www/html`: `...
WordPress Playlist for Youtube plugin version 1.32 suffers from a persistent cross site scripting vulnerability.
GUnet OpenEclass E-learning platform version 3.15 suffers from an unrestricted file upload vulnerability in certbadge.php that allows for remote command execution.
Joomla SP Page Builder component version 5.2.7 suffers from a remote SQL injection vulnerability.