Tag
#rce
View CSAF 1. EXECUTIVE SUMMARY CVSS v3 10.0 ATTENTION: Exploitable remotely/low attack complexity/public exploits are available Vendor: Nice Equipment: Linear eMerge E3-Series Vulnerabilities: Path traversal, Cross-site scripting, OS command injection, Unrestricted Upload of File with Dangerous Type, Incorrect Authorization, Exposure of Sensitive Information to an Authorized Actor, Insufficiently Protected Credentials, Use of Hard-coded Credentials, Cross-site Request Forgery, Out-of-bounds Write 2. RISK EVALUATION Successful exploitation of these vulnerabilities could allow a remote attacker to gain full system access. 3. TECHNICAL DETAILS 3.1 AFFECTED PRODUCTS The following versions of Nice Linear eMerge E3-Series are affected: Linear eMerge E3-Series: versions 1.00-06 and prior 3.2 Vulnerability Overview 3.2.1 IMPROPER LIMITATION OF A PATHNAME TO A RESTRICTED DIRECTORY (‘PATH TRAVERSAL') CWE-22 Nice Linear eMerge E3-Series versions 1.00-06 and prior are vulnerable to path traversal....
### Impact In JSONata versions `>= 1.4.0, < 1.8.7` and `>= 2.0.0, < 2.0.4`, a malicious expression can use the [transform operator](https://docs.jsonata.org/other-operators#-------transform) to override properties on the `Object` constructor and prototype. This may lead to denial of service, remote code execution or other unexpected behavior in applications that evaluate user-provided JSONata expressions. ### Patch This issue has been fixed in JSONata versions `>= 1.8.7` and `>= 2.0.4`. Applications that evaluate user-provided expressions should update ASAP to prevent exploitation. The following patch can be applied if updating is not possible. ```patch --- a/src/jsonata.js +++ b/src/jsonata.js @@ -1293,6 +1293,13 @@ var jsonata = (function() { } for(var ii = 0; ii < matches.length; ii++) { var match = matches[ii]; + if (match && (match.isPrototypeOf(result) || match instanceof Object.constructor)) { + ...
Wallos versions prior to 1.11.2 suffer from a remote shell upload vulnerability.
Gentoo Linux Security Advisory 202403-1 - A vulnerability has been discovered in Tox which may lead to remote code execution. Versions greater than or equal to 0.2.13 are affected.
Petrol Pump Management System version 1.0 suffers from a remote shell upload vulnerability. This is a variant vector of attack in comparison to the original discovery attributed to SoSPiro in February of 2024.
GL.iNet AR300M versions 3.216 and below suffer from an OpenVPN client related remote code execution vulnerability.
GL.iNet AR300M versions 4.3.7 and below suffer from an OpenVPN client related remote code execution vulnerability.
LangChain through 0.1.10 allows ../ directory traversal by an actor who is able to control the final part of the path parameter in a load_chain call. This bypasses the intended behavior of loading configurations only from the hwchase17/langchain-hub GitHub repository. The outcome can be disclosure of an API key for a large language model online service, or remote code execution.
### Summary Security misconfiguration in edit configuration file API in dashboard component of ESPHome version 2023.12.9 (command line installation) allows authenticated remote attackers to read and write arbitrary files under the configuration directory rendering remote code execution possible. ### Details It is possible to abuse this path traversal vulnerability both in command line installation and Home Assistant add-on, but it is possible to read and write files only under the configuration directory. The vulnerability is present and exploitable in the command line installation, but it was not possible to confirm an impact in the home assistant add-on version. ### PoC <img width="482" alt="/edit?configuration=/config/.esphome/esphome.json" src="https://github.com/esphome/esphome/assets/115887876/d2da3180-976e-4bed-b4b9-35ac960a7fb4"> <br/> <img width="344" alt="/edit?configuration=/config/.esphome/build/test01/src/main.cpp (firmware for board named test01)" src="https://github...
### Impact Previously, budibase used a library called `vm2` for code execution inside the Budibase builder and apps, such as the UI below for configuring bindings in the design section. 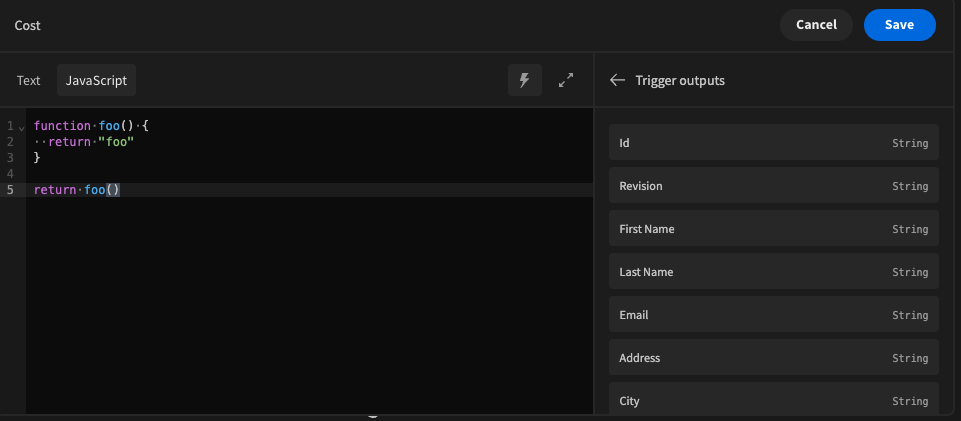 Due to a [vulnerability in vm2](https://github.com/advisories/GHSA-cchq-frgv-rjh5), any environment that executed the code server side (automations and column formulas) was susceptible to this vulnerability, allowing users to escape the sandbox provided by `vm2`, and to expose server side variables such as `process.env`. It's recommended by the authors of `vm2` themselves that you should move to another solution for remote JS execution due to this vulnerability. ### Patches We moved our entire JS sandbox infrastructure over to `isolated-vm`, a much more secure and recommended library for remote code execution in 2.20.0. This also comes with a performance benefit in the way w...