Tag
#sql
### Impact Backoffice users can execute arbitrary SQL. ### Explanation of the vulnerability A Backoffice user can modify requests to a particular API endpoint to include SQL which will be executed by the server. ### Affected versions All versions ### Patches Workflow 10.3.9, 12.2.6, 13.0.6, Plumber 10.1.2 ### References [Upgrading Umbraco Workflow](https://docs.umbraco.com/umbraco-workflow/upgrading/upgrading)
Red Hat Security Advisory 2024-1999-03 - An update for postgresql-jdbc is now available for Red Hat Enterprise Linux 9.0 Extended Update Support.
SQL injection vulnerability in Zend Framework before 1.12.9, 2.2.x before 2.2.8, and 2.3.x before 2.3.3, when using the sqlsrv PHP extension, allows remote attackers to execute arbitrary SQL commands via a null byte.
A remote SQL injection vulnerability exists in FortiNet FortiClient EMS (Endpoint Management Server) versions 7.2.0 through 7.2.2 and 7.0.1 through 7.0.10. FortiClient EMS serves as an endpoint management solution tailored for enterprises, offering a centralized platform for overseeing enrolled endpoints. The SQL injection vulnerability is due to user controller strings which can be sent directly into database queries. FcmDaemon.exe is the main service responsible for communicating with enrolled clients. By default it listens on port 8013 and communicates with FCTDas.exe which is responsible for translating requests and sending them to the database. In the message header of a specific request sent between the two services, the FCTUID parameter is vulnerable to SQL injection. It can be used to enable the xp_cmdshell which can then be used to obtain unauthenticated remote code execution in the context of NT AUTHORITY\SYSTEM. Upgrading to either 7.2.3, 7.0.11 or above is recommended by Fo...
Versions of the package mysql2 before 3.9.7 are vulnerable to Arbitrary Code Injection due to improper sanitization of the timezone parameter in the readCodeFor function by calling a native MySQL Server date/time function.
### Summary Using a version of `sqlparse` that has a security vulnerability and no way to update in current version of dbt core. Snyk recommends using `sqlparse==0.5` but this causes a conflict with dbt. Snyk states the issues is a recursion error: `SNYK-PYTHON-SQLPARSE-6615674`. ### Details Dependency conflict error message: ```sh The conflict is caused by: The user requested sqlparse==0.5 dbt-core 1.7.10 depends on sqlparse<0.5 and >=0.2.3 ``` Resolution was to pin `sqlparse >=0.5.0, <0.6.0` in `dbt-core`, patched in 1.6.13 and 1.7.13. ### PoC From Snyk: ```python import sqlparse sqlparse.parse('[' * 10000 + ']' * 10000) ``` ### Impact Snyk classifies it as high 7.5/10. ### Patches The bug has been fixed in [dbt-core v1.6.13](https://github.com/dbt-labs/dbt-core/releases/tag/v1.6.13) and [dbt-core v1.7.13](https://github.com/dbt-labs/dbt-core/releases/tag/v1.7.13). ### Mitigations Bump `dbt-core` 1.6 and 1.7 dependencies to 1.6.13 and 1.7.13 respectively
### Summary Get a valid API token, make sure you can access api functions, then replace string on my PoC code, Test on offical OVA image, it's a old version 23.9.1, but this vulerable is also exists on latest version 24.2.0 ### Details in file `api_functions.php`, line 307 for function list_devices ```php $order = $request->get('order'); $type = $request->get('type'); $query = $request->get('query'); $param = []; if (empty($order)) { $order = 'hostname'; } if (stristr($order, ' desc') === false && stristr($order, ' asc') === false) { $order = 'd.`' . $order . '` ASC'; } /* ... */ $devices = []; $dev_query = "SELECT $select FROM `devices` AS d $join WHERE $sql GROUP BY d.`hostname` ORDER BY $order"; foreach (dbFetchRows($dev_query, $param) as $device) { ``` The "order" parameter is obtained from $request. After performing a string check, the value is directly incorporated into an SQL statement and concatenated, resulting in...
### Summary SQL injection vulnerability in POST /search/search=packages in LibreNMS 24.3.0 allows a user with global read privileges to execute SQL commands via the package parameter. ### Details There is a lack of hygiene of data coming from the user in line 83 of the file librenms/includes/html/pages/search/packages.inc.php 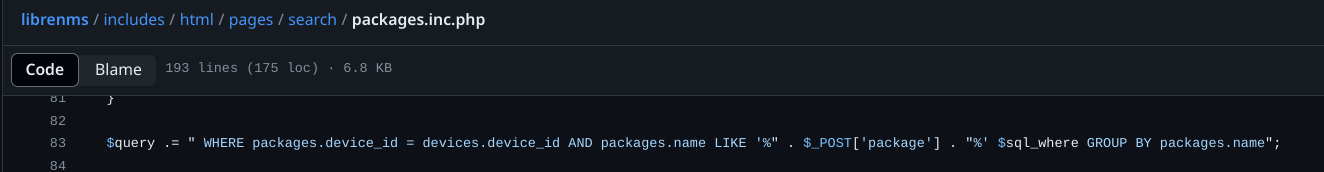 ### PoC https://doc.clickup.com/9013166444/p/h/8ckm0bc-53/16811991bb5fff6 ### Impact With this vulnerability, we can exploit a SQL injection time based vulnerability to extract all data from the database, such as administrator credentials
Users will need to download the latest version of Ivanti's Avalanche to apply fixes for all of the bugs.