Source
ghsa
## Summary Nokogiri v1.18.3 upgrades its dependency libxml2 to [v2.13.6](https://gitlab.gnome.org/GNOME/libxml2/-/releases/v2.13.6). libxml2 v2.13.6 addresses: - CVE-2025-24928 - described at https://gitlab.gnome.org/GNOME/libxml2/-/issues/847 - CVE-2024-56171 - described at https://gitlab.gnome.org/GNOME/libxml2/-/issues/828 ## Impact ### CVE-2025-24928 Stack-buffer overflow is possible when reporting DTD validation errors if the input contains a long (~3kb) QName prefix. ### CVE-2024-56171 Use-after-free is possible during validation against untrusted XML Schemas (.xsd) and, potentially, validation of untrusted documents against trusted Schemas if they make use of `xsd:keyref` in combination with recursively defined types that have additional identity constraints.
## Summary Problem: Potential man-in-the-middle attacks due to missing SSL certificate verification in the project codebase and used third-party libraries. ## Details In the past, `aiohttp-session`/`request` had the parameter `verify_ssl` to control SSL certificate verification. This was a boolean value. In `aiohttp` 3.0, this parameter was deprecated in favor of the `ssl` parameter. Only when `ssl` is set to `None` or provided with a correct configured SSL context the standard SSL certificate verification will happen. When migrating integrations in Home Assistant and libraries used by Home Assistant, in some cases the `verify_ssl` parameter value was just moved to the new `ssl` parameter. This resulted in these integrations and 3rd party libraries using `request.ssl = True`, which unintentionally turned off SSL certificate verification and opened up a man-in-the-middle attack vector. Example: https://github.com/home-assistant/core/blob/c4411914c2e906105b765c00af5740bd0880e946/hom...
### Description Authentication using Spid and CIE is based on the SAML2 standard which provides for two entities: Identity Provider (IdP): the system that authenticates users and provides identity information ( SAML assertions ) to the Service Provider, essentially, it is responsible for managing user credentials and identity; Service Provider (SP): The system that provides a service to the user and relies on the Identity Provider to authenticate the user, receives SAML assertions from the IdP to grant access to resources. The library `cie-aspnetcorerefers` to the second entity, i.e. the SP, and implements the validation logic of the SAML assertions present within the SAML response . The following is a summary diagram of an authentication flow via SAML: 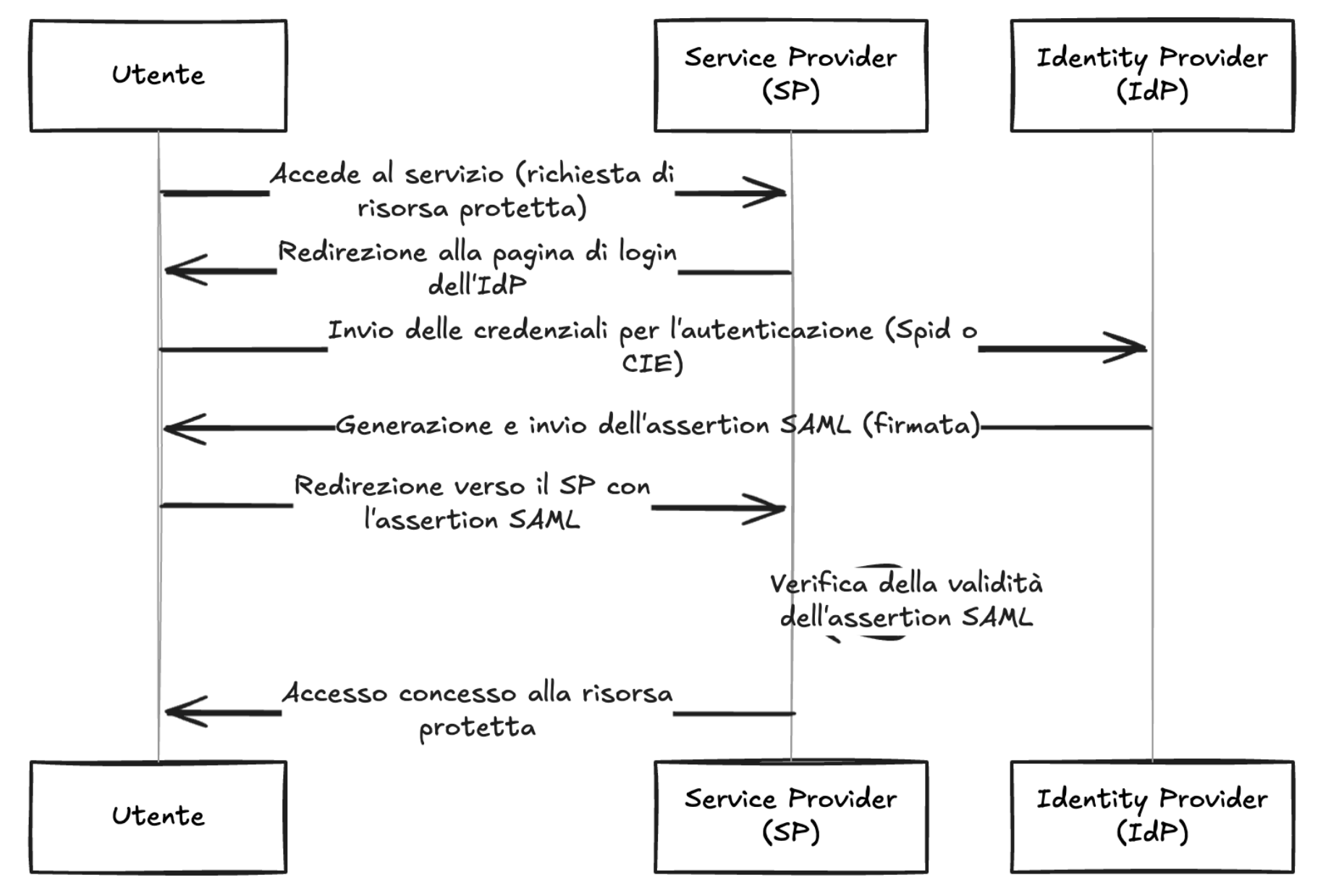 As shown in the diagram, the IdP, after verifying the user's credentials, generates a signed SAML response, this is propagated to the SP by the use...
### Description Authentication using Spid and CIE is based on the SAML2 standard which provides for two entities: Identity Provider (IdP): the system that authenticates users and provides identity information ( SAML assertions ) to the Service Provider, essentially, it is responsible for managing user credentials and identity; Service Provider (SP): The system that provides a service to the user and relies on the Identity Provider to authenticate the user, receives SAML assertions from the IdP to grant access to resources. The library `spid-aspnetcorerefers` to the second entity, i.e. the SP, and implements the validation logic of the SAML assertions present within the SAML response . The following is a summary diagram of an authentication flow via SAML:  As shown in the diagram, the IdP, after verifying the user's credentials, generates a signed SAML response, this is propagated to the SP by the us...
A vulnerability was found in Keycloak. This issue may allow a privileged attacker to use a malicious payload as the permission while creating items (Resource and Permissions) from the admin console, leading to a stored cross-site scripting (XSS) attack.
A flaw was found in the Keycloak organization feature, which allows the incorrect assignment of an organization to a user if their username or email matches the organization’s domain pattern. This issue occurs at the mapper level, leading to misrepresentation in tokens. If an application relies on these claims for authorization, it may incorrectly assume a user belongs to an organization they are not a member of, potentially granting unauthorized access or privileges.
Versions of the package jsonpath-plus before 10.3.0 are vulnerable to Remote Code Execution (RCE) due to improper input sanitization. An attacker can execute aribitrary code on the system by exploiting the unsafe default usage of eval='safe' mode. **Note:** This is caused by an incomplete fix for CVE-2024-21534.
### Impact The Keylime `registrar` implemented more strict type checking on version 7.12.0. As a result, when updated to version 7.12.0, the `registrar` will not accept the format of the data previously stored in the database by versions >= 7.8.0, raising an exception. This makes the Keylime `registrar` vulnerable to a Denial-of-Service attack in an update scenario, as an attacker could populate the `registrar` database by creating multiple valid agent registrations with different UUIDs while the version is still < 7.12.0. Then, when the Keylime `registrar` is updated to the 7.12.0 version, any query to the database matching any of the entries populated by the attacker will result in failure. ### Patches Users should upgrade to versions >= 7.12.1 ### Workarounds - Remove the registrar database and re-register all agents ### Credit Reported by: Anderson Toshiyuki Sasaki/@ansasaki Patched by: Anderson Toshiyuki Sasaki/@ansasaki
### Summary The regular expression `/<([^>]+)>; rel="deprecation"/` used to match the `link` header in HTTP responses is vulnerable to a ReDoS (Regular Expression Denial of Service) attack. This vulnerability arises due to the unbounded nature of the regex's matching behavior, which can lead to catastrophic backtracking when processing specially crafted input. An attacker could exploit this flaw by sending a malicious `link` header, resulting in excessive CPU usage and potentially causing the server to become unresponsive, impacting service availability. ### Details The vulnerability resides in the regular expression `/<([^>]+)>; rel="deprecation"/`, which is used to match the `link` header in HTTP responses. This regular expression captures content between angle brackets (`<>`) followed by `; rel="deprecation"`. However, the pattern is vulnerable to ReDoS (Regular Expression Denial of Service) attacks due to its susceptibility to catastrophic backtracking when processing malicious inp...
### Summary A Regular Expression Denial of Service (ReDoS) vulnerability exists in the processing of HTTP request headers. By sending an authorization header containing an excessively long sequence of spaces followed by a newline and "@", an attacker can exploit inefficient regular expression processing, leading to excessive resource consumption. This can significantly degrade server performance or cause a denial-of-service (DoS) condition, impacting availability. ### Details The issue occurs at [line 52](https://github.com/octokit/request-error.js/blob/main/src/index.ts) of iterator.ts in the @octokit/request-error repository. The vulnerability is caused by the use of an inefficient regular expression in the handling of the `authorization` header within the request processing logic: ```js authorization: options.request.headers.authorization.replace( / .*$/, " [REDACTED]" ) ``` The regular expression `/ .*$/` matches a space followed by any number of characters until the end of th...